Living in a digitally connected world pressures companies to deliver product releases quickly, contributing to exponentially growing cybersecurity threats and incidents. According to a 2023 study conducted by the Identity Theft Resource Center (ITRC), a non-profit organization established in 1999, 2,365 cyber-attacks were recorded in the US alone, claiming 343,338,964 victims. Modern businesses must adapt and respond to threats without compromising speed and performance.
For a long time, security has been regarded as an afterthought. Yet, to safeguard assets and data effectively, security must be considered throughout an organization's product and service development and delivery lifecycle. Effective and organized cybersecurity operations offer a solution to this problem.
In this article, we explore all facets of cybersecurity operations: their scope and span, their planning and implementation, and the best practices that make them successful.
Summary of key cybersecurity operations best practices
What is cybersecurity operations (SecOps)?
Cybersecurity operations, or SecOps, is a collaborative approach between security and SaaS (software as a service) or IT operations teams. It aims to strengthen an organization’s security posture by minimizing and responding to security risks and threats in software development and operations.
Traditionally, operations and security have operated as two distinct functions due to clashes in approach: Operations teams seek to deploy services and applications quickly, whereas security teams prioritize the protection of systems and data over timeliness. However, this does not need to be a case of “either/or”—by applying SecOps, both teams can work harmoniously and achieve their goals.
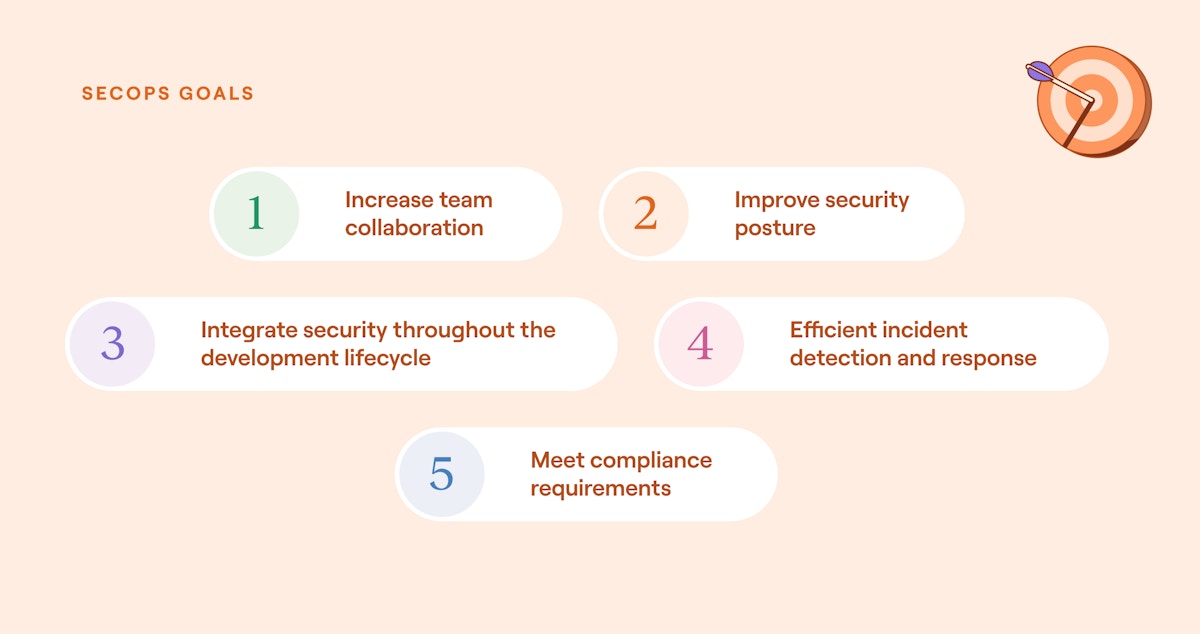
The primary goals of cybersecurity operations, listed in no particular order (source)
SecOps vs. SOC: What’s the difference?
It’s common to hear the terms SecOps and SOC being used interchangeably. Both are tasked with protecting and defending an organization against cyber attacks and threats, but they are distinct concepts.
Security Operations Center (SOC)
Think of the security operations center as the central command and control hub where the bulk of security detection and response activity happens. The SOC is the “home base” of the SecOps team, where they keep their tools.
Traditionally, SOCs were physical hubs, but developments in cloud computing have opened up remote working possibilities (e.g., hybrid and virtual SOCs). Companies also now have more choices in how they build their SOCs: Some opt to keep a wholly in-house function staffed by internal resources, whereas others outsource anything they can’t do internally (known as hybrid or fully outsourced SOCs).
SecOps
While the SOC is the home of the SecOps team, SecOps refers to the overarching collaborative approach between security and operations teams. When implemented successfully, SecOps embeds security across the development lifecycle, from end to end. Areas of focus for SecOps can include implementing and monitoring security controls and detecting and responding to incidents and threats. Overall, SecOps is the security management approach aiming to improve an organization’s security posture.
Workflow orchestration and automation for security teams
- No code or low code - no custom development necessary
- Integrates with all your systems - internal and external
- Built-in safeguards like credential management and change control
The fundamental pillars of cybersecurity operations
Organizations often rely heavily on security tooling to achieve their security goals, but in reality, tooling is just one piece of the puzzle. Successful security operations teams seek to unify three essential elements: people, process, and technology. Teams have a better chance at success when these three areas work in tandem and are not considered in isolation.
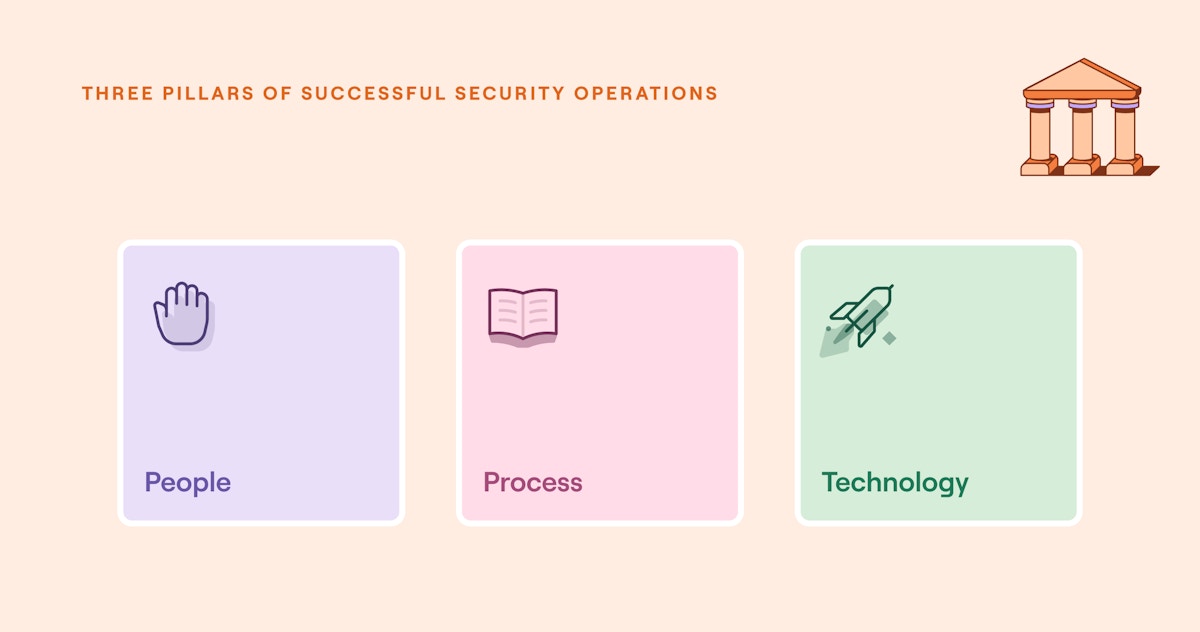
The fundamental elements that underpin successful security operations (source)
People
To meet resourcing and skill demands, you need suitably skilled human beings within the cybersecurity operations team, though what “suitably skilled” means can vary depending on the roles each team member holds. Generally speaking, these capabilities can be broken down into two categories, as detailed in the two tables below:
Technical skills and knowledge
Soft skills
Process
Well-documented security processes (and policies) are required to define how a business acts regarding security and operations. To be effective, they must accurately reflect the reality of your environment and be easy to understand and follow for all who must abide by them. They must also clearly outline any necessary responsibilities and be enforceable for non-compliance.
The table below shows some examples of typical security processes.
Technology
SecOps teams rely on a combination of security and technology tools to monitor an environment for security threats and incidents. The table below provides examples of tooling. These tools monitor infrastructure, endpoints, the cloud, and network devices for suspicious or malicious activity. In a later section, we will cover cybersecurity operations tools and how they are used in more depth.
What are security operations teams responsible for?
SecOps responsibilities should span all stages of the development lifecycle. A combination of specialist skill sets is required to cover all bases effectively. The tables below outline key areas of responsibility you can expect to see in well-established cybersecurity operations teams:
SecOps team’s areas of responsibility
The following table summarizes the SecOps team's responsibilities in key areas:
Typical roles in a cybersecurity operations team
As of last year, cybersecurity operations teams were staffed by an average of 11-25 people. While each organization’s approach to resourcing may differ, some roles are typical of most SecOps teams, as shown in the figure below.

The typical roles and responsibilities in the majority of SecOps teams (source)
Additional specialized cybersecurity operations roles exist, usually within mature SecOps teams:
Digital forensics specialists
Threat hunting specialists
Red and purple team specialists
Compliance roles (e.g., auditors or assessors), although these often sit within governance, risk, and compliance (GRC) functions as opposed to security operations.
See Tines’ library of pre-built workflows
Core cybersecurity operations tools
SecOps teams require a combination of tools to protect assets and data within operations and development environments. Listed below are some of the standard core security operations tools.
SIEM & SOAR
Security information and event management (SIEM) tools collect large volumes of security-related information, ingesting it from various data sources (e.g., endpoints, servers, network devices, and applications). The platform turns the data into a view that is more accessible to human analysts, enabling increased detection and response efficiency.
Security orchestration, automation, and response (SOAR) technologies assist SecOps teams in reducing the time they spend on manual tasks. When leveraged effectively, automation and orchestration tools can help develop and scale cybersecurity operations. SOAR solutions vary greatly in their capabilities. This ranges from traditional SOAR platforms that are well-known (but often have limited integration features) to more modern solutions that leverage innovative approaches - such as artificial intelligence).
SOAR tools use a variety of methods. An example of this is the “no-code” approach, which enables teams to automate workflows without the need for existing coding knowledge. A typical SOAR use case could be incident enrichment, ingesting various threat feeds and automatically applying context to incidents to enable analysts to make better-informed decisions.
EPP & EDR
Endpoint protection platforms (EPP) and endpoint detection and response (EDR) tools both protect endpoints at the device level, but they approach it differently. EPP aims to prevent threats from ever fully hitting an endpoint, whereas EDR assumes a breach has occurred, providing attack detection, containment, and response capabilities. Some platforms offer a combined approach. Another variant of detection and response tooling that focuses solely on cloud devices is cloud detection and response (CDR).
You might also come across extended detection and response. XDR goes beyond the device level, integrating various security tools (e.g., network, cloud, email, and device security tools) to provide an extended holistic approach.
Network detection and response (NDR)
NDR solutions seek to detect malicious traffic and suspicious network activity. Often, these tools utilize machine learning techniques in their analysis to pick up on anomalous behavior that other security monitoring tools (e.g., signature-based tools) might miss.
User and entity behavior analytics (UEBA)
Traditional security solutions, like those listed above, are effective at identifying and managing known threats. In contrast, user and entity behavior analytics (UEBA) excels at identifying unknown threats using machine learning and behavioral analysis techniques.
Threat and vulnerability platforms
There are a variety of tools that can be used to identify and manage threats and vulnerabilities across the estate. Examples include:
Vulnerability scanners
Coding and software development testing tools, e.g., source code analysis (SCA) and static and dynamic application security testing (SAST/DAST)
Vulnerability management solutions (e.g., those that provide scanning, risk assessment and remediation capabilities)
Threat intelligence platforms (note: often threat and vulnerability capabilities are built into other existing monitoring tools, e.g., SIEM and EDR)
Other tools
Additional proactive tools used by more mature cybersecurity operations functions include the following:
Deception tools (e.g., honeypots, honeytokens, decoys)
External attack surface management tools (e.g., rogue asset/access identification, advanced shadow IT/AI detection)
Generative AI, machine learning, and advanced automation capabilities
Challenges faced by many cybersecurity operations teams
SecOps teams fight a continuous battle against expanding attack surfaces and the increasing sophistication of cyber attacks. These factors present several challenges:
Lack of visibility: Maintaining visibility of the entire estate becomes challenging when the perimeter expands. Widespread adoption of cloud computing and emerging technologies—such as GenAI and the Internet of things—adds further complexity to the attack surface. These technologies are often externally exposed, offering additional breach paths for attackers to exploit.
Alert fatigue, false positives, and manual workloads: SecOps teams are often exposed to overwhelming alert volumes, with the average SOC receiving 4,484 alerts daily. Teams spend almost three hours each day performing manual triage. Poor tool configuration often causes too much noise, with tools generating data that includes excessive false-positive results. Due to the sheer amount of work required to respond to the increasing volume of alerts, many analysts suffer from stress and burnout.
Too many tools but not enough integration: Cybersecurity operations teams have much ground to cover in their responsibilities, leading to investment in numerous tools—sometimes too many disparate ones. It’s estimated that the average organization has 76 security tools to manage. Additionally, more tools equals more alerts, contributing further to alert fatigue.
Security skills gaps and resourcing challenges: The cybersecurity industry faces an ongoing skills shortage, with global job vacancies having grown by 350%. It’s estimated that by 2025, there will be 3.5 million vacant positions. Many SOC teams struggle with high turnover due to stress and burnout, which presents a further problem. A survey of 900 security professionals conducted in 2023 showed that 63% of security practitioners are experiencing some level of burnout at work.
Read our free essential guide to security automation
Best practices for effective security operations
To address the challenges described above and increase effectiveness, SecOps teams need to evolve and adapt. Below, we’ve listed the best practices for successful security operations.
Develop and implement a clear strategy and approach
To set your cybersecurity operations team up for success, define an approach that works for your business. Start by scoping out your requirements, and use this to formulate a clear strategy covering the three fundamental pillars mentioned earlier: people, process, and technology. Ensure that you don’t consider these elements in isolation—they should tie together into one cohesive approach. Obtaining senior management buy-in on your strategy (and any associated plans) is vital to ensuring that they have the right level of support.
Every company is different, so think carefully about choosing a suitable model for your SOC. Consider outsourcing parts of the function to reduce your internal team’s workload. A couple of examples of this could include:
Outsourcing the first-line response capability of your SOC (i.e., the initial alert logging and triaging steps) before passing to your skilled internal human analysts for on-the-ground incident response
Outsourcing more complex root-cause analysis or incident response activities to an external supplier who provides incident response (IR) retainer or digital forensics services
Effective communication and collaboration are essential for SecOps functions to thrive. Aim to establish a shared responsibility approach across the business, so staff understand that security is everyone’s responsibility.
Embed security throughout the development lifecycle
It’s essential that security be made part of every phase of the full development lifecycle. To achieve this, you need to understand both the development and operations environments.
Consider reaching out to other business areas (e.g., other infrastructure teams, engineering, cloud, technology, service desk teams, and business line managers) to better understand what they do and any challenges they face when meeting security requirements. Building these communication channels can help increase a cybersecurity operations team’s visibility and identify potential gaps in monitoring coverage.
An example of a coverage gap could be where an organization has not onboarded critical log sources to their security monitoring platform. For example, consider a virtual local area network (VLAN) containing high-risk network devices that aren’t currently being monitored for security threats. This gap could have been discovered and remediated by establishing communication channels with the network team managing the VLAN.
Finally, ensure that you maintain regular contact with other business areas and continually verify the accuracy of your log and data sources to improve the quality of your security monitoring data.
Automate repetitive manual activities
A SIEM tool can provide automation capability in terms of real-time threat detection at scale, but it needs to be configured correctly. Ensure that you conduct fine-tuning activity within any security monitoring tool to reduce alert noise and the occurrence of false positives.
Human analysts waste hours and hours on repetitive low-level tasks such as raising tickets, triaging common threat types, sending updates, and researching context to apply to incidents. Consider using no-code orchestration and automation platforms to automate workflows and make them repeatable, enabling your human analysts to focus on what matters and better utilize their specialist skill sets on complex tasks.
Make smart tooling decisions
Many security tools exist, but this doesn’t mean you need them all. Rather than investing in separate tools to plug the gaps, seek to maximize the value of your existing toolset first. If the necessary functionality doesn’t exist in those tools, look at new options, but keep these considerations in mind to help make effective decisions:
Approach the process with consolidation and orchestration in mind to reduce overall complexity.
Prioritize tools that offer easy integration and customization capabilities, with support for services within your existing tech stack.
To enhance effectiveness, look for workflow automation and orchestration capabilities and consider features that add further contextual information (e.g., risk and asset data).
Incorporate threat feeds and/or frameworks for contextual enrichment. Integrating frameworks such as MITRE ATT&CK can help you better understand your adversaries, providing insight into their tactics, techniques, and procedures while strengthening response effectiveness.
Emphasize training, development, and resource management
To have the best chance of success, cybersecurity operations teams must be adequately resourced. Managers should aim to hire a mixture of individuals with a diverse range of specialized security skill sets. Ongoing proactive resource management is critical to lessening the pressure on remaining team members and reducing the risk of overwhelm and burnout.
Given the ever-changing nature of cybersecurity, your SecOps team should be offered regular training and development opportunities to expand their knowledge.
Did you know Tines' Community Edition is free forever?
- No code or low code - no custom development necessary
- Integrates with all your systems - internal and external
- Built-in safeguards like credential management and change control
Last thoughts
With the right tools and approach, cybersecurity operations teams can effectively defend organizations against cyber threats without compromising performance. A successful SecOps strategy combines people, processes, and technology, giving equal consideration to all three elements. SecOps teams can be optimized to develop their effectiveness through consolidation, automation, orchestration, and standardization activity.