The SOAR market is undergoing a radical transformation fueled by the rise of next-generation tools that are laser-focused on helping security teams to solve a core problem.
Traditionally, SOAR was driven by all-in-one solutions, claiming to be silver bullets but offering suboptimal functionality and user experiences.
As threats increase in volume and sophistication, and security teams opt for cloud infrastructure and applications, the need for flexible, robust, intuitive software is only increasing, particularly when it comes to security orchestration and automation, where the ability to detect and respond to alerts at speed and scale is critical to preventing cyber attackers from gaining access to an environment.
Tines commissioned a third-party survey of 205 security professionals who routinely use a SOAR platform at work. As part of our research and development, the survey was designed to uncover their opinions and experiences of SOAR tools, and identify any areas for improvement.
We've bucketed our key findings into different areas of interest to share with the broader community. We believe they will benefit anyone evaluating bundled SOAR or standalone platforms and highlight the potential pitfalls of implementing some SOAR solutions in your organization.
Time to value
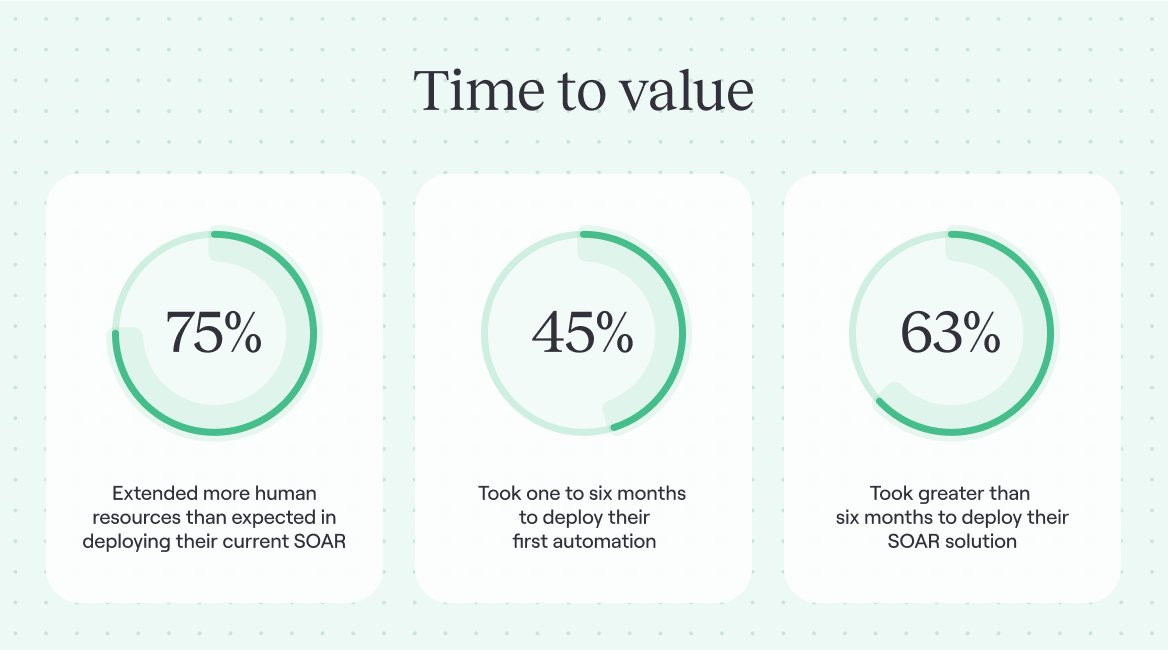
Cybersecurity is becoming an increasingly important concern for businesses of all sizes. In response to this, many organizations turn to SOAR solutions to help them better manage security risks. However, deploying a SOAR solution can be a complex and resource-intensive process. In fact, 75% of security professionals in the survey extended more human resources than they had expected when deploying their current SOAR solution.
Meanwhile, 45% of respondents admit it took one to six months to deploy their first automated workflow, and 63% say it took greater than six months to deploy their SOAR solution. This highlights the importance of carefully vetting a SOAR solution’s ability to meet your requirements. By considering the potential challenges and ensuring that adequate resources are in place, businesses can set themselves up for success when implementing a SOAR solution.
Post-onboarding SOAR weaknesses
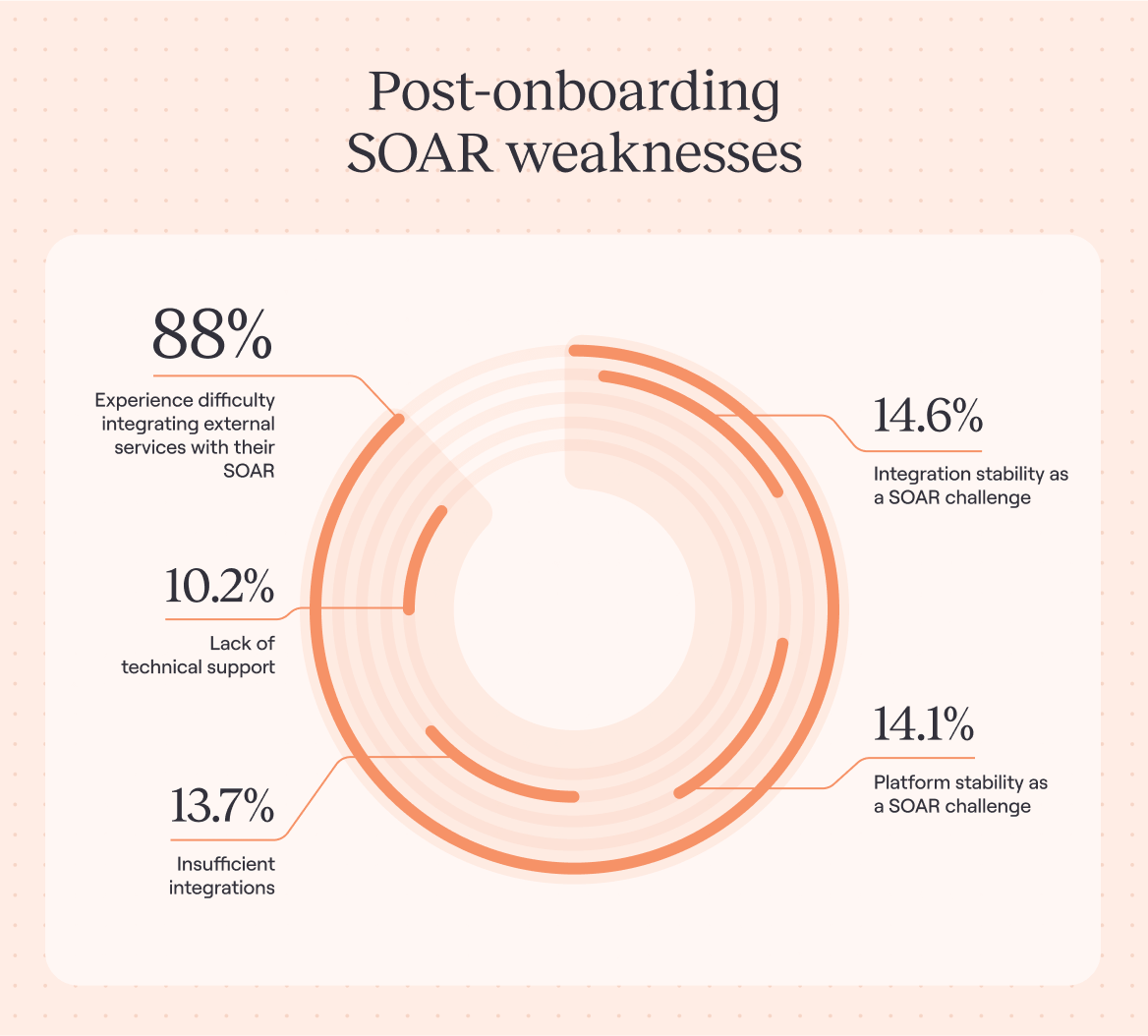
Despite the security benefits that SOAR can bring to an organization, there are some common challenges that should be considered.
One of the biggest issues that security teams face is integrating their SOAR platform with their external services; 88% of respondents report experiencing this difficulty. This can often lead to lengthy deployment delays and also have an impact on your ability to respond to incidents in a timely manner, ultimately increasing your overall risk of an incident.
Another important aspect of security is creating seamless connections between systems and data sources. This is essential for security teams to be able to gather and analyze critical information across their technology stack. However, many security professionals are struggling to achieve this goal. 13.7% of respondents say that insufficient integrations are one of the biggest weaknesses of their current SOAR tool. This issue is often compounded by the fact that many security teams lack the necessary technical expertise to properly configure, manage, and update their integrations.
14.6% of respondents cite integration stability as another core challenge they experience with their current SOAR tool. This is a significant issue as mission-critical cybersecurity processes are increasingly reliant on SOAR platforms and their ability to connect infrastructure.
Platform stability presents additional challenges for 14.1% of survey respondents. The importance of stability in this context cannot be overstated, as a SOAR system that goes down can leave an organization vulnerable. Additionally, 10.2% of respondents report a lack of technical support from their SOAR provider as a challenge. This makes it difficult to address issues that arise and ensure your environment runs smoothly.
It's important to take the time to carefully consider your top priorities before choosing a SOAR solution. Otherwise, you might find yourself at a significant disadvantage when it comes to protecting your network and data.
Top 3 barriers while deploying SOAR platforms
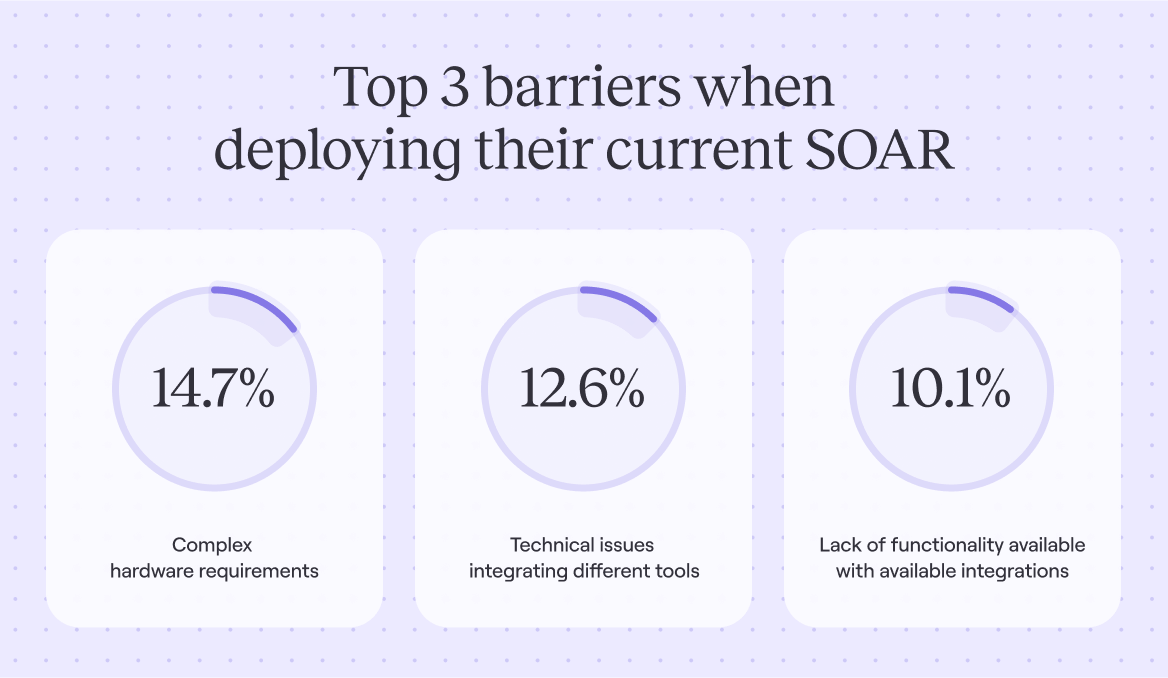
The survey also highlights the top three barriers respondents faced when deploying their current SOAR solution.
The top challenge is complex hardware requirements, with 14.7% of respondents pointing to this issue. Technical difficulties integrating different tools is the second most common challenge, cited by 12.6% of respondents. Finally, 10.1% of respondents say the lack of functionality available with existing integrations is their biggest issue.
While these challenges may seem daunting, they can be avoided with some careful research and due diligence. By working closely with security vendors and allocating time to evaluate different options, organizations can overcome these barriers and deploy a solution that will transform their security operations.
Unbundling SOAR
Perhaps one of the most interesting insights is that most respondents believe laser-focused products will replace bundled SOAR platforms in the next five years. 88% believe SOAR platforms will exist as standalone products that provide best-in-breed, next-generation solutions to security teams.
Looking to the future, customization is the top feature respondents want in a next-generation security platform. They also want version control and history, good documentation, and better collaboration capabilities.
Overall, the survey shows that while SOAR platforms are generally seen as helpful, there is room for improvement in terms of integrations, user experience, and customer support.
3 key takeaways from the State of SOAR report
With cyber threats continuing to increase in volume and sophistication, security teams need built-for-purpose solutions to help them understand their vulnerabilities, identify suspicious behavior, and take action to stop cyber criminals in their tracks. If you’re looking for solutions to protect your organization more efficiently and effectively, here are five tips to help you choose a tech stack that sets your SOC up for success in preventing and mitigating threats.
1. API-first
Optimize for strong APIs. When considering software from any vendors or scoping internal tools, ensure a high-quality API exists. This way, your SOAR tool or security automation platform can properly orchestrate and communicate with it so you have the option to put humans in the loop when necessary while also easily collaborating across teams within your organization.
2. Prioritize orchestration and automation
Use orchestration and automation to gather, enrich, and distill all context for analysts. Summarizing enriched incident details in tickets remains an extremely popular tactic in SOAR tools — something 23% of respondents say they do. For organizations that aren’t quite ready for automated remediation, the low-hanging fruit is making it easy for human analysts to gather more context to understand a new case. Later, as automation grows in sophistication, you can graduate to human-in-the-loop automated remediation, or even fully automated remediation, where sensible.
3. Track your own success
Calculate your own time saved. Any software you buy needs to justify its existence, and for automation or SOAR tools, an appealing idea is that of time saved. However, calculating this accurately is nuanced and often varies wildly depending on factors like use case, organizational design, toolset, etc.
Don’t take your vendor's word for it - calculate your time saved independently. In our survey, 14% of respondents feel that such metrics in their platform were gimmicks not to be taken seriously. The central benefit of an orchestration and automation platform is that it can go further and take actions that wouldn't be possible for a human to execute, making time saved indeterminate. As a result, representations of saved time can range from inflated and dubious to overly conservative or just plain wrong.
Looking to the future
The world of SOAR has rapidly changed over the last few years. Legacy tools often struggle to integrate or orchestrate the modern security stack, and 88% of respondents say they've had difficulties with these core aspects of their existing SOAR tool. Yet many SOC teams are locked into these outdated, bundled solutions, with 59% of respondents using a platform for at least three years.
Today's security teams depend on their tools' strengths and need comprehensive and robust ways to quickly and efficiently protect their organizations. Simply put, the world of technology is ever-changing, and it may be time to consider a new solution.
Tines empowers security teams to move faster and smarter than their current SOAR solution. Find out more.