This blog post was originally published in February 2019 on the Carbon Black Blog.
Tines was founded by former DocuSign and eBay security engineers who were frustrated by existing security automation platforms. “I was leading an enterprise security team that had to work harder and harder every day just to keep up with the volume of alerts that required investigation,” said Eoin Hinchy, founder of Tines.
“We had talented engineers on our team, but we needed them focused on higher-impact engineering efforts. So, we started exploring tools that would allow analysts without coding or engineering backgrounds to automate their manual workloads.”
These workloads involved staples of incident investigation and triage: activities such as performing log searches, analyzing suspicious emails, and running vulnerability scans.
After spending months piloting various security orchestration automation and response (SOAR) platforms, a pattern began to emerge.
“Every SOAR platform we looked at had the same problems. They used prebuilt app-based integrations to interact with a limited number of tools, and these integrations would expose only a limited set of features in each tool. In addition, app-based integrations meant that it was difficult to connect with tools we’d built or deployed ourselves without engaging a software engineer or the SOAR vendor’s professional services team. That wasn’t good enough for what we needed to do.”
From this frustration, Tines was born, said Eoin.
“Simply put, our goal when founding Tines was to build the SOAR platform we wished we’d had when we worked in enterprise security. One that could automate any manual workflow regardless of complexity or technology stack, and that didn’t require any coding skills to operate.”
What should I automate first?
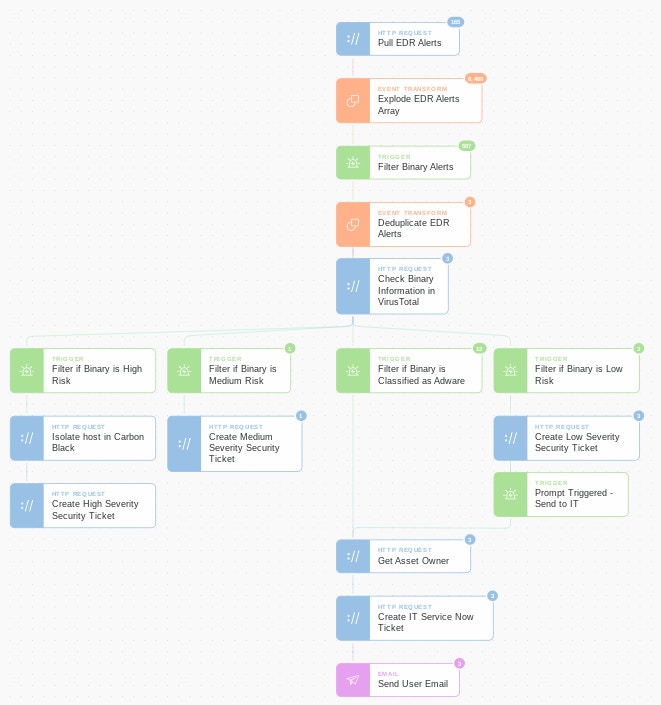
Customers can quickly see the value in SOAR platforms by letting their analysts automate their most frequent incidents and repeatable tasks. A great example is adware, which is detected in Carbon Black customer environments multiple times per week.
“Analysts shouldn’t be spending time on low-severity incidents, but those incidents still require investigation and are one of the main causes of alert overload,” explained Eoin.
“With Tines, it’s very simple for analysts to create a flow to deduplicate incidents and to enrich detections with binary information to see if the binary is classified as adware. If it is, then the analyst can set up Tines to automatically send the incident details to IT for remediation – there’s no need for infosec to get involved. You’d be surprised – we’ve seen analysts with no coding background automate a process in just a few hours that immediately freed up 10-20% of their time.”
Eoin said other examples of time-consuming tasks that analysts can start automating immediately include noisy live-off-the-land tool detections, crowdsourcing suspicious VPN or email activity, processing vulnerability scan results and handling mailbox abuse.
Does Tines integrate with other security tools?
Carbon Black is one of the thousands of tools Tines integrates with, “but it’s definitely one of our favorites,” said Eoin.
“Through our direct technology integration, our customers can connect with every tool in their technology stack. There’s no need to wait for a vendor to build an integration or to build one yourself.”
According to Eoin, Tines’ out-of-the-box phishing story is one example of this.
“Phishing automation is one of our most popular use cases. Our customers use Tines to pull in suspicious URLs from over a dozen sources – like their threat intel feeds, phishtank, their DMARC failures, abuse inbox emails, etc. – each with just a single agent and no custom integrations. From there, Tines can scan the URLs in a real-time classifier and leverage Carbon Black to hunt for malicious traffic. And then, some companies publicly share all malicious URLs they detect to keep the wider community safe. It’s inspiring!”
How customized can Tines Stories get?
“You can get endlessly more sophisticated,” says Eoin. “Let’s walk through a more complicated scenario.
“Although we pride ourselves on creating a tool that analysts with no coding skills can use, you can also create complex scenarios with hundreds of steps involving dozens of tools. For example, Macro-Enabled Malware has been a scourge for 25 years, but while it’s easy to create alerts in Carbon Black to detect it, responding is still time-consuming. We’ve known for years what steps we should take, we were just unable to automate them.
“When a Macro-Enabled Malware alert is sent to the Tines platform, it automates the containment while getting the information in front of the analyst as quickly as possible. After deduplication, Tines can leverage CB Response to quarantine the machine, kill processes and force full-sensor syncs, as well as send files for analysis to a sandbox. Customers can then use Tines to automate standard remediation actions like contacting users, informing IT, banning payload hashes, or blocking IOCs in firewalls or other security tools,” added Eoin.
What other capabilities are available when using Tines with Carbon Black?
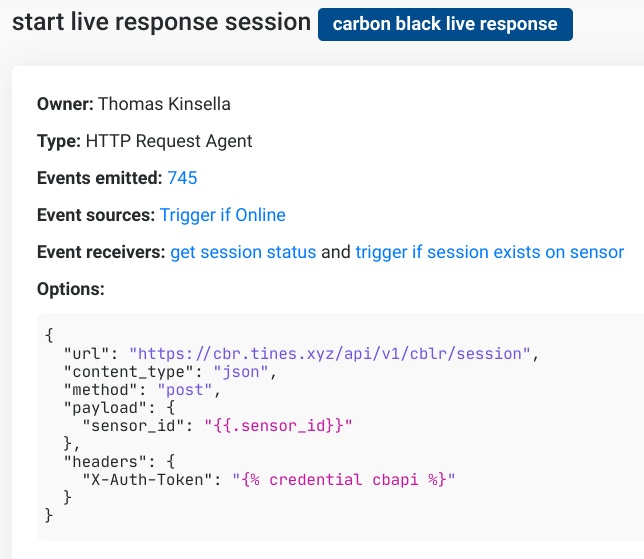
Carbon Black offers one of the best tools for detecting and responding to endpoint threats, but the key selling point for Tines was their open APIs. Because Tines doesn’t use any pre-built integrations, customers have more flexibility and extensibility to exploit the full power of Carbon Black because of the robust set of open APIs.
“The CB Response API exposes over 250 actions, which means using Tines, customers can isolate machines, force full sensor syncs, download or upload files, update watchlists and kill processes, along with 245 additional actions – hundreds more than other orchestration platforms,” said Eoin.
He added, “We have teams in companies from major banks to Fortune 5 companies doing everything from crowdsourcing suspicious employee activity reports, automating cleanup and evidence handling, vulnerability scanning, threat hunting, standardizing detections across tools, sharing intelligence, and some customers are even automating their compliance processes using Tines.”
To learn more about Tines integration with Carbon Black, visit their page on the Carbon Black Partner Locator. You can also download and import this Story from our Story Library.