Professionals working in cyber threat intelligence (CTI) overwhelmingly enjoy their jobs; over 66%, according to a limited survey of CTI professionals. They enjoy playing detective, investigator, researcher, analyzer, and communicator.
What do they not love about the job? Chasing down bits and pieces of information manually through tons of different interfaces. Wrangling a time-intensive monstrosity of various files, web pages, and inconsistent formats, then merging them (ungracefully).
According to SANS Institute’s 2022 CTI Survey, 44% of CTI teams are still using spreadsheets as the top tool, while 56% of threat intelligence platform users rely on some form of a homegrown solution. Similarly, 64% of SOC analysts report spending more than half their time on tedious work, and automatically receiving richer context for intelligence analysis is a "Top 5" focus area to save the most time.
These existing challenges underpin the key needs of CTI teams moving forward: improved collaboration, formalizing analysis processes, and optimizing/standardizing those processes with tools and systems.
Check your pulse
There’s a better way to get answers for some of the most common questions that can tip off more strategic (read: exciting, fulfilling, meaningful) threat intelligence research. Hybrid automation helps to replace the tedious, repetitive technical collection and contextualization steps to get to the "good stuff" where the security professional shines.
This formula can be summed up as Pulsedive + Tines = a better time. Even more, you can start for free, with no ticking time limit.

From IOC “enhance” to “thank you, next”
There’s nothing worse than getting an alert with nothing but the IOC and a flag. Then, running a lookup to uncover a slice of useful context to help make a determination, with no source or timestamp. And then not being able to dig into the raw data to dive deeper. Roadblocks each step of the way triggers the opening of a minimum of three new tabs. Where did it come from? Where did it go?
This is where the most essential enrichment workflow using Actions like 'Search Indicators in Pulsedive' and 'Scan an Indicator in Pulsedive' helps an analyst skip multiple steps in real-time.
Here’s an example that allows you to extract IOCs, search and analyze them in Pulsedive, and send an email with results.
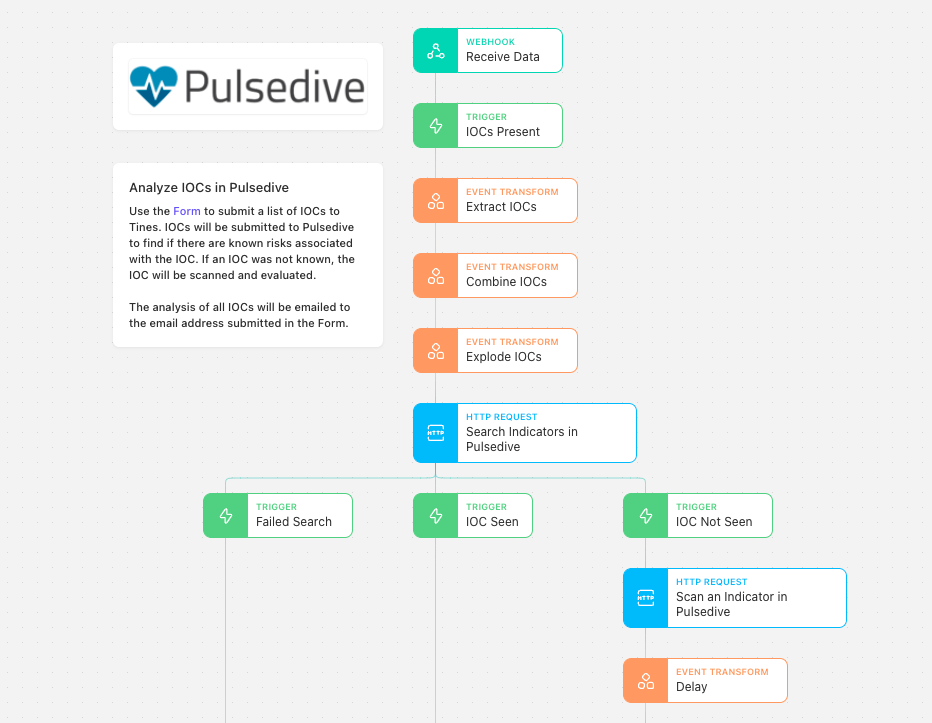
A Form is available to users to submit IOCs and an email address to send the report to. This means you can likely copy a number of indicators from a spreadsheet or report and simply paste them into Tines for analysis. Tines will identify each IOC as an IP address or URL and check to see if each is listed within Pulsedive already. If an indicator is not currently listed, Pulsedive will scan the indicator to retrieve more information about it if possible during the analysis.
Note: Scanning an indicator that is not already in Pulsedive does not mean submitting it to the database, and the indicator data will not be cached.
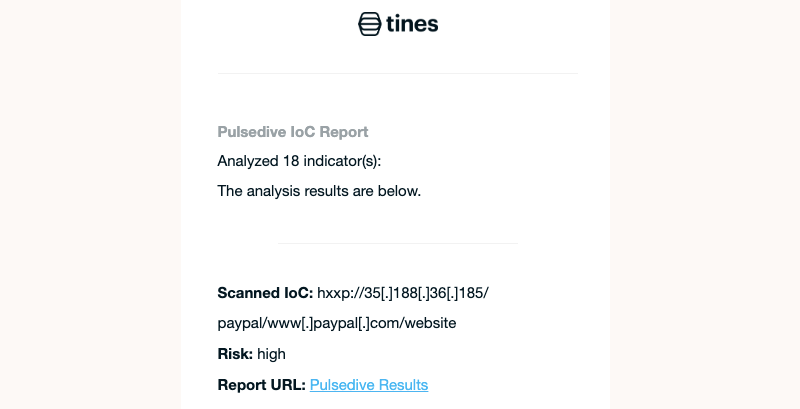
Once well acquainted with Tines and Pulsedive, extend the Story to analyze indicators sent in from Slack or use additional data points like domain registration info from Pulsedive.
Dive in
With the Pulsedive and Tines integration, it’s easy to share, enrich, and scan IOCs. This is one small example of what can be accomplished as you develop workflows that fit your threat intelligence playbook that underpin your security program.
Start for free with both Tines and Pulsedive's Community tiers and upgrade as you grow. To use and customize the above automation Story, import it via our Story Libary preview below.
Loading story...