Automation is often seen as the natural progression for a security operations center. However, deciding where and when to implement it can be pretty challenging. As an earlier blog post covers, Tines' Automation Capability Matrix is an innovative set of techniques that empower security operations teams to respond proactively and tackle common cyber-security incidents. With a clear view of their automation capability, these teams can become even more efficient in protecting against potentially damaging threats.
Now that we've covered what the matrix is, let's explore one possible way of utilizing it. In this example, we take a very common process many organizations face - phishing response - and apply the ideas outlined in the Automation Capability Matrix. Many organizations utilize multiple techniques to find and analyze suspicious messages to respond appropriately to malicious emails.
To start, here are some processes a routine phishing investigation might include:
Receive a phishing email or alert
Send a notification to the security team for processing
Create a ticket to track and record the analysis
Review the elements of the email, including attachments, links, and email message headers
If suspicious, delete the email and add features to blocklists
Send a notification to the recipient with a status update
Within the matrix capability Phishing Alerts in the Alert Handling section, it mentions that many organizations implement tools like email security gateways to prevent suspicious emails from being delivered to inboxes while also generating alerts of attack campaigns that could be automated. The capability also outlines a strategy to create a purposeful inbox for users to easily forward phishing emails that may have passed through the filters. Implementing both of these capabilities offers an opportunity to begin an automation workflow.
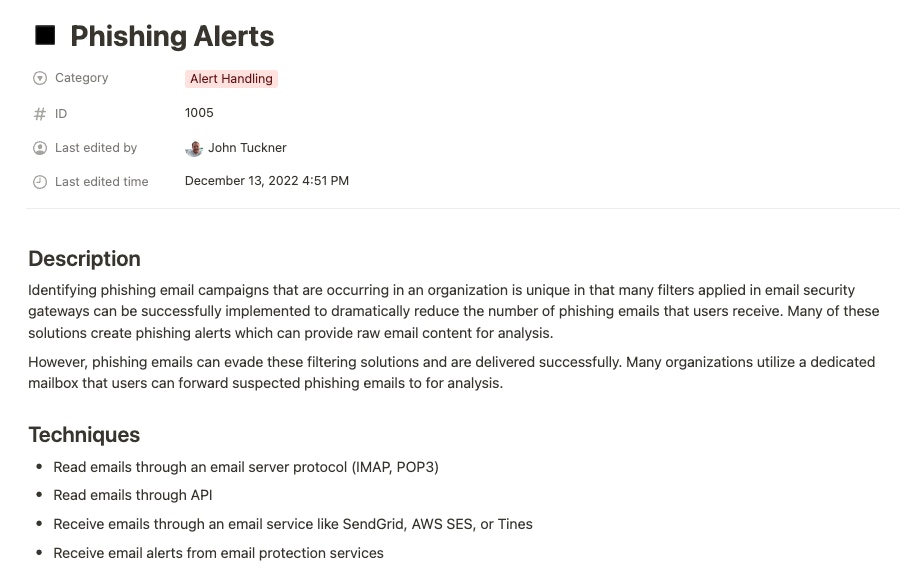
Once a suspicious message has been identified either through the user reporting or generated alert, more automation capabilities become available. A good piece of advice is to create a location for tracking the lifecycle of each alert as soon as possible. Utilizing the Tracking Location capability in the Issue Tracking section, we can identify where these alerts should be recorded, updated, and reported. Notice how the workflow has now moved between sections of the Automation Capability Matrix to extend the process.
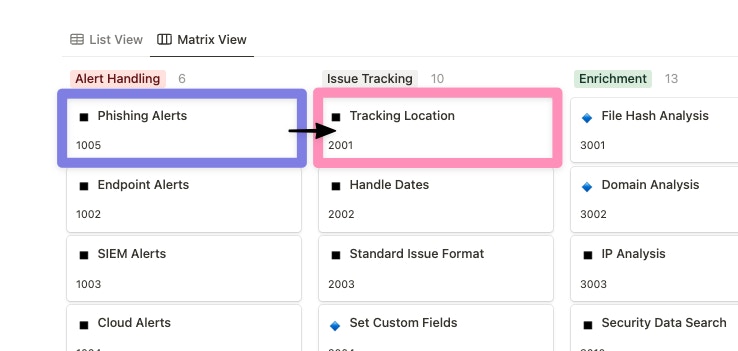
With the alert and tracking location decided on, move towards performing a thorough analysis of the phishing alert in question. Phishing emails commonly contain potentially malicious attachments and suspicious links to capture authentication material and are typically sent from spoofed sources. Moving into the Enrichment phase, we want to focus on utilizing a few key capabilities at a minimum: Domain Analysis for any links present in the email body, File Hash Analysis/File Analysis to look at any attachments to the email, and Email Attributes to look deeper into email headers for signs of emails from spoofed addresses.
For Enrichment opportunities, the number of options for API-driven tools and services that can be used to provide these capabilities grows exponentially. Some common options include VirusTotal for files, URLscan for domains, and EmailRep for sender information. Each of these enrichment results can be recorded in the associated tracking location identified previously to document the outcomes and provide analysts with a view into the results. This shows how many capabilities from the same section can be applied to the same automation workflow, in this case, to provide as much information as possible to analysts.
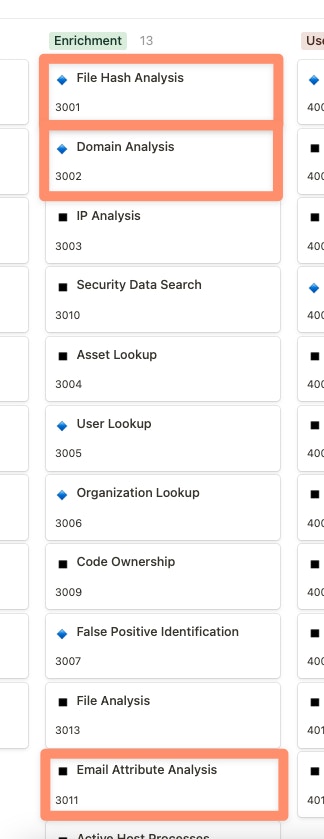
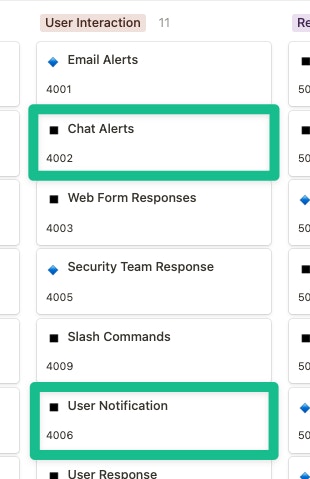
After enrichment occurs, a verdict might be reached already, but more likely, the issue will require a quick review from an analyst. At this point, the User Interaction section becomes critical. To start, we can use Chat Alerts to notify the security team in a Slack channel that a phishing email has arrived and a tracking issue has been created, with various enrichment details added as additional context is ready for review.
That takes care of informing the security team, but what about updating any users who might be impacted or reported the email? Phishing response processes, in particular, are unique because many organizations actively train users to report emails they might identify as suspicious. Informing these users with a confident verdict within a short timeframe is a great way to empower operations such as getting sensitive documents signed quickly or preventing mass malware outbreaks. To do this, we can use the User Notification capability to identify the user who reported the email and provide them with the results of the email analysis. In the case of User Interaction, it is not only about additional notification of the security team but also extending the reach and empowering others with real-time information to make the right decisions.
At this point, a lot of activity has taken place, and we have a lot of knowledge at our disposal. While more information is always helpful, actioning on it appropriately is what ultimately counts most, resulting in the Remediation phase. Many of the data points (indicators) we gathered before can be used for remediation action. Depending on how the situation has played out, we could take some of the following steps:
Domain Blocklist: Add any domains and URLs identified as suspicious to a blocklist.
File Hash Blocklist: Add any file hashes identified as malicious to a blocklist.
Email Deletion: Remove emails related to an attack campaign from inboxes.
Password invalidation: Change the passwords of any users found to have submitted credentials to a phishing website.
The key to any Remediation is to know what is possible and to start small, especially when utilizing automation to build confidence. One way to do this is to provide links or buttons that need to be manually clicked to take remediation actions but in a repeatable manner. If you want to introduce full automation, keeping lists of suspicious domains that can be blocked provides you with great utility, minor risk, and can be fixed quickly with little overall impact when errors occur.
Looking at the process end-to-end, we have utilized the following capabilities to help automate critical actions for many cybersecurity teams:
Phishing Alerts
Tracking Location
File Hash Analysis
Domain Analysis
Email Attributes
Chat Alerts
User Notification
Domain Blocklist
File Hash Blocklist
Email Deletion
Password Invalidation
This might seem like a lot already, but many organizations even opt to do more! Not all of these capabilities require automation, but many are best performed through automation because some steps are often skipped when email analysis is carried out manually.
A significant benefit of developing these capabilities in your organization to address a single process, such as phishing, is that many of these capabilities are now available to be reused for additional purposes like malware detection or handling suspicious logins, making each subsequent automation opportunity in your journey easier!