Just-in-time user provisioning
With SSO enabled via SAML or OIDC, administrators can optionally enable just-in-time user provisioning. When enabled, administrators can provide a json configuration mapping a group on their SSO identity provider to a Tines team and role. Once setup, a user signing into Tines for the first time will automatically be placed in the designated team and role mapped to their SSO group in the configuration json without requiring an invitation to the tenant.
Note: A change to the just-in-time configuration will not update existing users' teams and roles unless Enhanced Just-in-time syncing is enabled (see below for details).
💡Note
To setup:
Configure your tenant to use SAML or OIDC for single sign-on
Enter a value for "SSO-group-based access", so that the user group information is available to Tines when a user logs in.
Select Just-in-time user provisioning in the User provisioning section.
Configure a group mapping that has at least one entry for
mappings, and optionallytenant_owners_groupsandtenant_permission. See the Automated user provisioning section for details about configuring mappings.
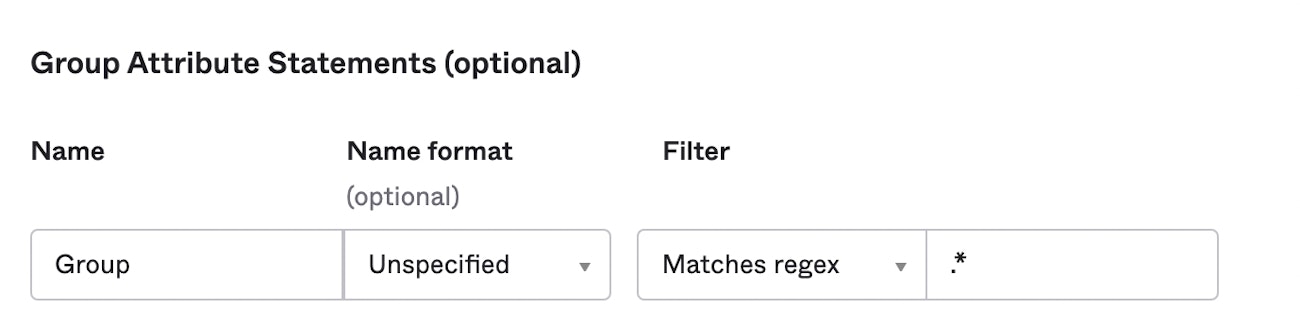
An example of a Group Attribute Statement configuration in Okta.
Optional Mappings
Optional: For a new user's first name, last name, and avatar to be automatically configured when signing on, the givenname, surname, and avatar attributes can be added to the SAML statement or OIDC claim.
🪄Tip
Enhanced Just-in-time syncing
As an addition to just-in-time user provisioning administrators can also enable 'Enhanced Just-in-time syncing'. This feature enables syncing of a users teams, case groups and roles from their IdP on every login.
Once this is enabled on a tenant, a users team memberships and roles are provisioned and synced in Tines to match changes made to resources on the Identity Provider. As a result, managing a user's team and role assignments via Tines will now be disabled.
❗️Important
To setup: (at /settings/authentication in your tenant)
Follow steps for configuration of JIT above. This feature is compatible with existing JIT configurations so current mappings will work.
Scroll down to the User provisioning section. Click on the Switch entitled "Enhanced just-in-time syncing".
Save
Now on each login a user's team and role assignments will be synced from their IdP settings.
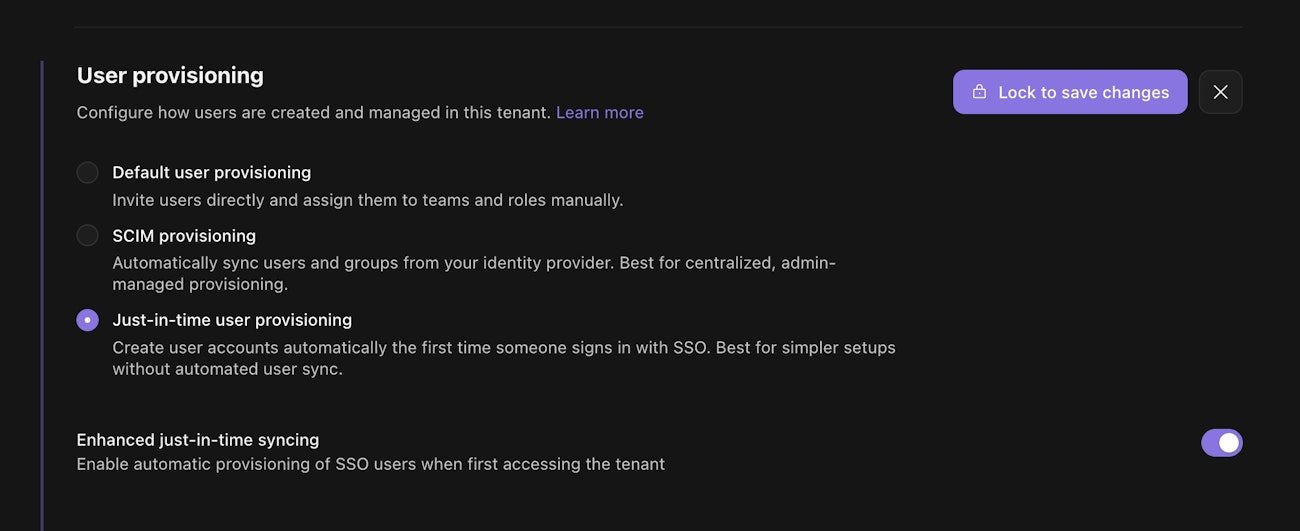
Authentication Settings configuration of enhanced JIT syncing.