What Should I Automate First?
At Tines, we pride ourselves on having developed a Security Orchestration Automation and Response platform that’s easy for any analyst to use, even with no coding experience, and which operates with every API using Direct Integration. We also assign every new customer a dedicated Customer Success Representative to provide Security Automation training for your team.
Not all SOAR platform deployments are a success, however, as without help or training, engineers and analysts can get stuck developing over-complicated response stories. Other teams find their SOAR platform can lack the pre-built integrations necessary to make their implementation successful. And even more teams just don’t know where to get started.
The question needs to be asked- if you’re trialing a Security Automation platform, what should you automate first?
Where are you spending your time?
The quickest way to decide what to automate first is to ask your analysts what tasks they’re spending the most time on. With 79% of security teams overwhelmed by the number of security alerts [0] we predict you’ll hear about the challenges of time-consuming investigations involving dozens of manual steps and where a high percentage of incidents are false positives.
The most frequent answers to this question that we hear are:
Processing employee or customer Abuse Inbox reports
Running, and analyzing the results of, vulnerability scans
Triaging low-level security incidents like adware
Gathering contextual information for alerts for noisy detections like
Data Loss Prevention alerts
Live off the land tool use
Suspicious login events
Brute force access attempts etc.
On-boarding and off-boarding users
Processing ticket escalations from VIPs
Standardizing or synchronizing ticket information in Case Management Systems
Reviewing phishing page visits or CEO Fraud
Writing incident notes and shift handovers
While none of these tasks are particularly complex, they all have several things in common – they’re frequent, they’re time-consuming and they’re not interesting cases for your analysts and engineers. Above all, security professionals have known for years what steps should be taken to investigate them, but until now they weren’t able to automate those steps.
Using the Tines Security Orchestration and Automation Platform there are a few immediate use cases teams can automate to take the pain out of dealing with these common incidents.
1. Deduplicate Alerts
Alerts are noisy, and even with the best tuning, your teams may still see the same alert pop up over and over again causing alert overload. It could be an alert for Powershell encoded command use by a user in Product Operations, a payroll analyst sending bank account details to an external email address, or a Business Intelligence team member exporting a large number of rows from a CRM tool triggering a DLP event. These incidents are easy to handle but still take time to review. With Security Automation platforms like Tines, it’s simple for analysts to create Stories to deduplicate incidents against multiple fields.
In the example below, we deduplicate alerts using an “Event Transformation Action” in Tines on the fields “Hostname” and “IOC Value” emitted from the “explode EDR alerts array” Action. This deduplication flow means the same indicator won’t alert on the same machine twice. Using a security automation platform to automate these steps helps minimize alert overload and, above all, helps keep your analysts focused on higher impact engineering efforts.
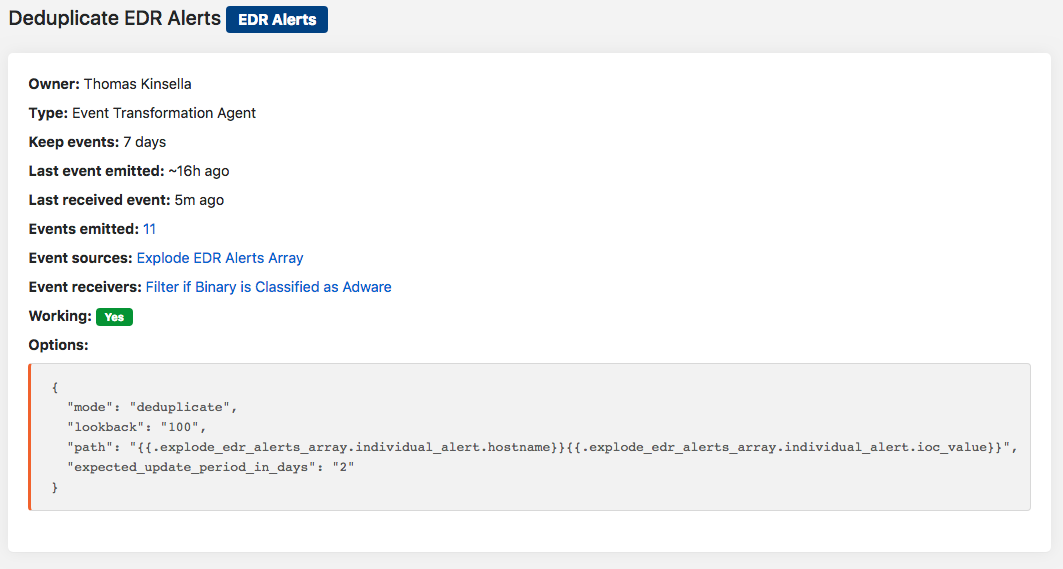
Security Automation Agent Configuration
An Event Transformation Action set up to Deduplicate alerts
2. Enrich & Provide Context
Reducing the meantime to action an alert is a key metric for any security team. Additional context helps analysts determine whether the incident is truly bad, a false positive, or something in between. For example, enriching suspicious login events with threat intelligence, researching when a domain was registered, running malware in a sandbox for additional analysis, or performing real-time analysis on a URL are all actions that can be automated with Security Automation platforms like Tines and included up-front in an incident ticket.
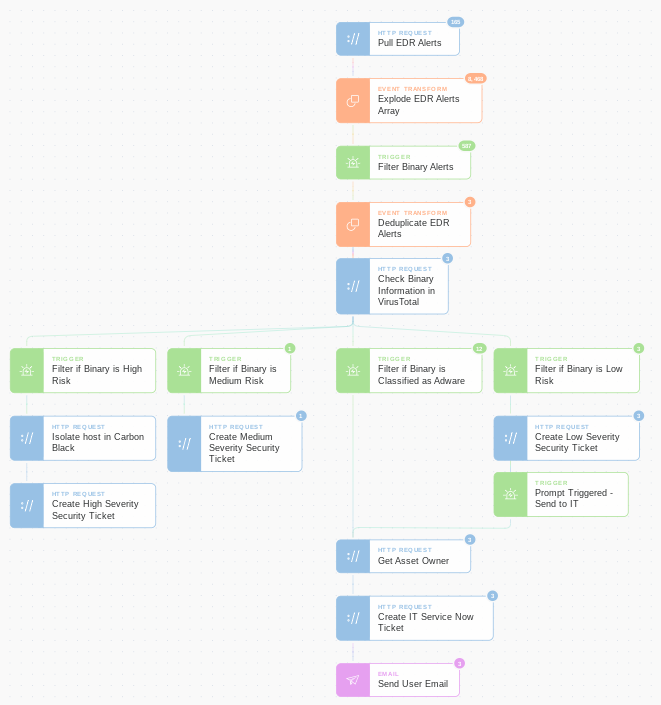
A good example of a simple enrichment flow that can be automated immediately (read more about it here) is a suspicious binary download detected by your Anti Virus, Firewall, or EDR tool. With Tines, it’s very simple for analysts to create a flow to first deduplicate and then enrich detections with binary information (from VirusTotal or elsewhere) to see exactly how dangerous the binary is and to take the workload off analysts if they’re classified as Unwanted or Adware. If the binary is classified as adware then Tines can automatically send the incident details to IT for remediation. Using this method we have seen analysts, with no coding background, automate a process in just a few hours that immediately freed up 10-20% of their time.
3. Correlate Alerts
Differentiating between legitimate and illegitimate detections for commonly used tools can be both hard and time-consuming. Alerts for a macro being run in Office, PII being downloaded from a CRM or BI system, or Powershell being used can differ dramatically in severity based on who the user is, but writing hard rules for this is difficult. Often the first thing an analyst does when investigating an alert is search in internal tools for additional context:
Who owns an asset
what’s their job title
where are they based
how long have they been with the company
has this user done anything like this before
have we seen an alert on this device recently
With Tines, it’s possible to include this information directly in an alert ticket by correlating alert information with particulars found in other tools. By giving this information to your analysts you empower them to quickly make a decision on an incident.
Using a SOAR platform like Tines to enrich AntiVirus, EDR, DLP, firewall, and other alerts with asset owner information, user role, user location, and correlating with previous alerts (for example, has an alert fired for this hostname in the past 24 hours) can reduce the time needed for an analyst to triage and make a determination on the severity of an incident. In addition, automating the process reduces the chances of responders making simple mistakes during the investigation.
4. Supercharge Responses with Prompts
Once responders have enough information to triage an incident the next steps are to contain, eradicate and recover. This remediation can involve dozens of different individual steps for an analyst, but for many incidents there are a few common steps that can be automated using a SOAR platform like Tines – isolating machines, blocking domains, resetting passwords, sending a machine for forensics, replying to an end-user’s email, etc.
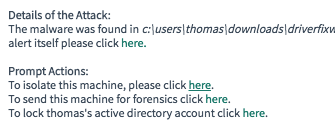
Security Automation Prompts
Prompt Actions within a ticket allow analysts to instantly isolate a machine or lock an account
With Tines’ “Prompts” feature we enable responders to automatically take an action in any workflow by simply clicking a link. These Prompts can be launched from anywhere, for example in an incident ticket, in a text or email, in Slack, etc. They allow analysts to take the next step in an investigation without opening up different tools, contacting other teams, or leaving their environment. When a responder clicks a “Prompt” this re-releases an event in Tines and sends it down a new remediation workflow. These prompts super-charge analysts' responses.
5. Crowdsource Suspicious Activity
With an ever-increasing number of security tools, new attacks, and alerts it’s hard to quickly respond to every incident. To combat this, many teams begin turning off noisier or lower-fidelity detections regardless of how useful they might be. Using Security Orchestration and Automation platforms like Tines it’s possible instead to “crowdsource” noisy alerts and activity.

A crowdsourced security automation alert
A crowdsourced suspicious VPN login alert
For example, as a small security team (or small company) with just a few security tools, it’s possible to investigate every suspicious VPN login or contact every new user provisioned export rights or admin rights. As the team expands and builds out higher-fidelity detections, however, these alerts become noisier and the ratio of true to false positive means it’s not practicable to follow up with all of them. Instead of turning off these alerts Tines takes these incidents, enriches them, and allows users themselves to detect potentially malicious activity.
Examples of crowdsourced reports include users:
logging in from a new location for the first time
provisioned new access rights
downloading large amounts of PII
requesting a new VPN token
changing payment details in their Payroll
visiting suspicious websites
uploading or downloading a large number of files
By crowdsourcing these alerts, Tines customers can quickly find true positives among the noise. Read our blogs on how to set up chatbots in Microsoft Teams and Slack for more information.
Take a look at this Cybernews interview with our CEO, Eoin Hinchy, about the future of cybersecurity and automation and how Tines will grow with these changes.
*Please note since the time of writing we have updated our terminology. Our "agents" are now known as "Actions," but some visuals might not reflect this.*