Phishing
Cut through the noise, break free from false positives
Discover ways to automate investigation, remediation, escalation, and communication around your phishing response process.
Featured stories
Read forwarded phishing emails and attachments
Commonly organizations ask their users to forward phishing emails as .eml attachments to a phishing inbox. This technique shows how to read an email, any attachments, and any attachments that are also .eml files.
Tools: EmailRep



Analyze potential SMS phishing attacks and raise incidents in Jira
Receive screenshots of potential SMSishing attacks and extract URLs. These URLs are then analyzed using another Tines story before the report returns to the user. If the user responds to the attacker, an incident is raised on a true positive.
Tools: OCRSpace, OpenAI, PagerDuty
By Rajesh Kumar


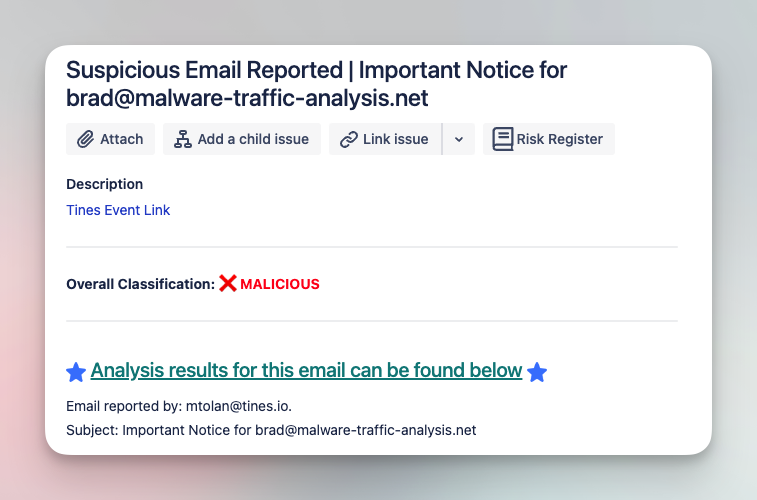
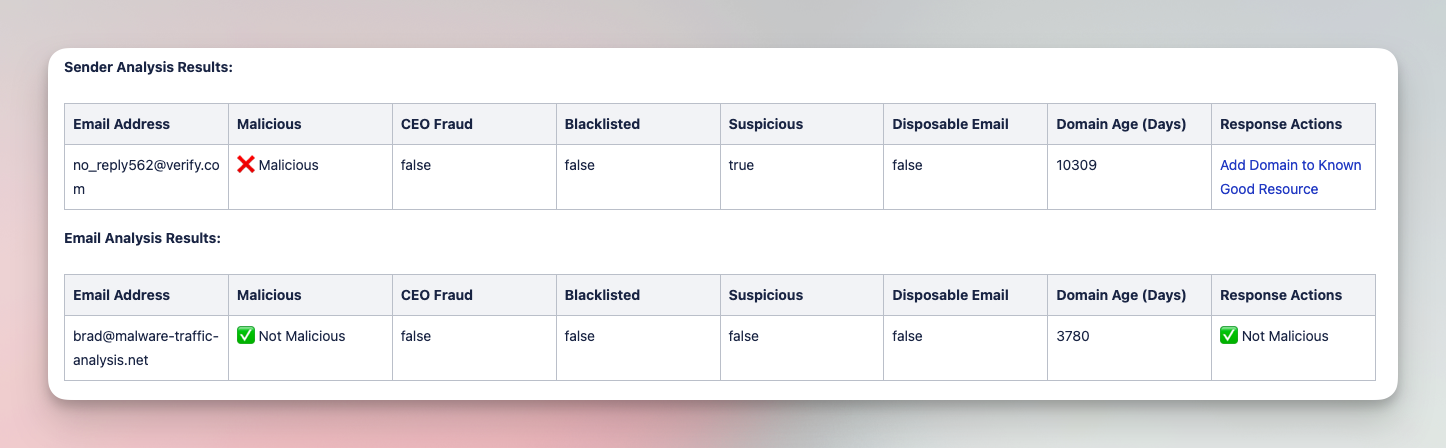
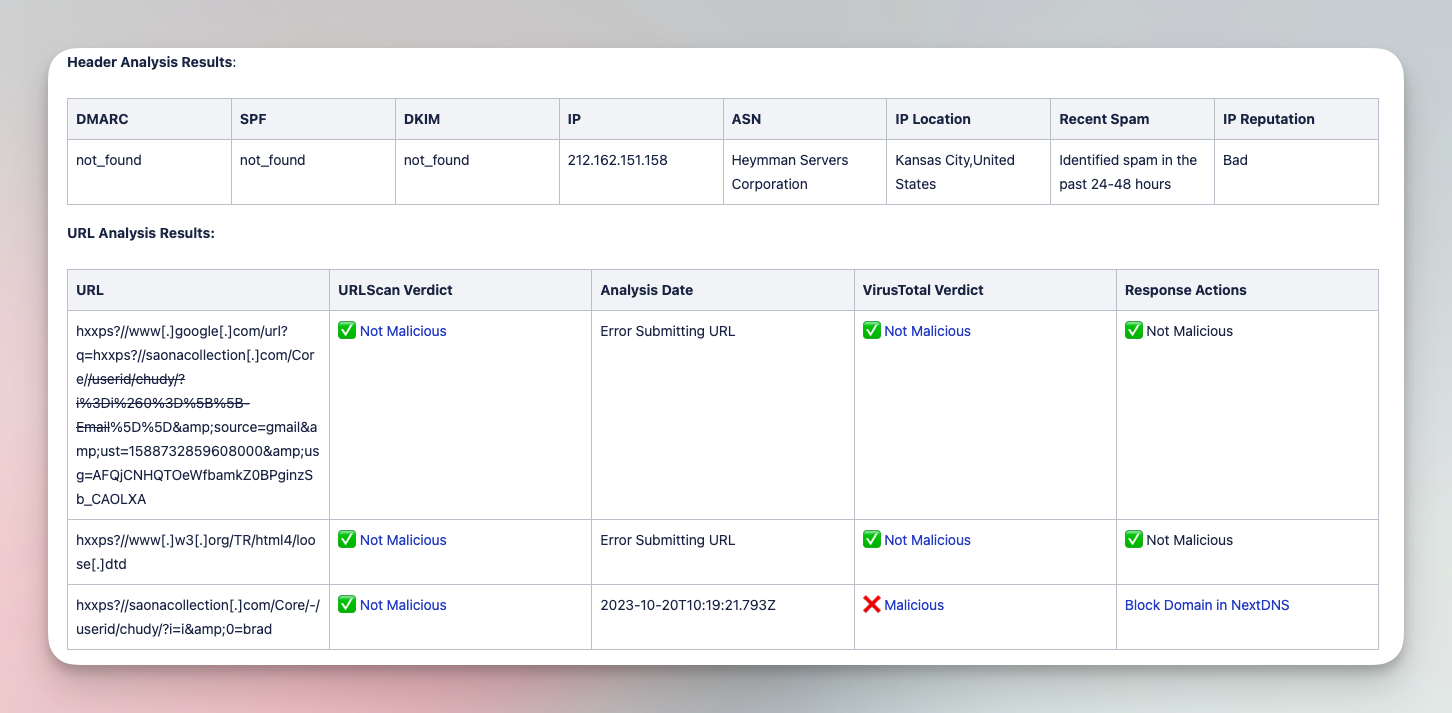
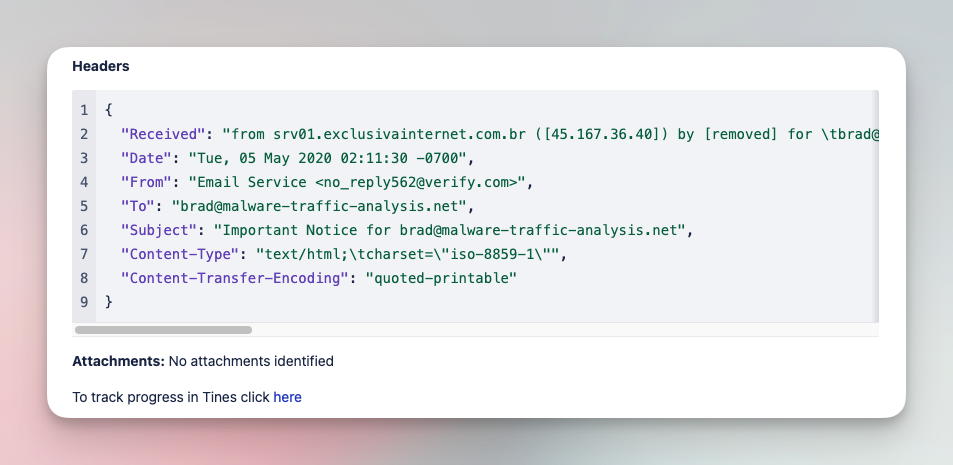
Analyze and triage suspicious emails with various tools
Submit suspicious emails and investigate with a comprehensive analysis of files, URLs, and headers. Add IOCs to various tool blocklists in order to limit impact of phishing campaigns.
Tools
CrowdStrike, EmailRep, Jira Software, NextDNS, URLScan.io, VirusTotal
Created by
How it works
Instantly import stories to your tenant where you can adapt them to meet your unique business requirements.
Learners welcome
Step through beginner to advanced topics as you explore our tailored courses on Tines University.
Latest stories
How Upwork fosters learning through phishing response
“My favorite Story so far is one we built around phishing response. We created it to give the person who reported it feedback on what they reported, which enables my team, via the Story, to further educate the end-users on phishing vs. spam. This helps them to get smarter too.”
Learn more about how Upwork uses Tines.
Get started with
one of our technology partners
Submit your story
We’d love to hear your ideas or see what you’ve created.
