Security teams often have key management systems that encrypt and securely hold their applications' credentials. Instead of entering these credentials into your automation Stories every time, you can leverage Tines to retrieve an application's credentials whenever you require them in a workflow.
Tines continues to expand our partnership with HashiCorp and allows mutual users to connect with the HCP Vault by using the AppRole authentication method. We've broken this tutorial into two sections:
Part one: Authenticating to HashiCorp Vault with AppRole
Part two: Retrieve Vault Secret
NOTE: For both parts, you must ensure the resources and credentials referenced within the plain code match the names of the resources and credentials you previously created for objects such as the Role ID and Secret ID. You will also still need to set the location of the token response field.
Part one: Authenticating to HashiCorp Vault with AppRole
Before being able to retrieve credentials, Tines must first authenticate to HashiCorp Vault to receive a token to make additional requests. You can use the cURL examples in HashiCorp Vault to configure the appropriate Tines credential. In this example, we’re going to walk through using the sample secret created by the Vault.
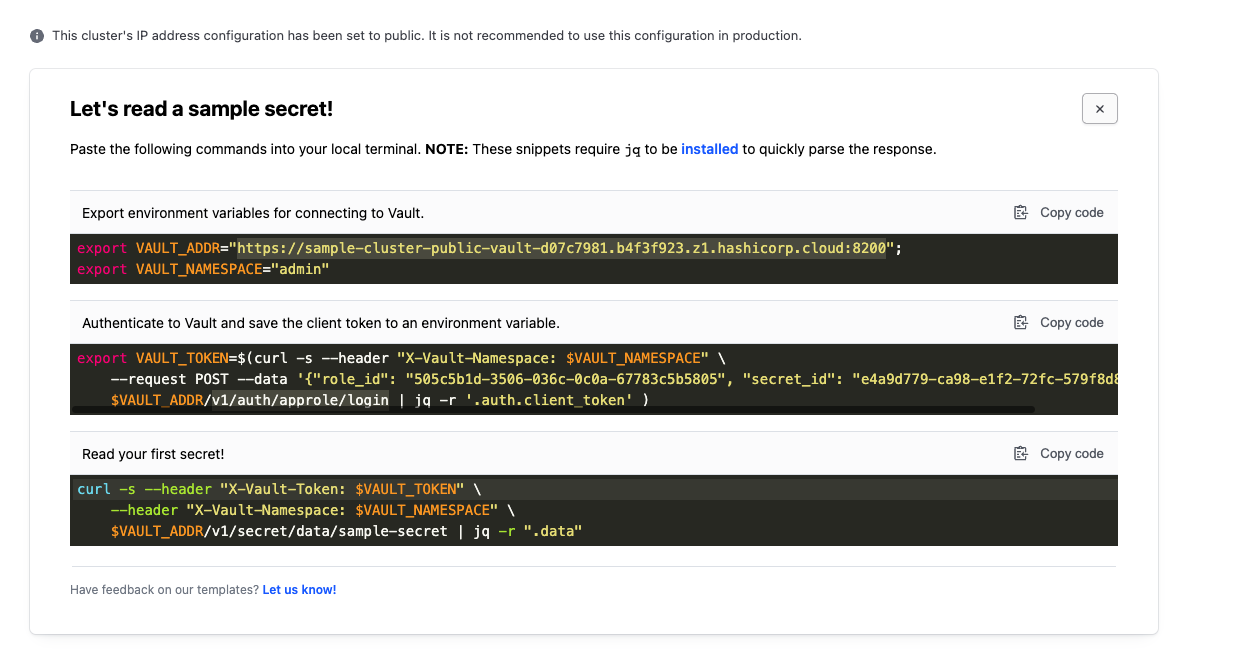
First, we recommend setting up resources for your Vault configurations:
Vault Address (
VAULT_ADDR)Vault Namespace (
VAULT_NAMESPACE)AppRole
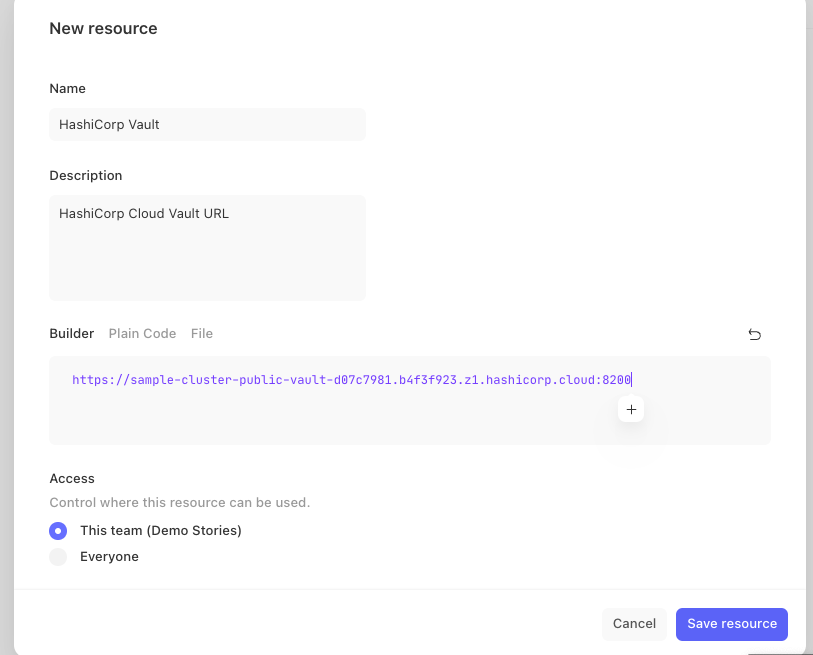
Example resource for Vault Address, VAULT_ADDR
Then, create the credentials for HashiCorp Vault following the relevant HashiCorp Vault instructions (see below reference links):
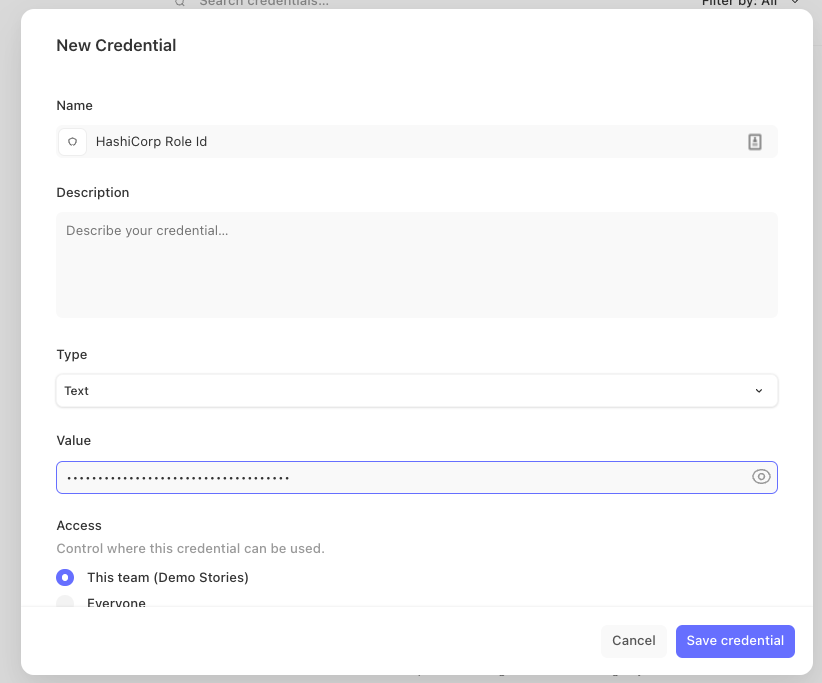
Example of configuring a credential in Tines for HashiCorp Vault Role ID
Configure the HTTP credential
Once you save these items as resources and credentials, you're ready to authenticate and use them for HashiCorp Vault. Configure the appropriate Tines HTTP credential for the Vault token so that the information mirrors the example below.
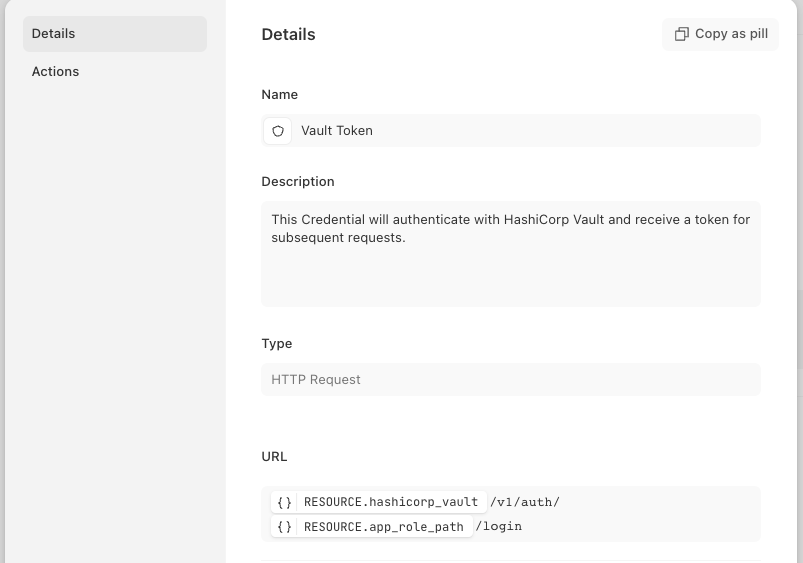

The final step is to identify the specific object from the Vault API data returned. To get the return data:
Click
run optionsto make an HTTP request to the VaultThen expand on the JSON data returned
Identify the
client_tokenobject underauthcontaining the AppRole tokeDouble-click
client_tokenPaste this information into the
location of the token from the responsefield
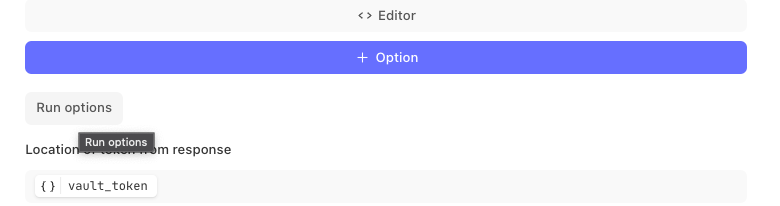
Click run options
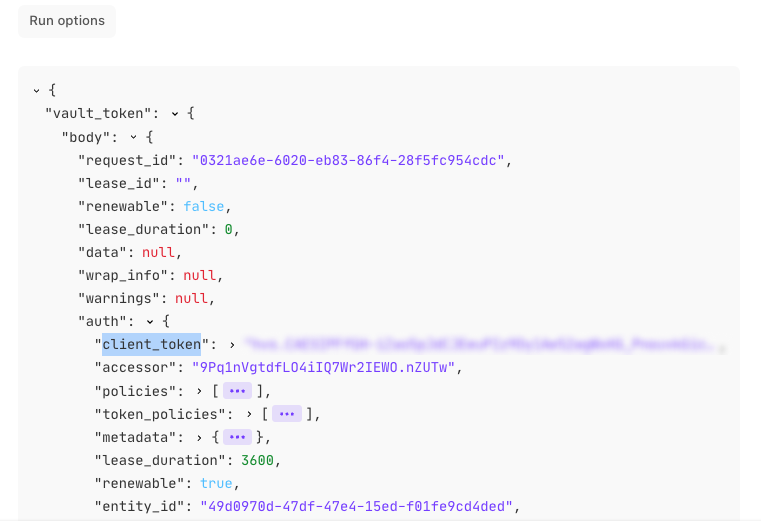
Expand the returned data and double-click client_token
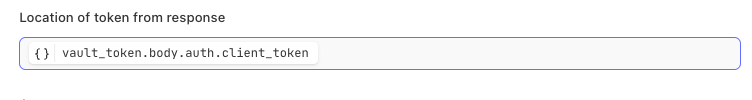
Paste client_token into the location field
Now when the credential HTTP request is executed the client_token will automatically be stored in the Tines HTTP credential you created for AppRole authentication.
Example
When creating a new credential to retrieve your Vault token, you can copy the example code below.
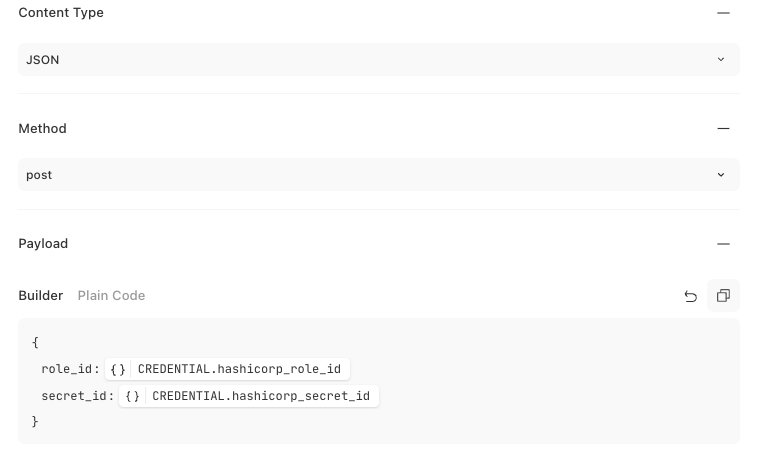
{
"url": "<<RESOURCE.hashicorp_vault>>/v1/auth/<<RESOURCE.app_role_path>>/login",
"content_type": "application_json",
"method": "post",
"payload": {
"role_id": "<<CREDENTIAL.hashicorp_role_id>>",
"secret_id": "<<CREDENTIAL.hashicorp_secret_id>>"
},
"headers": {
"X-Vault-Namespace": "<<RESOURCE.hashicorp_namespace>>"
}
}In your credential, navigate to the Editor section and click Editor.
Paste the code from this example over the code in the plain code of your new credential.
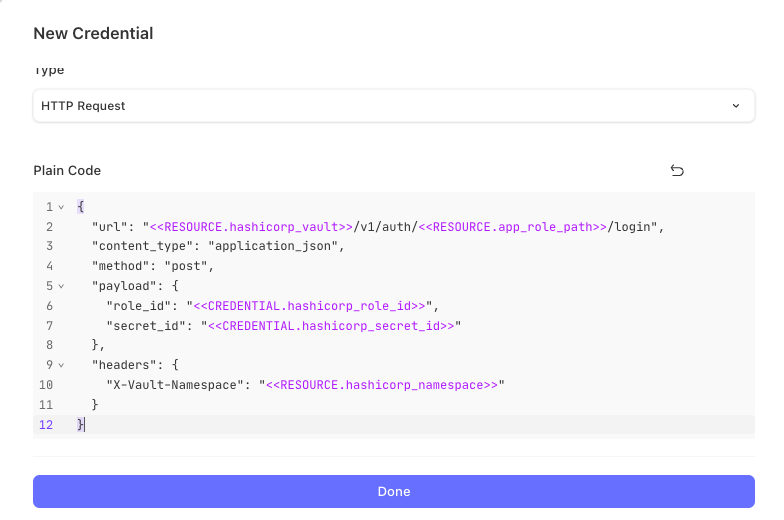
When you select Done, the credential is created with the expected configuration.
Part two: Retrieve Vault Secret
After successfully creating an HTTP credential to authenticate to HashiCorp Vault, you will need to configure an HTTP request credential to retrieve the specific Vault Secret for your application.
Before configuring the credential HTTP request, create two additional Tines resources following the same steps above. The two resources will contain:
The name of the Vault Secrets Engine that your secret resides in
The name of the secret you want Tines to utilize
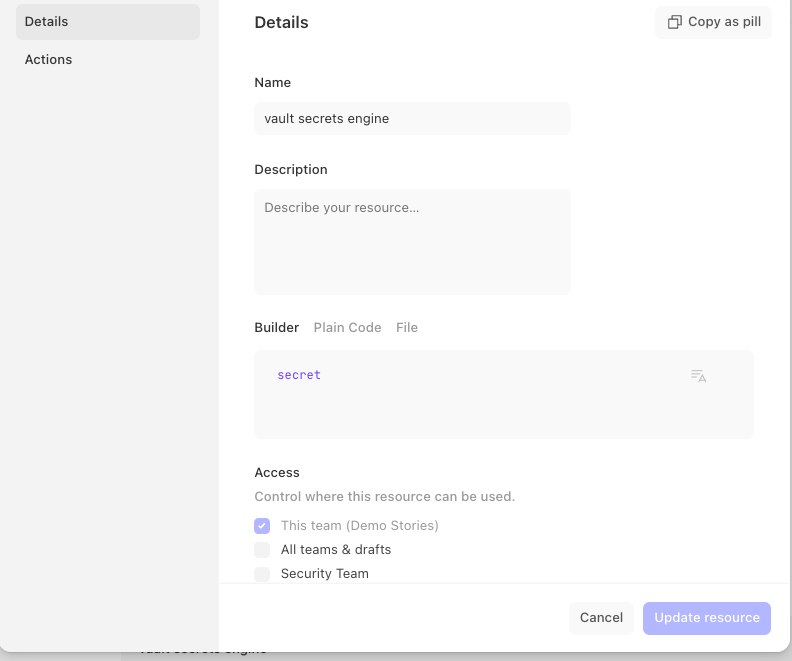
Configure the HTTP credential
Now, you're ready to create your HTTP credential for the secret you require.
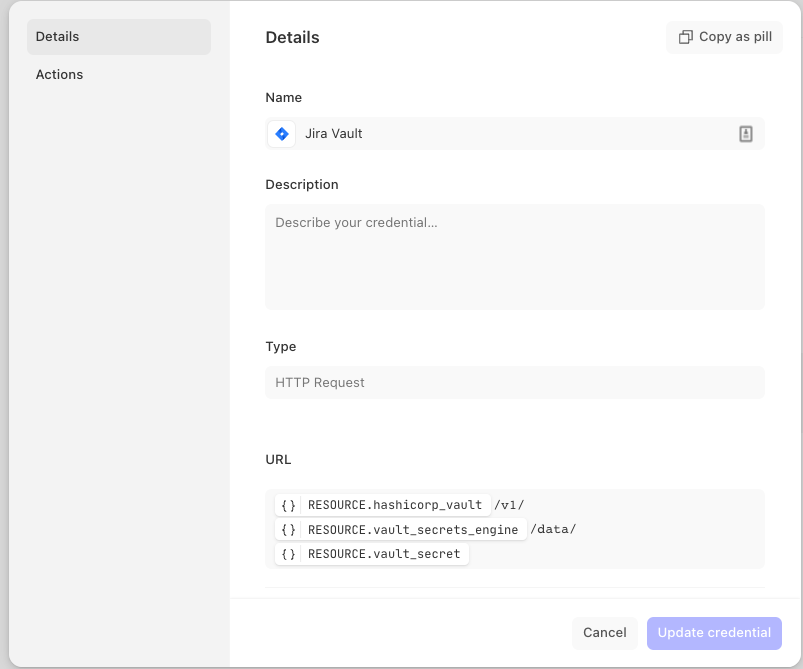
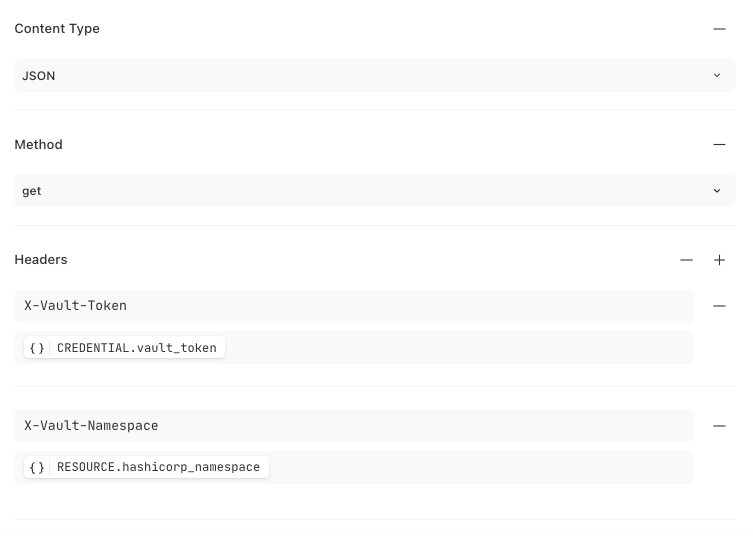
Ensure that the content-type, method, and headers are configured to match the example below.
Content type:
JSONMethod:
getHeaders:
X-Vault-Token {}
CREDENTIALS.vault_tokenX-Vault-Namespace {} RESOURCE.hashicorp_namespace
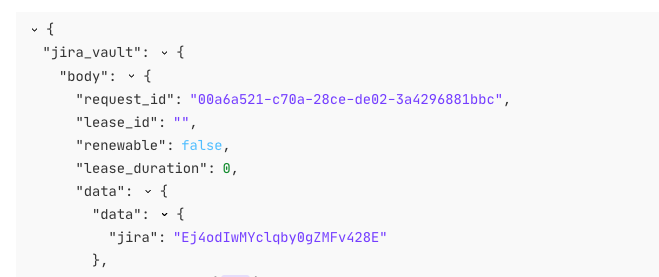
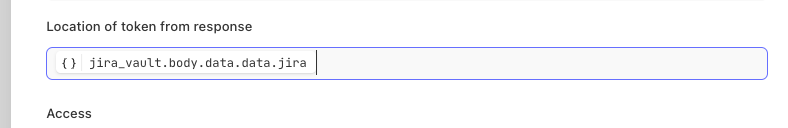
Similar to part 1, select Run Options to allow the HTTP credential to authenticate to your Vault and return the secret data you request. Double-click the specific JSON object key that returned the secret data. Paste this value into the token's location from response to allow the credential to store the returned token data.
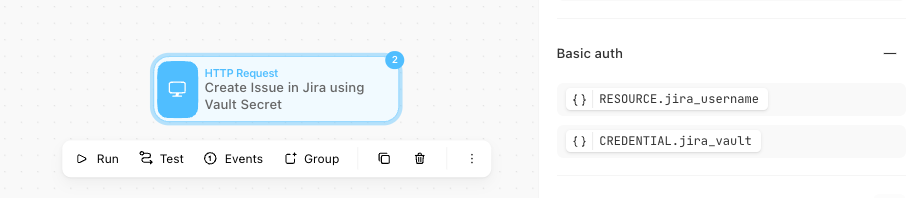
With your AppRole authentication and secret authentication configured, you can utilize your Vault credential in your Tines Stories. When you configure Actions in Tines to leverage your Vault credential connection, the appropriate secret will be pulled into the Actions and used as part of the successful API call.
Example:
When creating a new credential to retrieve your Vault secret you can use the example below.
{
"url": "<<RESOURCE.hashicorp_vault>>/v1/<<RESOURCE.vault_secrets_engine>>/data/<<RESOURCE.vault_secret>>",
"content_type": "application_json",
"method": "get",
"headers": {
"X-Vault-Token": "<<CREDENTIAL.vault_token>>",
"X-Vault-Namespace": "<<RESOURCE.hashicorp_namespace>>"
}
}Paste the contents of the code block into the Credential Editor Plain Code field as referenced previously.
NOTE: Ensure the resources and credentials referenced within the plain code match the names of the resources and credentials you previously created for objects such as the role ID and secret ID. You will also still need to set the location of the token response field.