Tines is a flexible security automation platform that provides a wealth of opportunity to replace manual tasks and quickly build the infrastructure needed to create impactful security solutions. Through our Community Edition, we provide the ability to publish 3 workflows, which can be used to implement ideas nearly unlimited in scope or complexity (fair usage limits apply). Words like unlimited, open, or unbound can sometimes be overwhelming when you're just getting started with something. Sure there are endless possibilities, but who is to say what could be done first?
Motivation often comes after starting, not before. Action produces momentum.
- James Clear
Here are three workflows that Tines enables, which have been proven to save teams countless hours of their day and can be implemented with our Community Edition.
1. Embrace ChatOps
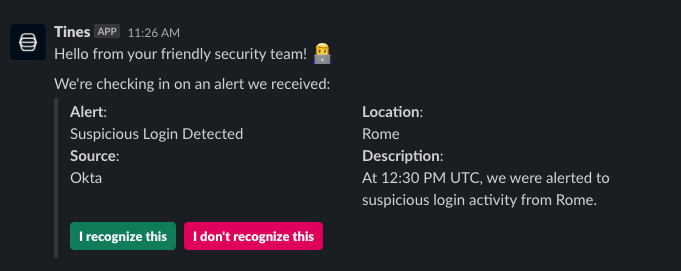
Cybersecurity teams spend countless hours reaching out to people and their managers to get the full context of a security alert. It is not just the effort involved in looking up a person's contact information and sending the message, but also waiting for a response, potentially escalating to other individuals, or even just forgetting to follow up on the message, which consumes valuable time. ChatOps can reduce the load on your security team, provide individuals their own response options, and extend out services to a common chat interface. Worried about compromised accounts responding? Go a bit further and send a push notification to a user's multi-factor authentication application.
Check out this Story and Slack Bot manifest, which enables sending a crafted message in Slack to a user and awaiting a response for an hour before taking additional action.
2. Enrich More than Just IoCs
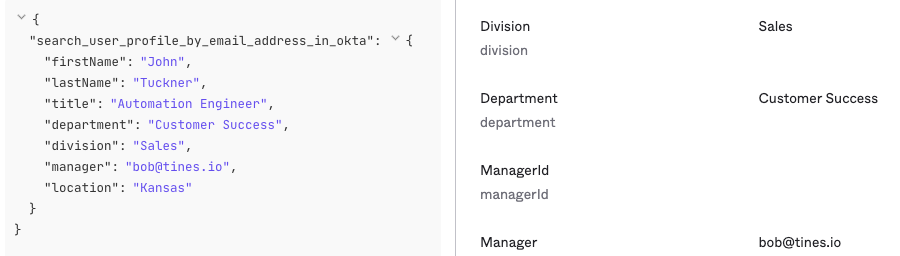
Enriching indicators of compromise like hashes, IP addresses, and domains with current information is critical to the success of any cybersecurity team. Don't stop there! Utilizing all sources of information in your organization can lead to surprising efficiencies. For example, lookup user information in directories like Okta, find computer asset details present in Google Sheets, search SIEM platforms for a sample of logs files that occurred around the time of an alert, or find knowledge base articles in Notion for any prior research that relates to an alert.
Looking up individuals in Okta's directory is incredibly simple, and this Story helps identify any regional logins that might be out of the norm for a user.
3. Account for Your Alert Budget
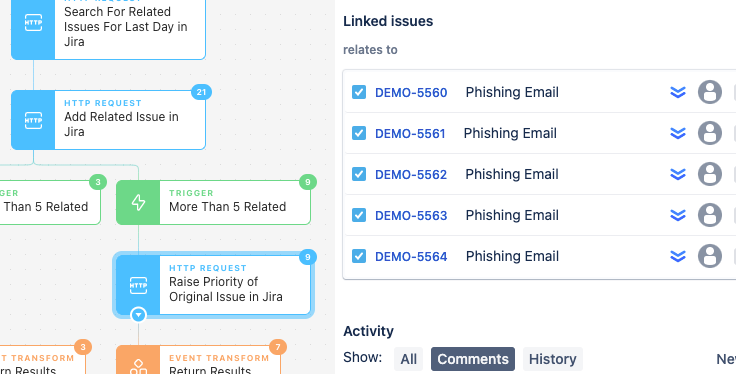
We should all accept that every cybersecurity team has an alert budget. There is a maximum number of issues that can be triaged in a day before tradeoffs in quality and risk start being made. Even without a clear (or maybe any) idea of how to handle each alert that comes in, there are opportunities to make savings by creating tracking tickets immediately and joining related tickets together or increasing the priority of repeated issues.
Using Jira and a workflow similar to this Story, teams can establish those reliable audit trails and the critical data points needed to address capacity issues when a team goes over its budget.