Introduction
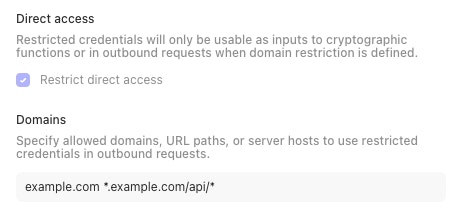
Domain restriction is used to enhance credential security. In order to use credentials in an outbound request, domain restriction must be defined.
Access
Domain restriction can only be changed by the credential creator, users with the 'Manage credentials' permission, which corresponds with the Team admin role, and tenant owners.
Supported restrictions
Domain restriction supports the following:
Multiple inputs: separate each input with a space
Wildcards: use a
*as a wildcard within any of the input types
The following input types are supported:
Domains:
Specify the domain of the API call URL that your credential will be used in.
Examples:
*.tines.comallows your credential to be used in any HTTP request to a URL with a domain that ends intines.comyour-domain.tines.comallows your credential to be used in any HTTP request to a URL with the domainyour-domain.tines.com
URL Paths
URL paths encompass the full URL rather than just the domain. By specifying a URL path, you can prevent usage of a credential within http or https requests. Additionally, you can further restrict credential usage to a particular part of an API.
Examples:
your-domain.tines.com/api/*/casesallows your credential to be used only within calls to the Tines API for cases. The wildcard allows support for v1 or v2 of the cases API.https://your-domain.tines.com/api/*allows your credential to be used within calls to the Tines API and further specifies requests must go to anhttpsendpoint.
Server Hosts
This is used within IMAP mode of the Receive Email action. Enter the server host used for your action to allow your credential to be used within the Receive Email action.
Special Cases
We recommend using caution when enabling credentials for the below cases.
Command over http: to use a credential with command over http, enter
command-over-httpRun script: to use a credential in a run script action, enter
run-script
Supported functions
Credentials that do not have a domain restriction defined will only be usable in functions that do not expose the credential value. See the allowed functions a credential can be used in below:
Legacy tenants
Tenants created before May 17, 2024 12:00 UTC can opt in to the above behavior via a tenant-wide setting Credential Access.
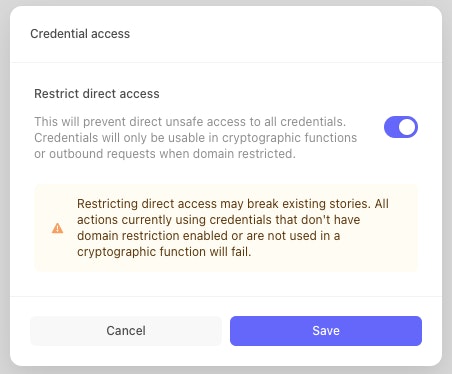
Before opting in at the tenant level, we strongly recommend enabling this behavior at the credential level to reduce the risk of story breakage. Checking the Restrict direct access box will restrict credential usage to only the supported function list and specified domains for the credential.
To view all restricted and unrestricted credentials, tenant owners can visit https://your-tenant-domain/credentials and filter for unrestricted credentials. We recommend using this as an additional check before turning on Restrict direct access at the tenant level. Learn more about viewing and managing tenant-wide credentials.
Once all credentials have Restrict direct access turned on, we strongly recommend enabling the tenant-wide setting, which will update your tenant to the non-legacy behavior described above, ensuring any new credentials created mandate defined domain restriction to be used in outbound requests.