With AWS Security Hub, Amazon has provided a way for AWS customers to “quickly see their entire AWS security and compliance state in one place, and so help to identify specific accounts and resources that require attention.”
Security Hub went GA in July 2019 and although there is debate around the material value the service will provide, specifically in terms of ROI (when it’s enabled, 30+ Config rules are created per account, this can quickly become expensive), the benefit for enterprise security teams of having a centralized portal for Inspector, GuardDuty, and CIS benchmark findings are intriguing.
In this post, we will explore how to send findings from Security Hub to Tines so they can be enriched, prioritized, deduplicated, and ticketed.
How AWS Security Hub Works
When you enable Security Hub, it immediately begins consuming, aggregating, organizing, and prioritizing findings from AWS services, such as Amazon GuardDuty, Amazon Inspector, and Amazon Macie, and from AWS partner security products. Security Hub generates its own findings by running continuous, automated compliance checks based on AWS best practices and supported industry standards. It then correlates and consolidates findings across providers to help you to prioritize the most significant findings.
As AWS Security Hub discovers findings, it will automatically send them to CloudWatch Events. As a result of this automated process, it’s simple to trigger notifications to Tines through SNS Topics.
Tines AWS Security Hub Automation Story
Here you will find a Tines automation Story which you should download and import into your Tines tenant. The Story contains five agents. including a Webhook Action, which we’ll use to receive events from Security Hub.
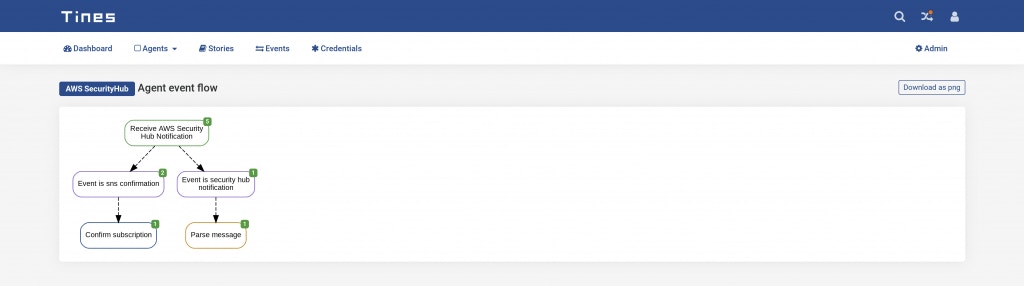
AWS Security Hub Tines Automation Story
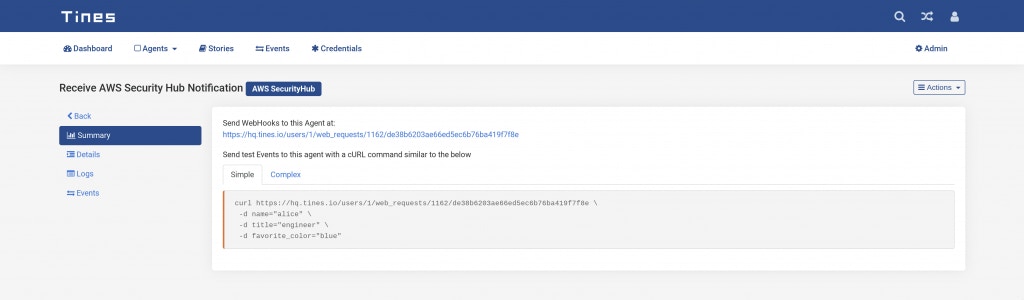
Webhook Action Receives SNS Notifications
Take note of the Webhook URL from the Summary tab in the Tines Action view, we’ll need to provide this to AWS. In the above example, the Webhook URL is:
Using the Tines AWS Security Hub CloudFormation Template
Next, you will need to configure AWS Security Hub to send CloudWatch Events to Tines. Although you can do this manually, we also provide a CloudFormation template that does the hard work for you.
Download the template from here and upload it to CloudFormation.
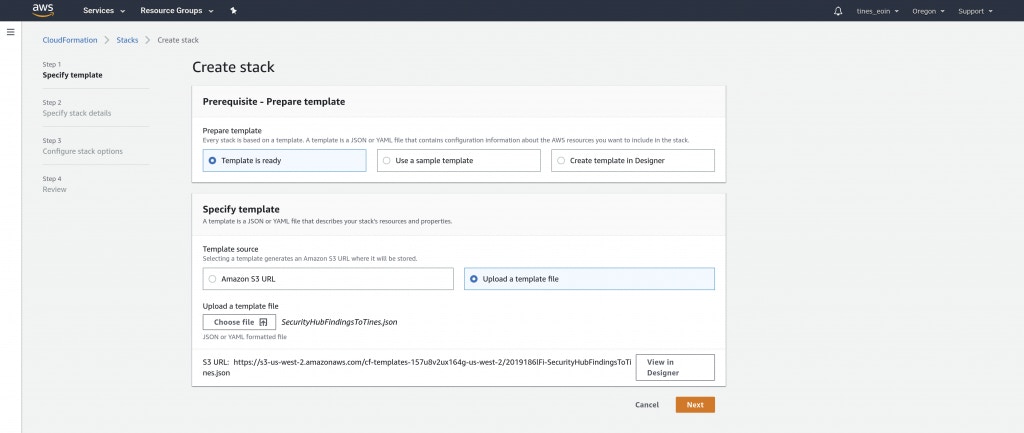
Once you have uploaded the file, click Next and give the stack a name, then provide the following parameters:
TinesWebhookURL: The Webhook URL is taken from the Receive AWS Security Hub Notification.
After selecting Create Stack, CloudFormation will begin creating the stack. When CloudFormation is finished creating the stack, it sends a new SNS Subscription Confirmation Event to Tines (sample below).
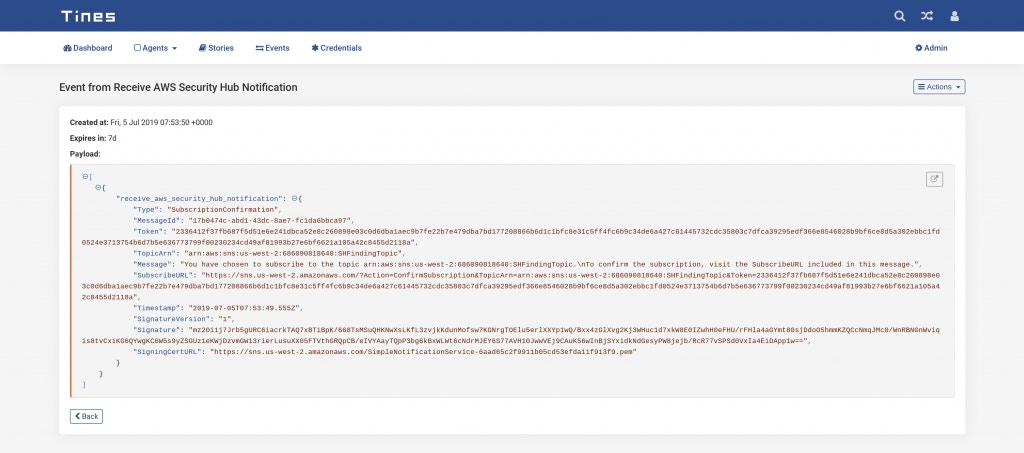
AWS Security Hub SNS Subscribe Confirmation event in Tines
We’ve configured the Confirm subscription HTTP Request Action to send a GET request to the SubscribeURL defined by SNS. This confirms the SNS subscription so Security Hub so it will now send Findings to Tines.
Receiving AWS Notifications in Tines
You should now have everything needed to begin automating responses to Security Hub Findings in Tines. When Security Hub triggers a Finding, it will send a notification event to the Tines Webhook Action. A sample event is shown below:
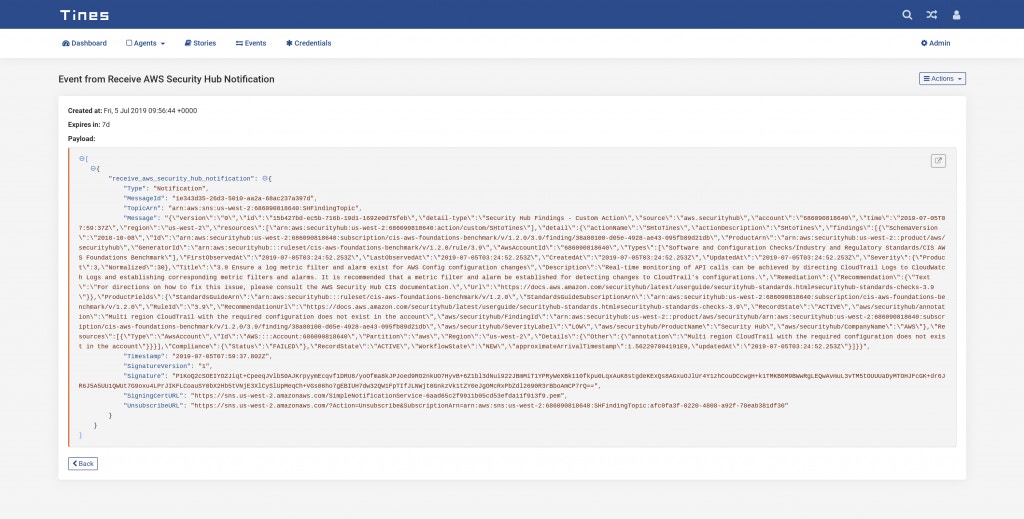
AWS Security Hub Notification event in Tines Security Automation Platform
The important information describing the Security Hub finding is in an escaped JSON string, this makes further automation challenging. To parse this string into a “friendlier” format, we use the Liquid Filter json_parse in a message_only mode Event Transformation Action.
Events emitted by this Action will contain the finding’s details in a format we can easily use in Tines to further enrich, deduplicate, prioritize and even automatically remediate the finding.
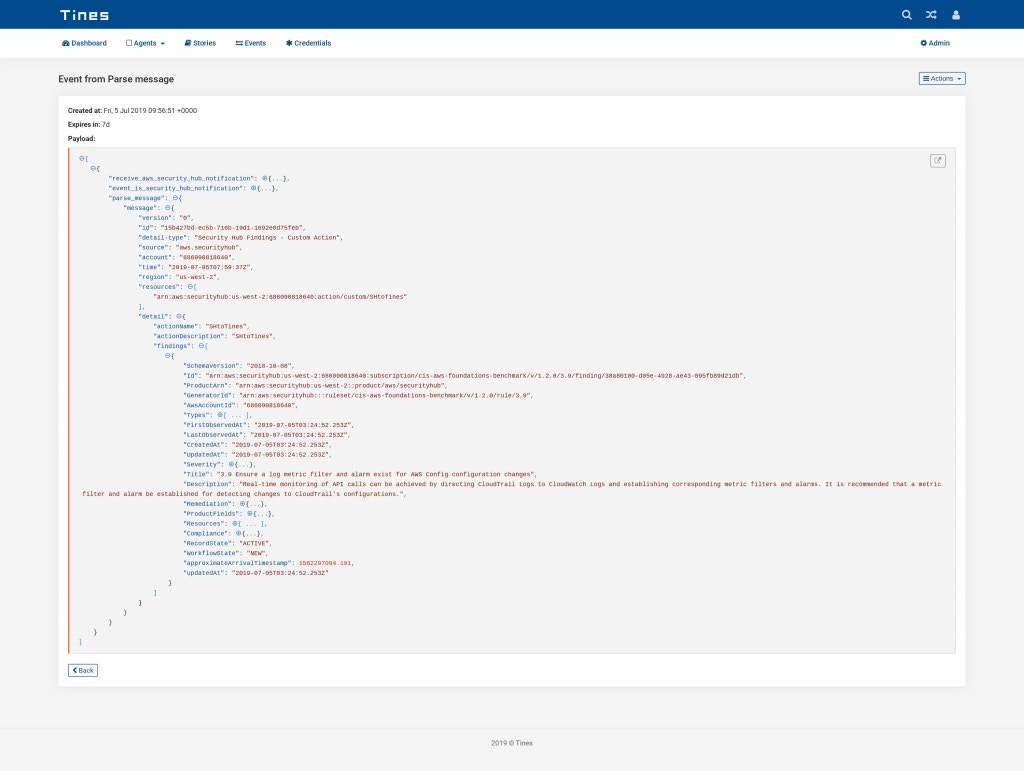
*Please note we recently updated our terminology. Our "agents" are now known as "Actions," but some visuals might not reflect this.*