Phishing has been the number one cause of breaches since... well... forever. Which is why security teams invest enormous amounts of time and energy advising employees on what to do when a suspicious email lands in their inbox. This advice is usually some variation of: “If you receive an unsolicited email that seems suspicious, don’t click any links and don’t open any attachments. Forward it to the security team for analysis.”
For security teams across the world, analyzing employee-reported phishing emails is a manual, time-consuming process that detracts from other, higher-impact and more engaging work.
Today we’re excited to announce Phish.ly, a free service, built in partnership with urlscan, that helps address this challenge by automating the analysis of suspicious emails.
How it works
When you send a suspicious email to scan@phish.ly, either forwarded inline or as an attachment, the below Tines Story runs.

Phish.ly Tines automation Story
The Story extracts all URLs in the suspicious email and submits them to urlscan. Once urlscan has finished analysing the URLs, Tines sends you a comprehensive report with information including:
Overall classification of the email
Sender reputation
List of all analyzed URLs with links to urlscan
List of all attachments with links to VirusTotal
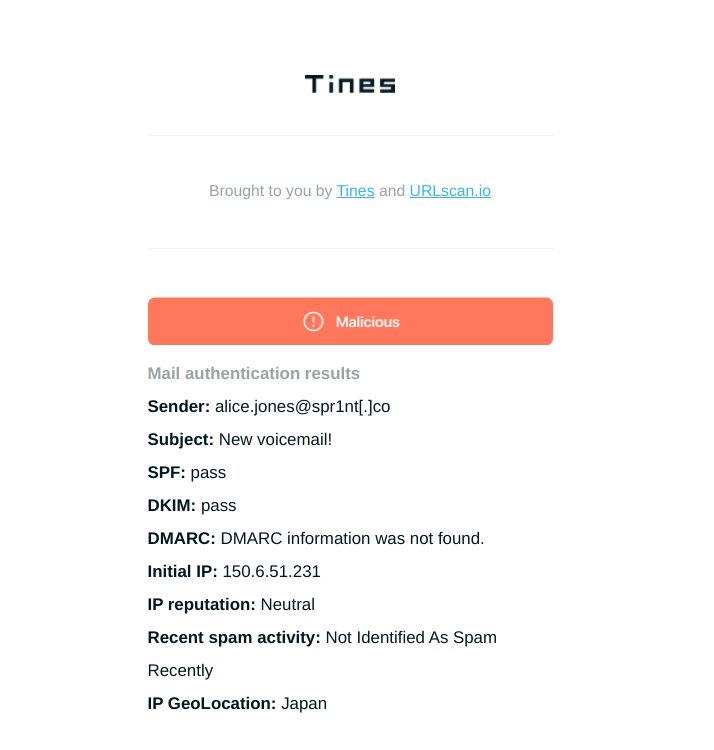
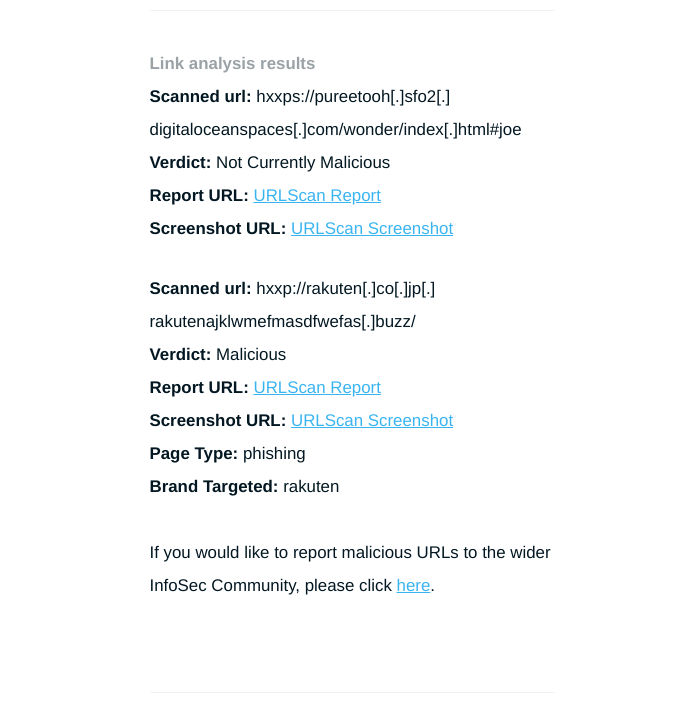
Sample Phish.ly report for a suspicious email
Sharing malicious indicators with the community
We’ve written previously about the value of sharing malicious indicators with the wider InfoSec community. When you send a malicious email to phish.ly, the report contains an option to automatically share the links with various open-source threat intel providers.
When you click this link, a Tines prompt is executed and sent to TinesBot for distribution to the wider InfoSec community.
What's next?
Try it! Visit Phish.ly or send a suspicious email to scan@phish.ly. If you want to examine, modify or expand on the automation Story powering Phish.ly, it’s available for download here. Simply import it into your existing Tines tenant or access our free Community Edition of Tines here.
If you have feedback, questions or suggestions on Phish.ly, contact feedback@tines.io.