A partner blog between Phish.ai and Tines.com
[End of life notice: please note, Phish.ai is no longer available.]
According to the latest Verizon Data Breach report Phishing is involved in 93% of breaches and email continues to be the most common vector (96%) in successful cyberattacks [0]. These figures indicate that malicious email detection software and employee security awareness training are no longer sufficient on their own to deal with the volume of attacks, even on a small scale. In addition, the process to review suspicious emails and examine suspicious URLs is both time-consuming and error-prone. Furthermore is one of the most frequent causes of alert overload and analyst fatigue. Phishing Automation using SOAR platforms like Tines and Phishing analysis tools like phish.ai helps companies tackle these problems.
In a world where detecting and responding to incidents quickly is a key metric for any security program, automating the collection and analysis of suspicious URLs can reduce mistakes and improve response times. Above all, it will make your analysts more efficient, effective, and happier.
What steps should I take to automate the analysis of suspicious URLs?
The first step in building out automation is to identify sources for collecting suspicious URLs for your environment. Common sources of malicious URLs include:
Customer Abuse boxes (You can read more about using Tines to manage your Abuse Inbox here)
URLs blocked by your email security solution like Proofpoint, FireEye ETP, Barracuda, Mimecast, or Microsoft APT.
DMARC failures or rejects
Suspicious uncategorized or punycode URLs from your firewall logs or DNS logs
New SSL Certificates registered with domains similar to your brand (e.g. from crt.sh)
Threat Intel sources like the Phish.ai threat intel feed which generates feeds based on the brands attacked
Free feeds of malicious URLs like Phishtank, Openphish, phishstats.info or Urlhaus. Note, these feeds are often are high-reputation so don’t necessarily need to be further analyzed.
Using Tines’ Phishing Story it’s easy to collect suspicious URLs from over a dozen of different sources automatically. Once these feeds are in Tines it’s easy to deduplicate and classify URLs to prevent alert overload and to generate more accurate metrics.
Once Tines has deduplicated the URL feed, it’s time to perform a real-time URL analysis using a tool like phish.ai.
Phish.ai is a premium service that proactively indexes websites of top brands around the world to create an up-to-date computer vision database. Phish.ai’s real-time web crawler will index all URLs submitted and compare the site image against the known bad database. (Note, to submit privately you’ll need to sign up for a basic plan. Basic plans allow scanning of up to 10,000 URLs each month).
Integrating Phish.ai with Tines in your phishing automation process
With Tines, it’s simple to make a single API call to submit these URLs for analysis using Phish.ai’s API. The configuration to make these calls in Tines is below, using an “HTTP Post Request Action”. In this example, {{.explode_urls-array.url}} represents the URL to be sent for analysis. Moreover, this can be done in a totally secure manner. The parameter {% credential phish_ai %} is the phish.ai API key which is encrypted and sent along with the request.
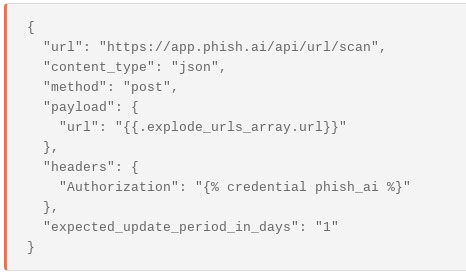
A HTTP Request Agent configuration to submit urls to phish.ai
This request returns a unique “scan_id” parameter:
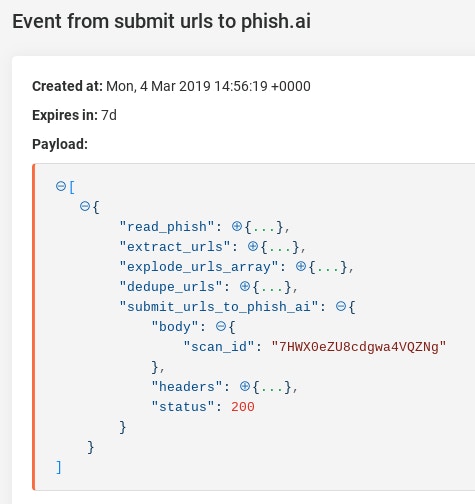
In the next step, Tines sends this parameter to Phish.ai to retrieve the results of the analysis. Similar to the request above, an HTTP Request Action is used.
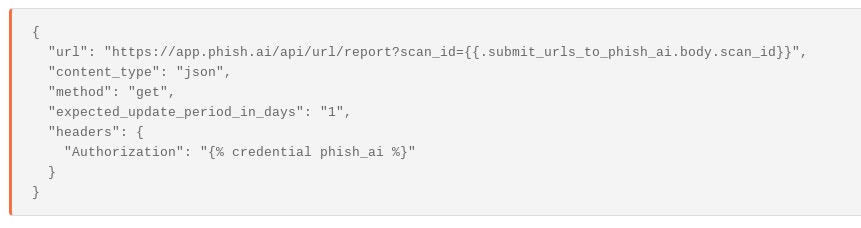
This call returns the results of the analysis by Phish.ai:
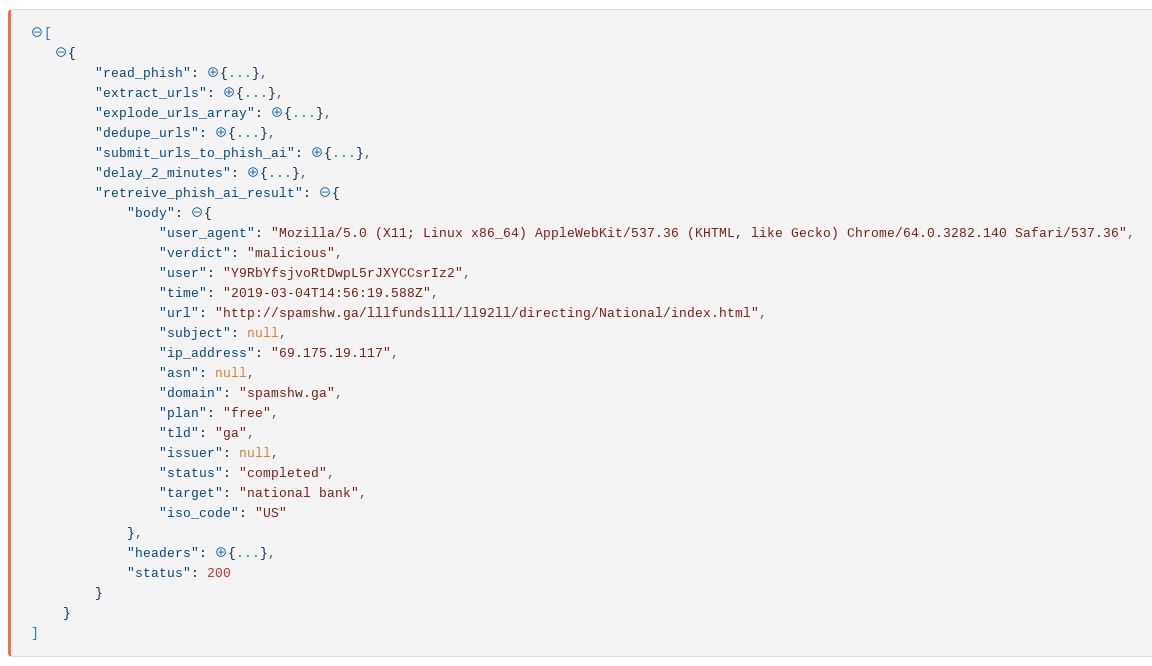
In the background, phish.ai has compared the image of the crawled page against its collection of known bad images. Subsequently, phish.ai has correctly detected that this particular site submitted through Tines is a phishing website. In the event emitted above, not only has phish.ai has successfully identified the site as malicious, it has also identified the target as “National Bank”. Importantly, this information can also be used to help analysts decide on the priority of an incident. For example, this information can help analysts identify more targeted attacks or phishing using brands used by employees.
Analysts can also use the phish.ai dashboard to view more information about the detection or a screenshot of the phishing page.
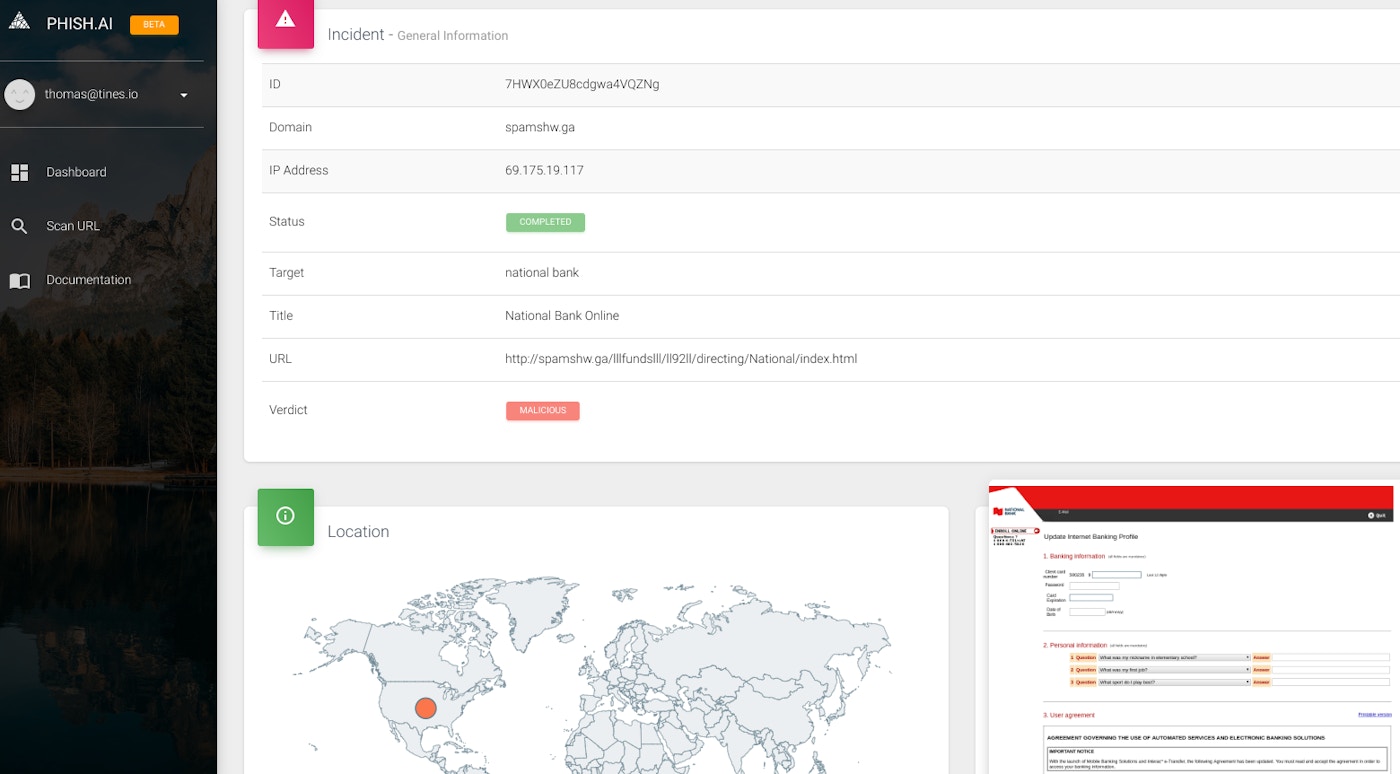
The phish.ai Dashboard UI
What’s Next?
Once your phishing automation process has completed an analysis of the phishing URL it’s possible to automate dozens of other interactions in Tines.io. For instance, traditional next steps include scanning for any traffic to the identified malicious in firewall logs and endpoint logs etc.; blocking the domain; removing the particular email from inboxes; performing a header analysis etc. Other companies also use Tines to respond to reporters confirming a site is malicious. Another popular use case is to use phish.ai’s threat feeds in combination with other public and private feeds to detect brand abuse and send takedown notices to hosts requesting they remove the infringing content.
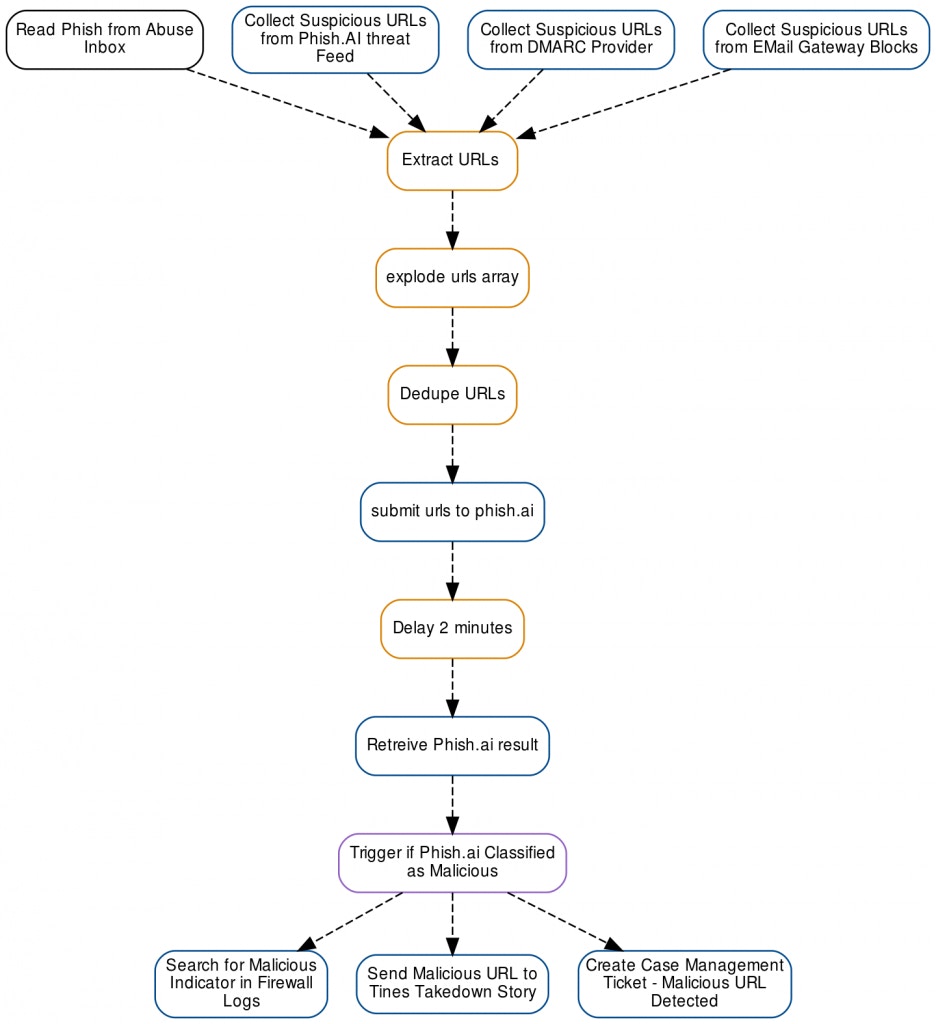
An excerpt from the Tines Phishing Automation Story
In conclusion, Phishing Automation using a no-code security automation platform like Tines in combination with a real-time phishing analysis platform like Phish.ai, can help your security team scale and keep your analysts focused on more impactful efforts, leaving them happier.
You can read more about this step in the process in part three of our “automating your abuse inbox” blog series.
*Please note we recently updated our terminology. Our "agents" are now known as "Actions," but some visuals might not reflect this.*
—
To date, Phish.ai has scanned over 21 million URLs and identified over 85,000 zero day phishing attacks. You can read more about the Phish.ai api here.
Tines.io is an Security Orchestration, Automation and Response (SOAR) platform used by Fortune 10 companies, global banks and large public and private SaaS companies.
[0] Verizon Data Breach Investigations Report 2018