One morning, a couple of years ago, while I was working as an analyst for a managed security services provider (MSSP), the SIEM I was using filled up with network traffic hits related to a new high severity "Common Vulnerabilities and Exposures" (CVE) with exploit attempts coming from all over the Internet.
Instead of instantly hitting the panic button, I decided to try out a new service I had recently heard of called GreyNoise. GreyNoise was promising to be a catalog of all scanning services on the Internet, both malicious and benign. I took my list of IPs, ran them through, and saw there was not a known malicious threat source in the bunch. All IP addresses were clearly identified as major services like Shodan.io or other Internet scanners. I could move on with confidence, and I also had hard evidence that named organizations were looking for these vulnerabilities, which allowed me to prioritize the patching to teams more effectively.
Before GreyNoise, a situation like the above would have left me digging through web server logs, analyzing brand new exploits to see if they had been successfully executed, and attributing the traffic to some entity looking to harm the organization. In the past, only some of the most mature cybersecurity teams might have kept a list of known or frequent IPs (which was probably only a result of running "WHOIS" repeatedly). GreyNoise has collected and curated all this data in one place, extending and improving knowledge for teams that would otherwise be draining valuable hours researching for potentially ineffective outcomes.
Not only does the free GreyNoise Visualizer provide a graphic representation of this invaluable knowledge, but GreyNoise offers easy access to its APIs for programmers to make the most of its data sets. By using GreyNoise and Tines together, cybersecurity teams can gain back some power from one of the loudest, busiest parts of a security operations center (SOC).
W(T)AF Alerts
The most frustrating types of alerts that a cybersecurity team will deal with are often the alerts from a Web Application Firewall (WAF). Factors contributing to the frustration are not only the alerts themselves but also the management of the WAF service.
These factors include but are not limited to:
The nearly unlimited amounts of detection tuning required
Complications with application owners when signatures match expected traffic patterns
The ability for anyone on the Internet to have a direct impact on the number of alerts your team experiences
By using GreyNoise to enrich WAF alerts in Tines, teams can begin to take some of the power back. To do this, for each alert that comes in, look up the IP in GreyNoise to understand if and how they have classified the IP.
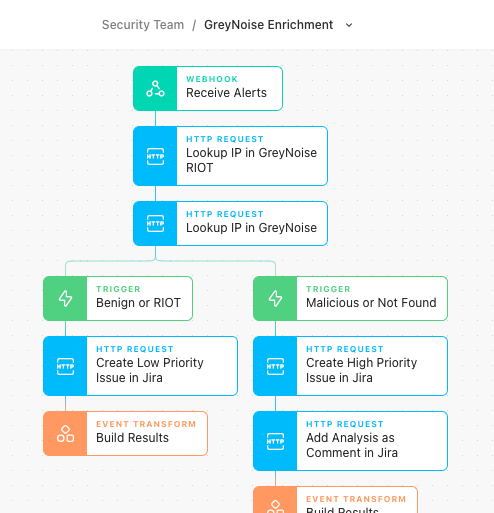
This flow takes advantage of two separate service endpoints GreyNoise offers: RIOT and Noise IP lookups. RIOT stands for "Rule It OuT", a service that provides a curated insight into known Internet services such as Google DNS, AWS Cloudfront, and Fastly. RIOT further breaks down this classification into two separate trust levels:
Trustworthy because the companies or services assigned are generally responsible for the interactions with this IP.
Somewhat trustworthy because they are necessary for regular and common business internet use.
Simply put, if an IP is classified in RIOT and has a trustworthy confidence level, the impact of the alert is very likely to be minimal, and it can be set as a low priority or closed immediately. Suppose the IP has a somewhat trustworthy confidence level. In that case, the priority could be raised, and/or additional risk factors could be added in to arrive at a confident automated determination of the status of the alert before any analyst review.
The other GreyNoise API is the Noise Lookup service. The Noise Lookup provides context data around mass-internet scanning activity collected by the GreyNoise sensor network. The Noise Lookup service provides further context around the IP as well as a current classification of the IP. While the data provided by the lookup can be incredibly interesting, getting no results can be even more fascinating. GreyNoise is present all over the Internet, just waiting for people to scan the whole Internet or even parts of it looking for easy victims. If your WAF sees activity from an IP that GreyNoise has never seen before, there is a chance that the activity seen was a direct, purposeful, and targeted scan or exploit attempt against specific assets. In a situation where there is a malicious classification or no known data points, a higher priority and enriched investigation can be carried out.
Blocking Active CVEs
Perhaps a specific CVE had just been released, and there is a mad scramble to find a patch or apply mitigating factors. Vendor patches seem to be running behind while the attackers have the advantage. Instead of applying a vendor-specific signature, patch, or other mitigation, what if the opportunistic attackers were just... blocked.
The GreyNoise team spends countless hours performing the task of analyzing and classifying new traffic patterns on the Internet. As a result, GreyNoise sees which CVEs are being actively exploited in the wild. Not only are they some of the first on the scene to classify and tag new attacks as they occur, but they also keep on top of older exploits with elevated scanning profiles.
These CVEs and tags are usable in the GreyNoise visualizer, but they are also available to be searched programmatically via the GreyNoise API using a searching endpoint and the GreyNoise Query Language (GNQL). CVEs can be searched like cve:CVE-2021-26855 (Exchange ProxyLogon exploit attempts), and an example of search by tags can be seen in the tweet above.
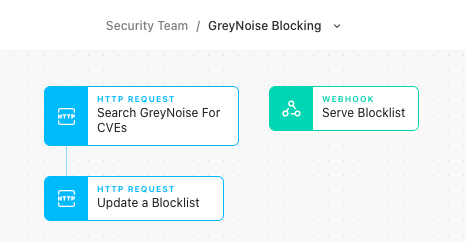
Once GreyNoise has classified the traffic, a routine scheduled GNQL search can be done in Tines, which looks for all IPs performing scanning or exploitation behaviors. With that list of known IP addresses, Tines can update a firewall or WAF rule to block traffic from classified sources. Alternatively, Tines webhooks can be used to serve as a dynamically updated list of IP addresses that those firewalls can pull in dynamic objects from.
Are We The Baddies?
In a team's day-to-day, handling alerts and blocking IP addresses might be standard procedures. On the off chance, though, what if your assets end up scanning the internet and start getting picked up by GreyNoise?
There is likely a bronze-hued plaque somewhere featuring the cybersecurity truism that a good program requires comprehensive asset management. It is hard to argue with, but it is much more difficult to achieve than just saying the words. Even with new asset management capabilities built into cloud providers, security teams sometimes have few options to get ahead of the business machine when spinning up "critical" new applications or a shadow IT WordPress site with just enough connection business assets.
If or when those assets are compromised, some attackers have been known to use their newfound machines as pivot points for additional discrete scanning of the Internet and exploitation. GreyNoise will classify this scanning activity, and with an owned ASN or known list of IPs, defenders can gain visibility into a compromise that otherwise would have been incredibly difficult to detect.
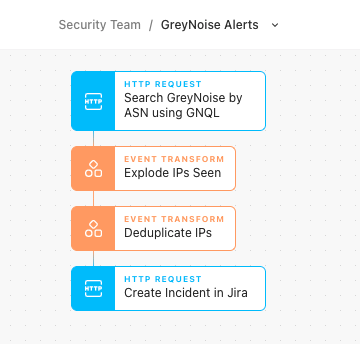
GreyNoise offers these notifications as email alerts which can be signed up for here. If instead, you would like more flexibility or automation in regards to the alert, use Tines to schedule another GNQL query looking for specific ASNs or IP ranges. In the example Story above, once the query has been made, IPs will get deduplicated from previous calls, and only if a new IP shows up will a new incident instantly get created for an analyst to dig into.
A Little Bit Louder Now
GreyNoise is a tool in a class of its own and I hope in reviewing some of these use cases you may have gained a new perspective on cybersecurity as I did way back. Using Tines and GreyNoise together opens up even more possibilities to not only handle your noisiest alerts but also respond to threats to your organization.
Download and customize GreyNoise automation workflows from the Tines Story Library.
Loading story...