Security automation improves an organization’s security posture. When done effectively, it enables organizations to scale existing tooling, reduce manual processes, and integrate cybersecurity deeper into the business.
For cybersecurity professionals, security automation and orchestration enable preventative, investigative, and monitoring activities to be deeply integrated into daily operations. This creates more confidence in the product’s security, reduces alert fatigue, and improves investigative outcomes.
This article explores how security automation can assist with the preproduction and production stages of software development. It is written for cybersecurity professionals, and each section contains one or more practical examples of security automation in action.
Summary of key security automation opportunities
The table below summarizes the concepts covered in this article.
The rest of this article delves into each concept introduced in the table above. Each section provides more context about a specific concept and provides a practical example of it in action.
Workflow orchestration and automation for security teams
- No code or low code - no custom development necessary
- Integrates with all your systems - internal and external
- Built-in safeguards like credential management and change control
Source code review and dependency management
Security automation enables organizations to combine static application security testing (SAST) tools into a holistic source code review and dependency management program. SAST assesses source code for vulnerabilities, application design flaws, and insecure code; it typically includes scanning native source code and code dependencies such as third-party libraries.
Various tools simplify SAST for developers. Snyk Code integrates with popular integrated development environments (IDEs). IDEs such as Visual Studio Code (VS Code) can integrate SAST tools to secure code as it’s written, providing real-time reports and checks for developers. GitHub’s Dependabot generates alerts when vulnerabilities are detected in dependencies used by a project’s code base.
Snyk Code Report (source)
Here, a security workflow orchestration and automation tool called Tines takes the output of Snyk’s code-scanning capabilities and scales it across the entire organization. As vulnerabilities are identified, they are matched against predefined thresholds, and JIRA tickets are created.


Query Snyk & gather a vulnerability report
Query each project within all Synk organizations for critical vulnerabilities. Create a custom report in Jira for each organization, containing only those Snyk projects which meet specific vulnerability severity.
Tools
CI/CD pipeline
Security automation increases the security of continuous integration / continuous deployment (CI/CD) pipelines and enables the integration of dynamic application security testing (DAST). Combining these two aspects improves the security of the software product while reducing the likelihood of poisoned pipeline execution attacks.
CI/CD pipeline security
Businesses face a dilemma when protecting CI/CD pipelines from poisoned pipeline execution attacks. Rapid deployment capabilities become meaningless if securing them requires more resources than previous methods.
Security orchestration and automation offer a solution to this dilemma. It preserves CI/CD’s rapid deployment advantages while also allowing the integration of cybersecurity tooling.
Security automation can help by doing the following:
Automating secure container configurations, including endpoint detection and response (EDR) tools, log specifications, and container secrets management.
Enforcing role-based access controls (RBAC) throughout CI/CD pipeline infrastructure, including temporary credential creation and teardown
Implementing secrets management throughout the CI/CD pipeline
Configuring secure network configurations during each stage of the pipeline
Configuring static code analysis in the pipeline builds (discussed previously)
Dynamic application security testing (DAST)
DAST ensures that applications are not susceptible to known vulnerabilities and automated attack vectors. Tools such as Tenable Vulnerability Management simulate events that expose vulnerabilities in an application and then observe how the application responds. The response determines whether the application is vulnerable to that sequence of events.
Successfully passing DAST assures organizations that the application is not vulnerable to these known vulnerabilities.
Security orchestration and automation enable DAST to be integrated into a CI/CD pipeline. For example, the workflow below launches a Tenable scan on a specific web app each time a CI/CD pipeline process is triggered. Once the scan is completed, a report is generated and emailed to a decision-maker.


Launch DAST scan on web app via CI/CD pipeline
This story is getting triggered from the CI/CD pipeline to launch a DAST scan on a specific web app. It takes 2 arguments, such as APP Name and ConfigID. It will launch a scan from Tenable.io and will send a PDF with the results if successful.
Community author
Julien D.
User acceptance testing (UAT)
Security automation allows the integration of script-based UAT tests into code releases. This allows applications to be tested with complex, scripted attacks and event sequences in a real-world environment.
Consider the simple example of an organization wanting to confirm that their production web app is not vulnerable to a remote file inclusion attack. To test this, a script could be developed that passes a “malicious” remote file into all observed include locations and then tests the response. If the script executes successfully, then a vulnerability has been discovered—the developers are notified, and a new release can be pushed to fix the issue.
Organizations can use security automation to apply this script to every PHP code release across every project. They can also develop more complex scripts and attacks, covering things like the Mitre Att&ck Framework and specific regulatory requirements.
As the library of UAT attacks grows, security automation ensures that every code release is tested against all relevant attacks with no further involvement from individuals (unless they have to fix a vulnerability they created).
See Tines’ library of pre-built workflows
Ongoing monitoring and maintenance
Security automation streamlines business-as-usual maintenance and monitoring activities.
Maintenance
Rolling out scheduled updates and maintenance activities securely can require considerable resources—even operating system (OS) updates can become complicated. The requirement to test an OS update thoroughly with a pilot group, confirm its effectiveness, and then deploy it to the broader organization means there are multiple potential points of failure.
Security automation can simplify many of these maintenance activities. In the image below, automation is used to streamline a macOS software update. It includes integrations with Jamf for asset management, Slack for communication, and JIRA for user registration. In the workflow, the following processes are covered:
Identification of a new macOS update
Testing the update on a small group of pilot users, each of whom is notified on Slack
Preventing access to the update from non-pilot group users
Enabling organization-wide updates once testing is completed
Streamline macOS software updates with self-service patch management
Our macOS Patch Management automation streamlines the entire lifecycle of managing software updates for macOS operating systems. It includes a self-service implementation of opting in and out of the patch management pilot group via Tines pages and a ring 0/ring1 approach to distributing macOS operating system updates. Updates are initially pushed to the pilot group for testing, and after a week, they are rolled out to the production group. This automation neatly balances user empowerment, system security and stability, and overall reduction of our company's attack surface.
Tools
Community author
Tyler Talaga at MyFitnessPal
Monitoring
Initial event triage capability is provided by integrating security automation into existing security information and event management (SIEM), extended security orchestration, automation, and response (SOAR), and EDR tooling. An auto-triage capability can reduce false positive alerts, enrich successful alerts, and take initial containment actions if certain thresholds are met.
For example, if an organization subscribes to Crowdstrike Falcon Overwatch, security automation can automatically contain devices flagged by the Overwatch team, creating a JIRA ticket for further review. While the security team responds, existing logs for the impacted assets can be captured and tagged in the SIEM.
Other practical uses for initial triage activities can include:
Gathering network logs if a suspicious IP is detected
Checking geo-locations for assets
Confirming threat intelligence alerts against network activity before passing them on to investigation teams. A more extensive example of this workflow is covered later in this article.
Anomaly detection and event correlation
Integrating security automation into existing SIEM, SOAR, and EDR tools offers opportunities to enhance anomaly detection and event correlation. Platforms like Tines serve as a bridge between different tools and capabilities, allowing data outputs from one tool to be compared with another, resulting in a deeper understanding of events.
For example, consider how the response to a sensitive S3 bucket exposure would change based on contextual queues. If the only known event was exposure of the S3 bucket by a user, the incident would be straightforward to manage. Many organizations would capture the length of the exposure, what access occurred during the exposure, and some kind of remediation training for the user. Ultimately, the event, while frustrating, would be quickly closed.
However, imagine how the investigation would escalate if it were revealed that the user profile that caused the exposure had been created 24 hours ago along with extensive administrator privileges. This extra contextual information immediately makes the S3 bucket exposure more suspicious: Various questions about the user profiles’ legitimacy and intent would need to be answered. Many organizations would completely change their response, and it would probably have significant executive involvement while the investigation proceeded.
Security automation enables contextual information to be gathered for defined events. Instead of relying on security teams to remember to check predefined correlation events for events, the workflowis triggered each and every time the event occurs.
Did you know Tines' Community Edition is free forever?
Incident response
Each stage of the incident response lifecycle benefits from security automation.
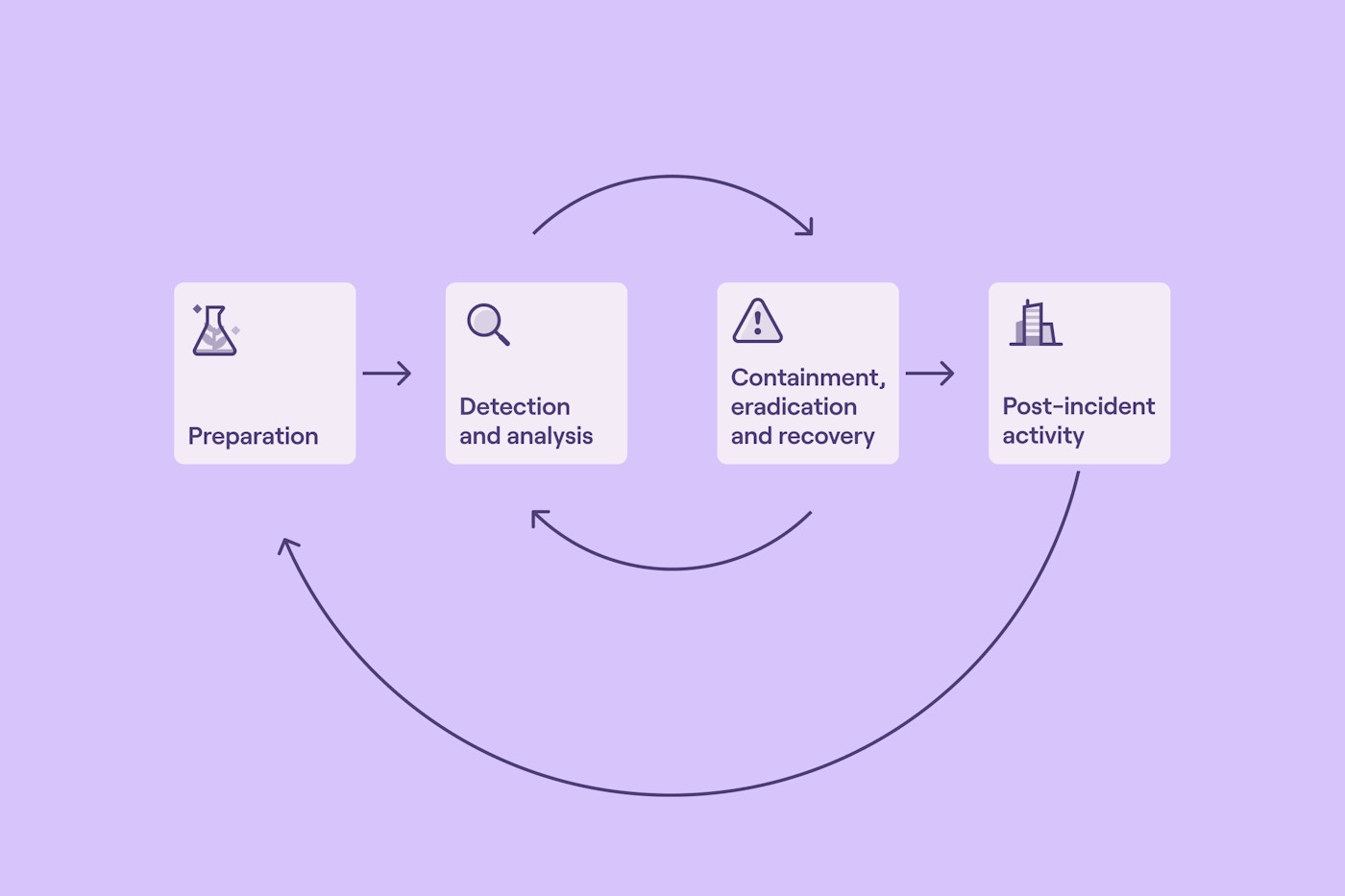
Incident response lifecycle (content source)
Preparation
It is extremely frustrating for a computer security incident response team (CSIRT) to respond to an incident only to find that the exact logs they need haven’t been captured. Equally frustrating is discovering that the forensic workstation they need has been repurposed because it hasn’t been used for the past two weeks. Not only are these events incredibly annoying for CSIRTs, but they can also result in significantly more investigation time as other correlating events or resources are gathered. This can be a critical issue in cloud environments where ephemeral resources such as containers are common—by the time a CSIRT responds to the event, the asset may no longer exist.
Security automation helps solve this issue. It enables incident response teams to specify the tools and logs needed and trust the workflow to make it happen. The specification can include everything from EDR tools to automating the creation of a digital forensic capability and sending logs to the SIEM. In cloud environments, CSIRTs can capture memory dumps on ephemeral containers and specify container images with the tools they need to respond effectively.
For example, the image below shows how security automation can create a digital forensic file analysis environment. The environment is always on call and available, with the only resource requirement being an AWS subscription.


Run a Forensics Lab in Tines
From the submitter: This story is a POC which tries to copy the functionality of forensic tools like FTK Toolkit and Autopsy. Although not at the same level of complexity the story has the core elements of those tools like, having the ability to create Forensic Cases, parsing disk images created using FTK Imager, viewing internal disk structures (as hex or table where possible), view what files were saved or deleted on disk and also dump files or disk regions for further investigation. For the purpose of this competition and also being limited by the 1MB file size, the story is built to only parse disk images formatted with the FAT filesystem type. The technologies used in this story are Tines (95%) and AWS (5%). The AWS environment is set up to use a Lambda Function, S3 bucket and an API gateway which allows communication between AWS and Tines.
Community author
Todoran Horia
Detection and analysis
Security automation can assist incident response teams beyond anomaly detection and event correlation and provide help with in-depth analysis. This might include something as simple as extracting log files and formatting them into a usable format or something more complex. For instance, an analyst might want to extract a potentially unwanted program (PUP) and perform static file analysis on the executable to investigate it further; without security automation, this can be a time-consuming task.
In the image below, security automation is used to save an analyst some time. The analyst has specified that a memory dump of an asset is required. Instead of manually waiting for a user to log onto the asset, then connecting to the asset, dumping the memory, and proceeding, the user can queue the workflow to do it for them. Once the process is complete, the security automation emails them.


Initiate CrowdStrike RTR memory dump
Initiate a remote Memory Dump in CrowdStrike Falcon via a Tines form. Input a device ID and a filepath on the remote machine and receive an email once the memory dump has completed on the device.
Tools
Containment and eradication
Security automation enables the scaling of containment and eradication efforts. This can be particularly useful for larger organizations, events requiring immediate response, or events where a complex set of actions must simultaneously be performed on multiple assets.
Common examples of this type of activity include:
Blocking network access to assets with specific indicators of compromise (IOCs)
Removing a banned user from multiple assets
Killing a malicious process on multiple hosts at the same time
Diverting network traffic to a different segment of the network
Build security automations faster with 1000+ pre-built workflows
- Pre-built workflows for every domain - from threat intel to IAM
- Easy to import and customize in minutes
- Includes workflows submitted by fellow security practitioners
Post-incident activity
The ability of security automation tools to integrate with ticketing systems provides value. CSIRTs can use automation to capture and store logs, artifacts, and other contributing information without manually retrieving it. Removing these manual tasks allows CSIRTs to focus their post-incident activity on recording their thoughts and possible solutions rather than data capture.
Root cause analysis (RCA)
Incorporating security automation into the RCA process allows participants to focus on capturing their thoughts and observations while the automation takes care of the data capture.
For instance, given specific information about an event, security automation is effective at mapping that event to a causal account, asset, or process. Depending on the type of event being identified, security automation can continue to capture and store logs, network traces, memory images, disk images, and so on.
Security automation can also provide logs and other information to specialized RCA software to identify hidden dependencies.


Gather & add correlated searches in Splunk Enterprise Security to Drata
Search the notable index to gather correlated searches that have triggered in Splunk Enterprise Security. Gather the results of the search and add them as evidence to the logging security controls within Drata.
Threat intelligence
Security automation allows organizations to use threat intelligence feeds more effectively. Here are several common use cases:
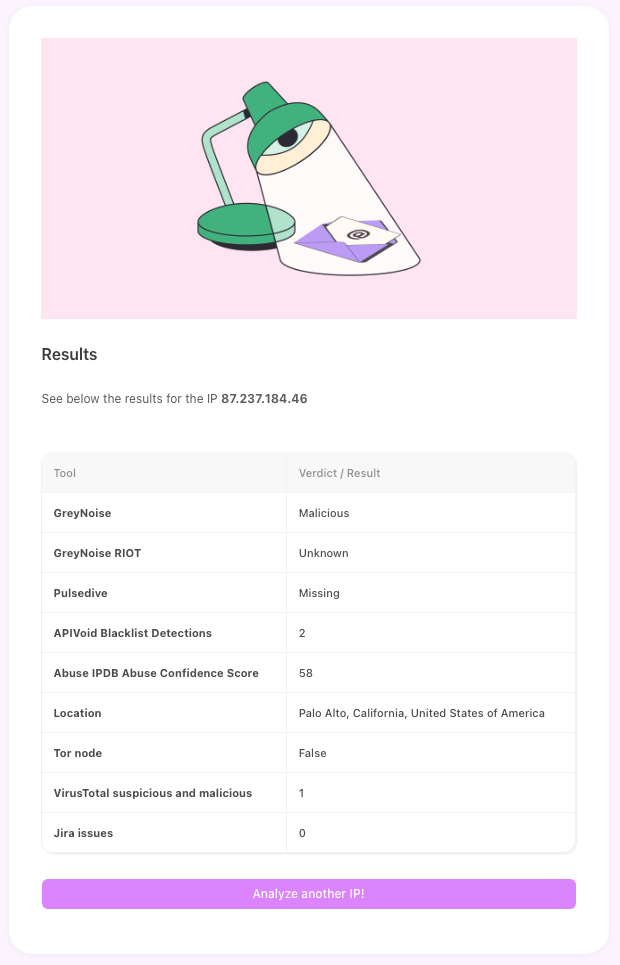
Analyzing a suspicious IP address with multiple services
Confirming if an alerted IOC is present in the network before alerting security teams; if it is, provide information about where it is present, how long it was present, and any relevant logs.
Routing different types of qualified alerts to the right team, e.g., product security alerts would be routed to product security (ProdSec) or application security (AppSec) teams, while IOC alerts would be routed to a SOC/CSIRT, depending on the severity



Analyze an IP in many services at once
Analyze an IP address across some of the most popular IP reputation and enrichment services, and consolidate results using the best data.
Tools
AbuseIPDB, APIVoid, GreyNoise, Jira Software, Pulsedive, VirusTotal
Created by
Threat hunting
The proactive, hypothesis-driven approach of threat hunting offers several opportunities for integrating security orchestration and automation.
First, security automation can be used to prove or disprove a hypothesis. Leveraging an organization’s existing security stack (SIEM, EDR), the information required to resolve the hypothesis can be loaded into a workflow orchestration and automation platform. Once the workflow is ready, it can be run, and the results can be analyzed asynchronously.
Second, security automation focuses threat hunting on specific areas of interest in a network. Assuming that the first point is in place, a threat hunt can be focused on a specific part of the network at a specific time, allowing threat hunters to integrate with other network activities.
Third, security automation can connect threat-hunting to the rest of the organization. For instance, if a threat hunt identifies a valid threat, security automation allows a smoother handoff to other participating teams, such as a CSIRT.


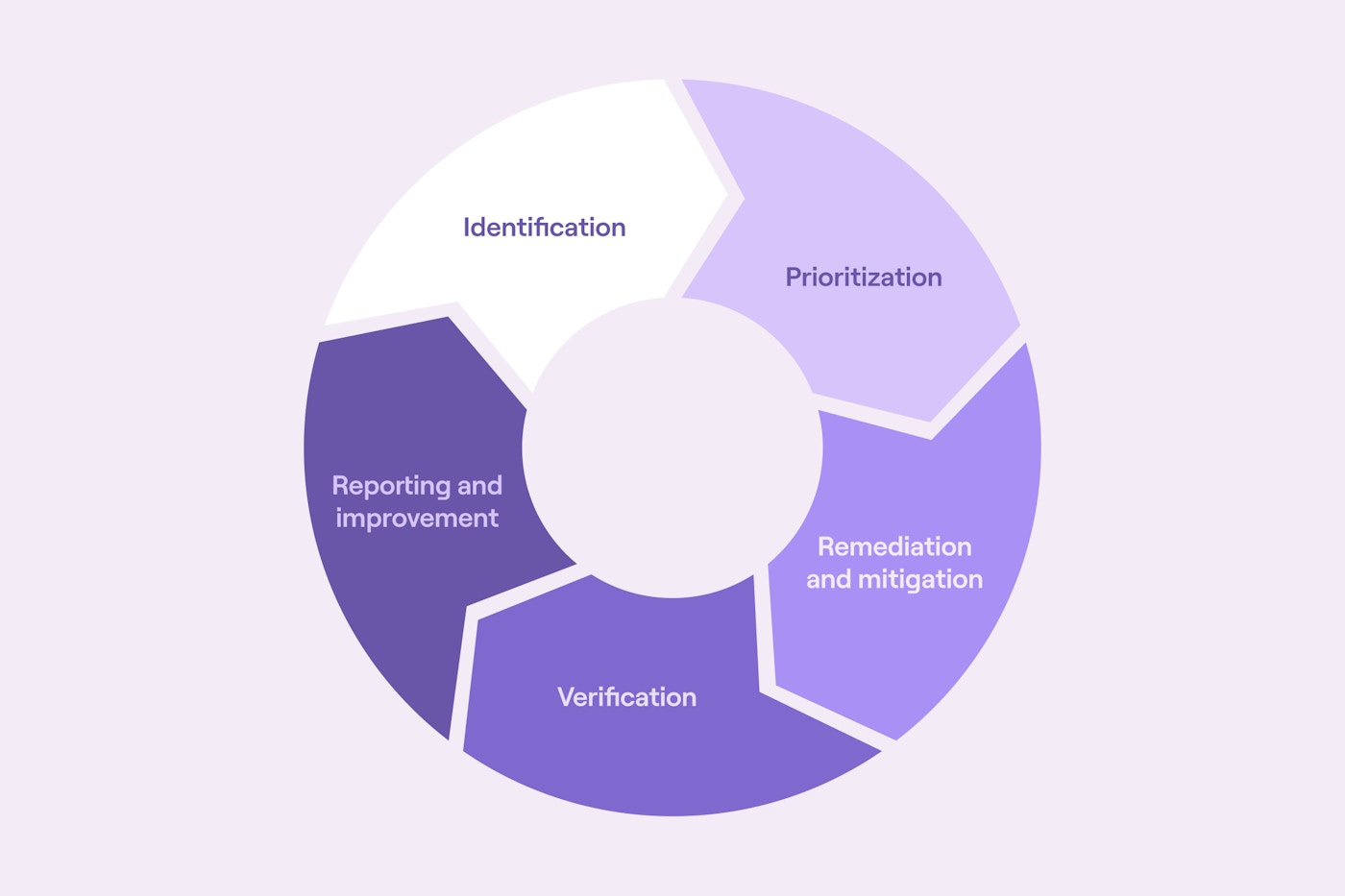
Vulnerability management lifecycle
Security automation enables organizations to streamline the vulnerability management process.
Vulnerability lifecycle (content source)
Identification
Using security orchestration and automation, various components of vulnerability identification can be orchestrated to work together. For instance, the outputs from an Orca Cloud Scan could be automatically assigned to the team responsible for managing a vulnerable asset.
Security automation can also connect other parts of an organization’s security capability to vulnerability identification. For instance, once a vulnerability alert is qualified from a threat intelligence feed, it could be automatically routed to the team responsible for remediation. Depending on the type of alert and vulnerability, the alert could be enriched with additional helpful information, such as what library or code base the vulnerability originates from, how long it has existed, and other contributing information.

Run & track vulnerability scans with Orca Security
Intake cloud assets, run a scan, and check for vulnerabilities. If vulnerabilities are present, a JIRA ticket will be created for remediation. If not, the asset owner will be updated via email.
Tools
Prioritization
Security automation can help prioritize vulnerability remediation work based on workload, regulator requirements, and other business requirements. This can be done directly or indirectly.
In the direct method, a workflow orchestration and automation platform can be preloaded with prioritization triggers and conditional branches. As vulnerabilities occur, the preloaded triggers apply the correct vulnerability rating and assign the vulnerability to the right team.
In the indirect method, security automation handles the inputs and outputs of a prioritization engine, such as Jupiter One. As the prioritization engine adjusts remediation work, the security automation handles any notifications and ticket adjustments.
Remediation and mitigation
Security automation can assist with the ongoing tracking of remediation and mitigation work. This can include automated reminders for any open tickets and updates on prioritizing the work being performed.
Verification
Once a vulnerability has been remediated, security automation can confirm that the remediation is effective and the vulnerability has been removed. Typically, this will involve attempting to replicate the conditions of the initial report—for instance, rerunning the Orca Cloud Scan or replaying the original script.
Reporting and improvement
Once vulnerability remediation has been verified, security automation can update the ticket system with the confirmed status. This might include capturing the logs for the initial report and remediation verification, as well as a log of any critical steps that were taken.
Security automation can also help manage the mitigations implemented during the vulnerability period. For instance, any alert suppression enabled during the remediation work could be automatically removed, or any assets disconnected from the network could be reconnected.
Read our free essential guide to security automation
Last thoughts
Security automation improves cybersecurity within an organization. It allows organizations to automate manual processes, apply existing tooling at a broader scale, and integrate healthy cybersecurity practices into all aspects of the development lifecycle. This improves the business’s preventative, investigative, and monitoring capabilities and outcomes. As a result, organizations become more confident in the security of their product, more likely to catch issues before they reach production, and ultimately, become more resilient.