We’ve written many blogs about how to analyze suspicious emails, attachments, urls, even email headers. However there is a consistent question prospects ask about analyzing emails – how does Tines automate the analysis of .eml files?
EML files are files that contain the raw contents of an email saved by email programs like Microsoft Outlook. Phish reporting tools like KnowBe4’s ‘Phish Alert’, Cofense’s PhishMe or the report phishing button in Outlook send suspicious emails as .eml attachments to companies’ abuse inboxes like those reported to phish.ly. These .eml attachments contain the content of the reported email, along with the message headers; the subject; sender; all the recipients; and other metadata about the email. EML files may themselves also store one or more email attachments, and even other .eml files.
EML files can’t be analyzed in a sandbox nor can we easily extract attachments or email headers from them. In order to analyze these files, we must extract the raw data and analyze the email as a whole.
The EML Parse Liquid Filter
To solve this problem at Tines we built a liquid filter, eml_parse, which extracts all the email data from an .eml file in a structured format. The liquid filters extract the attached .eml’s sender, body, attachments, headers, etc. Tines can then analyze the email in the same way as an email sent to an abuse inbox.
To use eml_parse is simple – take the base64 encoded contents of an attachment (or an eml file submitted manually to Tines or downloaded from elsewhere) and then use the eml_parse liquid filter together with the as_object liquid filter. An event transformation Action with the below code will take the eml file and decode it:
{
"mode": "message_only",
"message": "{{.path_to.eml_attachment.base64encodedcontents | base64url_decode | eml_parse | as_object}}"
}The output will look exactly like a normal email:
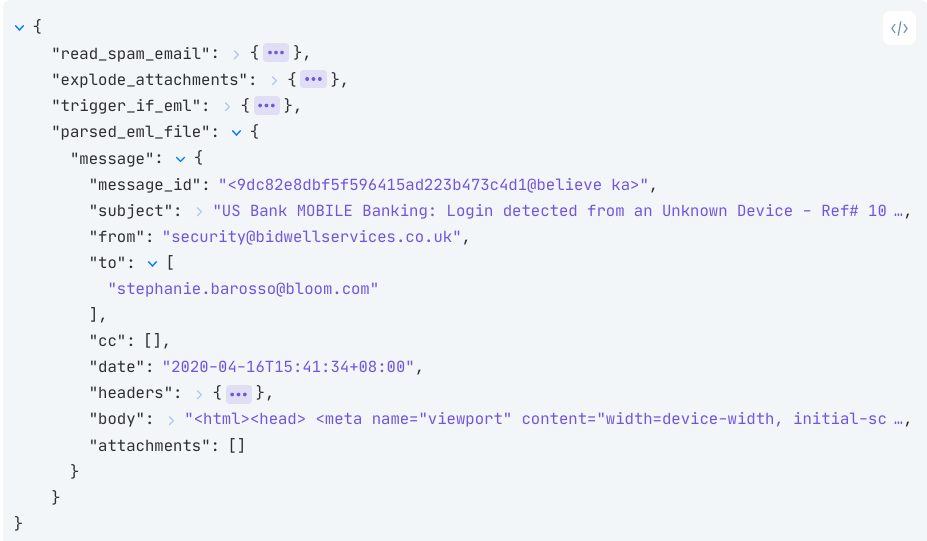
Recursive Analysis of EML Files
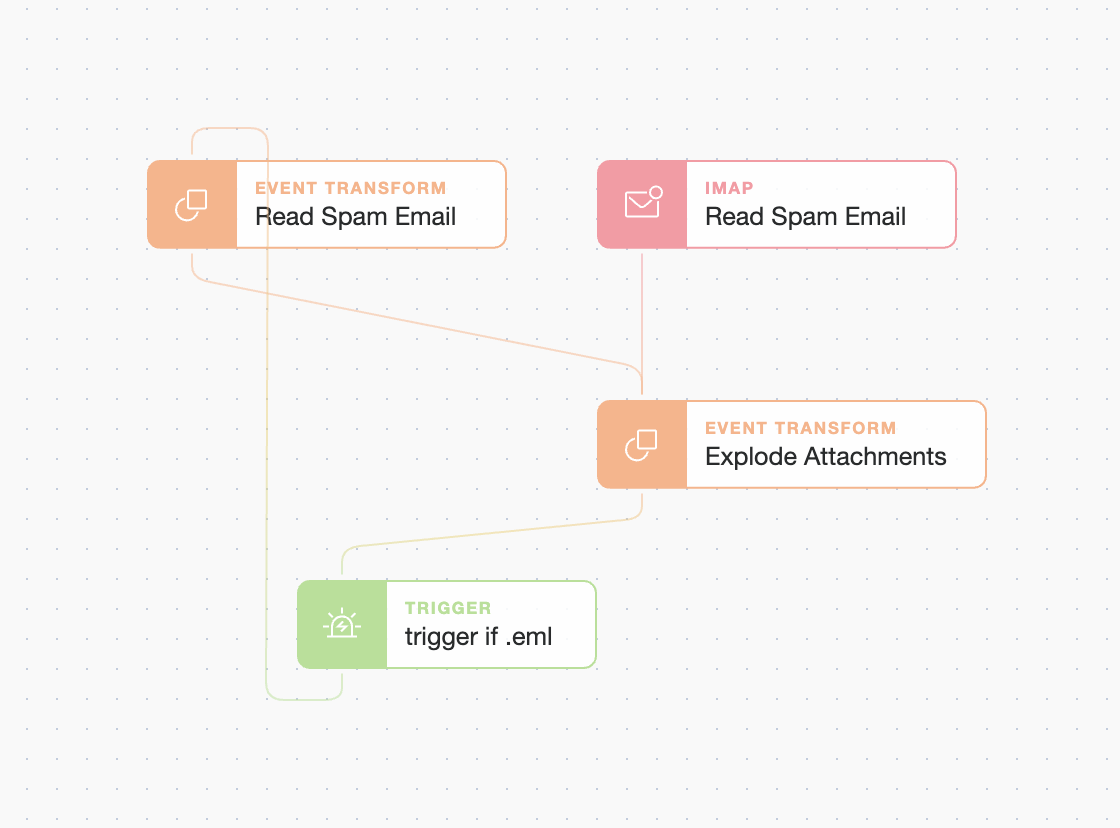
The beginning of a basic Tines Story with recursive email analysis is below. EML attachments will be analyzed recursively by naming the Event Transformation Action the same name as the IMAP Action:
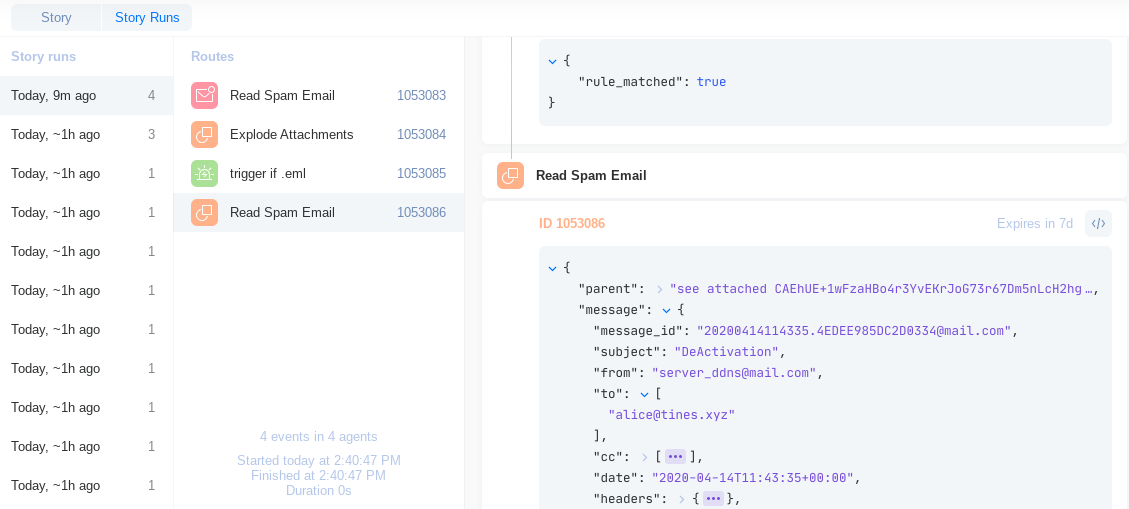
When we view the event in Story Runs we can see that we successfully extracted the attached email:
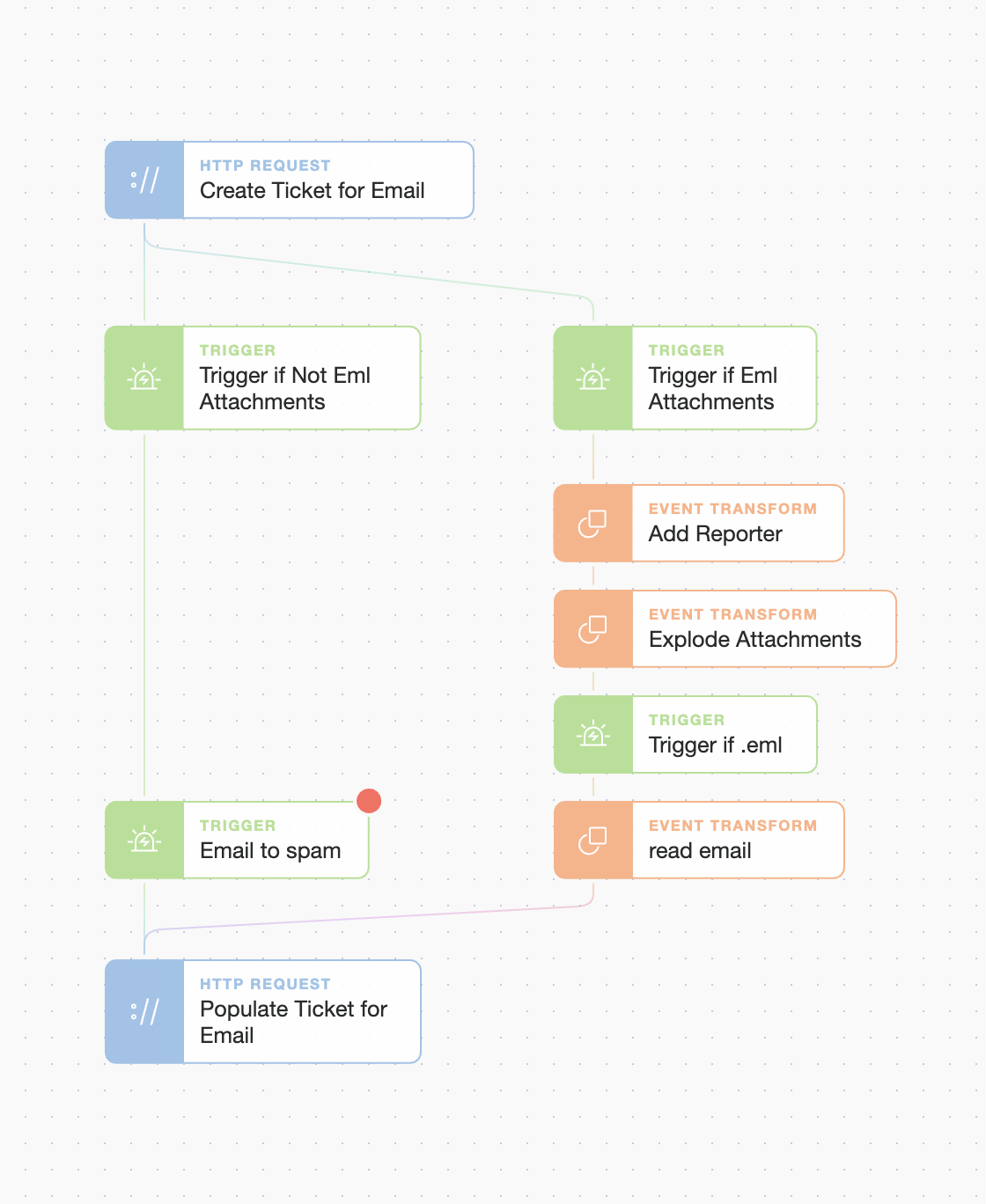
Now that we know we can analyze any .eml attachments we can include this process as part of any phishing analysis story easily, for example using Gmail to handle reports with multiple or no eml attachments:
Using this method you now have a simple process to automate the analysis of .eml files reported by your employees using your phish reporting tool. You can now analyze the email and its attachments using all of your favorite tools!
*Please note we recently updated our terminology. Our "agents" are now known as "actions," but some visuals might not reflect this.*