In the last few days, Google began rolling out the G Suite Alert Center to all G Suite customers. It provides extensive visibility into threats detected in G Suite tenants. In this post, we explore how G Suite administrators and security teams can leverage security orchestration automation and response (SOAR) platforms, like Tines, to centralize, triage, and respond to alerts from the G Suite Alert Center.
What is the G Suite Alert Center?
When Google announced the launch of G Suite Alert Center it was with the stated aim of providing “a single, comprehensive view of essential notifications, alerts, and actions across G Suite”. Admins can manage alerts more efficiently through the unified view that the alert center provides. Additionally, it provides insights that help them assess their organization’s exposure to internal and external security issues at the domain and user levels.
Out of the box, G Suite Alert Center includes the following types of alerts:
Accessing G Suite Alert Center
When logged into the G Suite Admin portal, click “Security” and then choose “Alert Center”.
Accessing the G Suite Alert Center
On the next page, the G Suite Alert center displays all the alerts for your G Suite tenant. From this view, G Suite admins can view details of the alerts. Additionally, G Suite customers on the Enterprise plan can perform remediation actions from within the G Suite Alert Center itself. Later in this post, we’ll show how Tines can be used to automate the same remediation actions in real-time regardless of your G Suite plan.
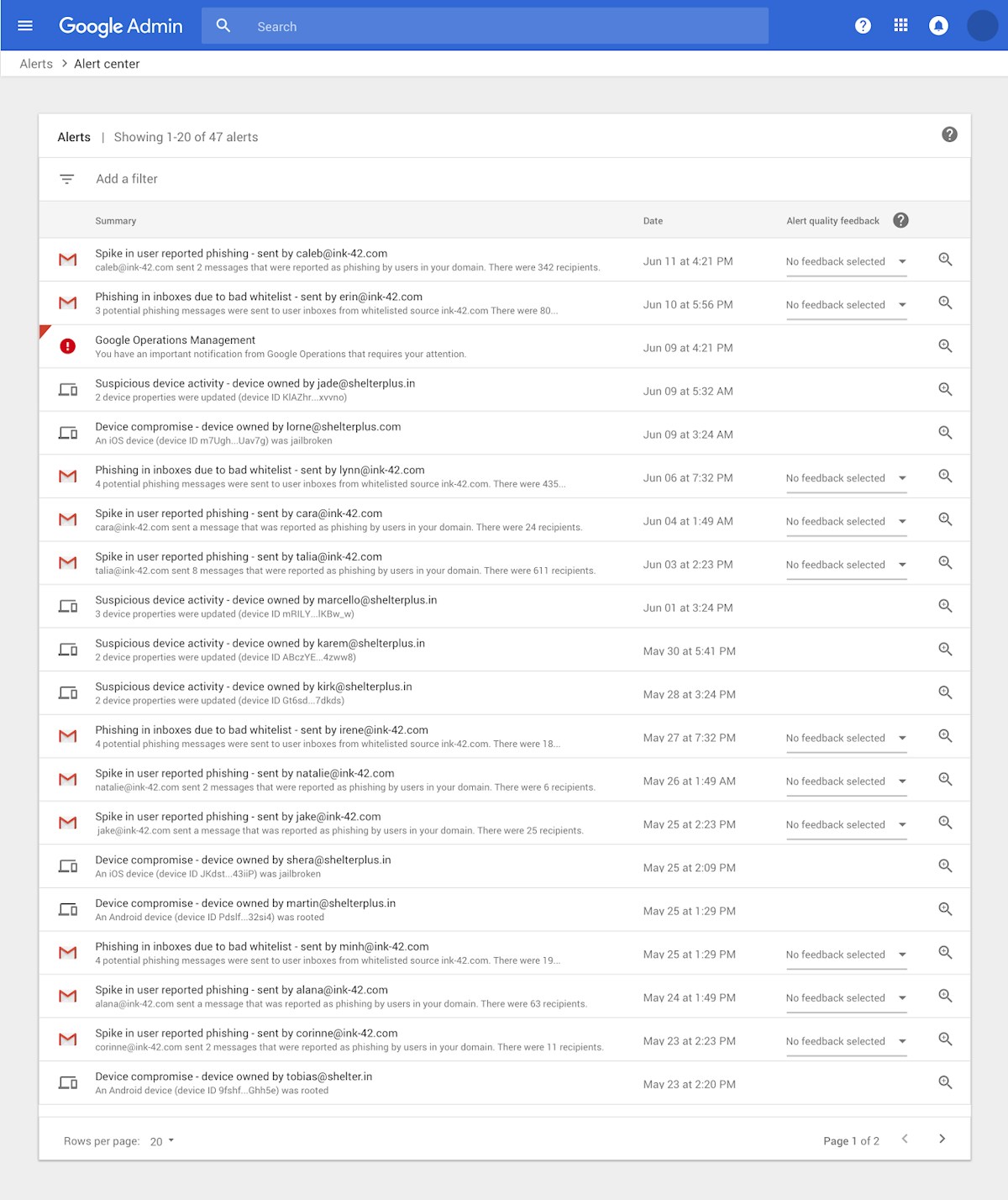
G Suite Alert Center Screenshot
Tines and the G Suite Alert Center
The alerts produced by the G Suite Alert Center provide valuable insight into potential security issues in G Suite tenants. However, the alerts are at their most valuable when, rather than being treated in isolation, we include them as part of a larger threat detection and response effort. By automating interaction with the G Suite Alert Center through Tines, we can use the alerts as both a threat source and as a source of additional context when investigating other incident types. By using Tines to integrate with the G Suite Alert Center, we’re also centralizing our response and aligning it to existing security response processes.
Connecting Tines to the G Suite Alert Center
In a previous blog post, we described the steps required to connect Tines to G Suite, we’ll use a similar method to connect to the Alert Center.
Enabling the G Suite Alert Center API
Follow these steps, based on those from developers.google.com to set up the Alert Center API:
Create a service account that can be used by your G Suite application (see instructions on creating a service account).
Download the key file, it will be a JSON file containing your private key and other sensitive information.
G Suite Service Account Key File
Enable the Alert Center API (for instructions, see the section on enabling and disabling APIs).
Enable G Suite Alert Center API
Authorizing the service account
In order for Tines to access user data in G Suite, a G Suite administrator needs to authorize the account we just created in the G Suite admin console, this is a process known as delegating domain-wide authority.
Go to your G Suite domain’s Admin console.
Select Security from the list of controls. If you don’t see Security listed, select More controls from the gray bar at the bottom of the page, then select Security from the list of controls. If you can’t see the controls, make sure you’re signed in as an administrator for the domain.
Select Show more and then Advanced settings from the list of options.
Select “API Controls" and then "Manage Domain Wide Delegation."
Select "Add New" to add your Client ID and OAuth Scopes.
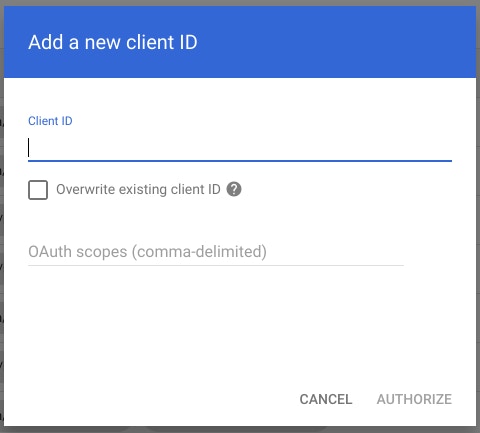
In the OAuth Scopes field, enter the list of scopes to which your application should be granted access. In this case, type the following value: https://www.googleapis.com/auth/apps.alerts.
Click authorize.
Creating a Tines Credential
Before Tines can connect to the G Suite Alert Center API, we need to configure a JWT credential type. For detailed instructions on how to use JWTs with G Suite, see here.
Use the information from your service account key file to fill in the required JWT fields. When you’re finished, the credential page will resemble the one below.
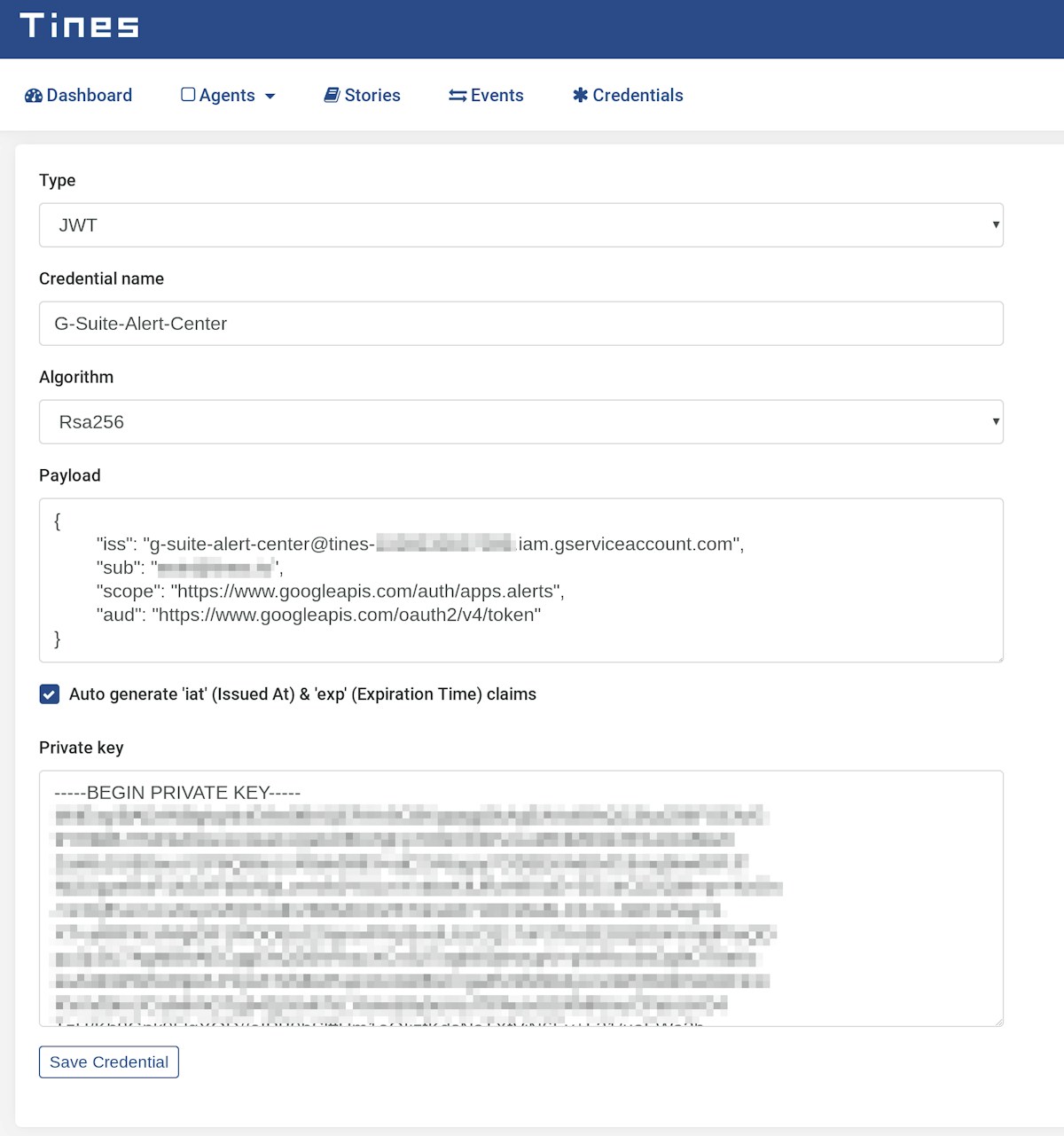
G Suite Alert Center Tines Credential
After saving the credential, we can begin automating interaction with the G Suite Alert Center.
G Suite Alert Center Automation Story
Get a G Suite Auth Token
To begin orchestrating and automating activities in the G Suite Alert Center, we first need to retrieve an auth token. This will allow us to interact with the Alert Center API. We’ll do this with an HTTP Request action, configured as shown below:
{
"url": "https://www.googleapis.com/oauth2/v4/token",
"content_type": "form",
"method": "post",
"payload": {
"grant_type": "urn:ietf:params:oauth:grant-type:jwt-bearer",
"assertion": "{% credential G-Suite-Alert-Center %}"
}
}When this Action runs, it will emit an event containing a bearer token which we will use in subsequent agents.
Get All Alerts from G Suite Alert Center
The G Suite Alert Center API is available at https://alertcenter.googleapis.com. We’ll use the list call in an HTTP Request Action to get all alerts associated with our G Suite tenant.
When this Action runs and there are alerts in our tenant, the G Suite Alert Center API will return an array of alerts.
Get alerts in last five minutes
Additionally, we can use filters to find alerts that match certain criteria. For example, the below HTTP Request Action uses the date liquid filter to find alerts created in the last 5 minutes (current time in seconds – 300 seconds, converted into Google’s preferred Timestamp format: RFC 3339).
{
"url": "https://alertcenter.googleapis.com/v1beta1/alerts",
"method": "get",
"headers": {
"Authorization": "Bearer {{.get_g_suite_auth_token.body.access_token}}"
}
"payload": {
"filter": "create_time >= \"{{ \"now\" | date: \"%s\" | minus: 300 | date: \"%Y-%m-%dT%TZ\" }}\""
}
}Get alert details from the G Suite Alert Center API
We can also use an HTTP Request Action configured as below to find details about a specific alert, using its ID.
{
"url": "https://alertcenter.googleapis.com/v1beta1/alerts/{{.explode_alerts.alert.alertId}}",
"method": "get",
"headers": {
"Authorization": "Bearer {{.get_g_suite_auth_token.body.access_token}}"
}
}A sample automation Story
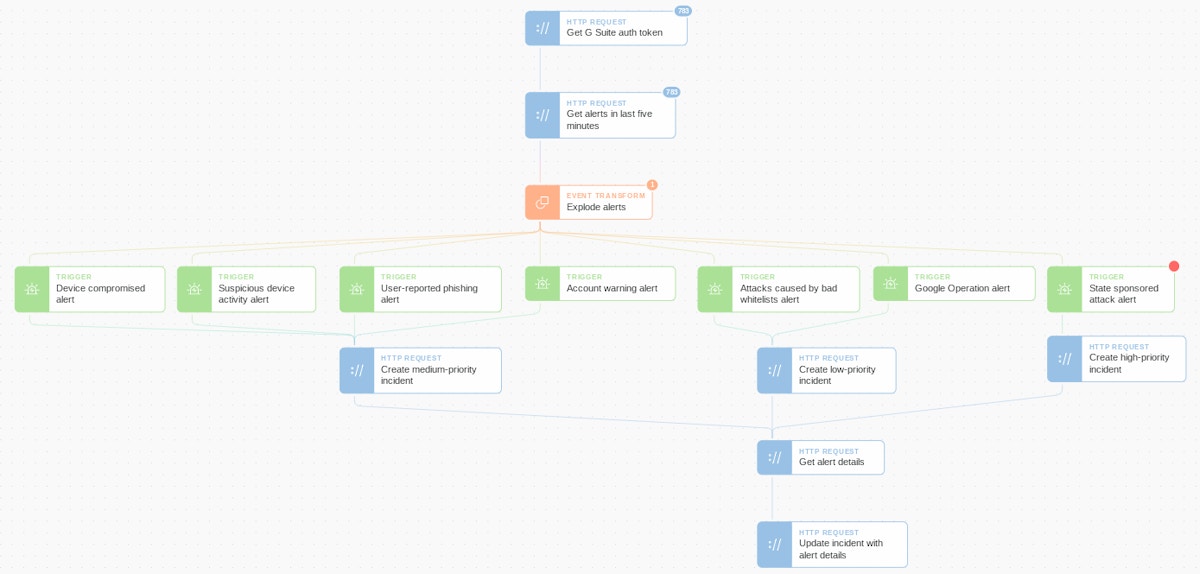
In the above automation Story, we’ve created a blueprint for getting started with the automatic handling of G Suite Alert Center threats. To begin, at five-minute intervals, we fetch all alerts. Next, an Event Transformation Action is used to explode the array of alerts so each alert can be treated individually. Then we use several Trigger Actions to emit events based on the alert type. Finally, we create an incident ticket based on the alert’s priority (this could be in Jira or another case management system) and add the alert's details to the ticket.
From here, it would be trivial to add additional threat intelligence sources or automate data gathering log searches in a SIEM. We could also automate remediation activity like blocking malicious senders, quarantining devices, and resetting compromised accounts all without requiring human intervention.
Conclusion
When considering threat detection tools for their technology stack, it’s easy for security operation teams and security operation centers to overlook assets like the G Suite Alert Center. However, as enterprises continue their move to the cloud, these non-traditional sources of threat intelligence and security alerts are becoming increasingly valuable.
By using security automation and orchestration tools like Tines to respond to threats surfaced by data sources similar to the G Suite Alert Center, an enterprise incident response team can ensure their standardized workflow is followed. Additionally, their detection and response are smarter, quicker, and less prone to human error.
*Please note we recently updated our terminology. Our "agents" are now known as "Actions," but some visuals might not reflect this.*